In-brief: the U.S. healthcare sector is in critical condition and needs urgent, coordinated action to protect patient safety and address vulnerabilities in millions of deployed medical devices, a Congressional Task Force has concluded. (Updated with comments from Joshua Corman of Atlantic Council. PFR June 7, 2017)
The healthcare sector in the U.S. is in critical condition and in dire need of an overhaul to address widespread and systemic information security weakness that puts patient privacy and even safety at risk, Congressional Task Force has concluded.
The report, released to members of both the U.S. Senate and House of Representatives on Friday concludes that the U.S. healthcare system is plagued by weaknesses, from the leadership and governance of information security within healthcare organizations, to the security of medical devices and medical laboratories to hiring and user awareness. Many of the risks directly affect patient safety, the group found. It comes amid growing threats to healthcare organizations, including a ransomware outbreak that affected scores of hospitals in the United Kingdom.
The final report by the Health Care Industry Cybersecurity Task Force [PDF] is a call to arms for the healthcare sector, featuring more than 30 pages of recommendations and “imperatives,” some of which are bound to be the source of controversy. Among other things, the report calls for the creation of a leader role within the Department of Health and Human Services (HHS) focused on cyber security.
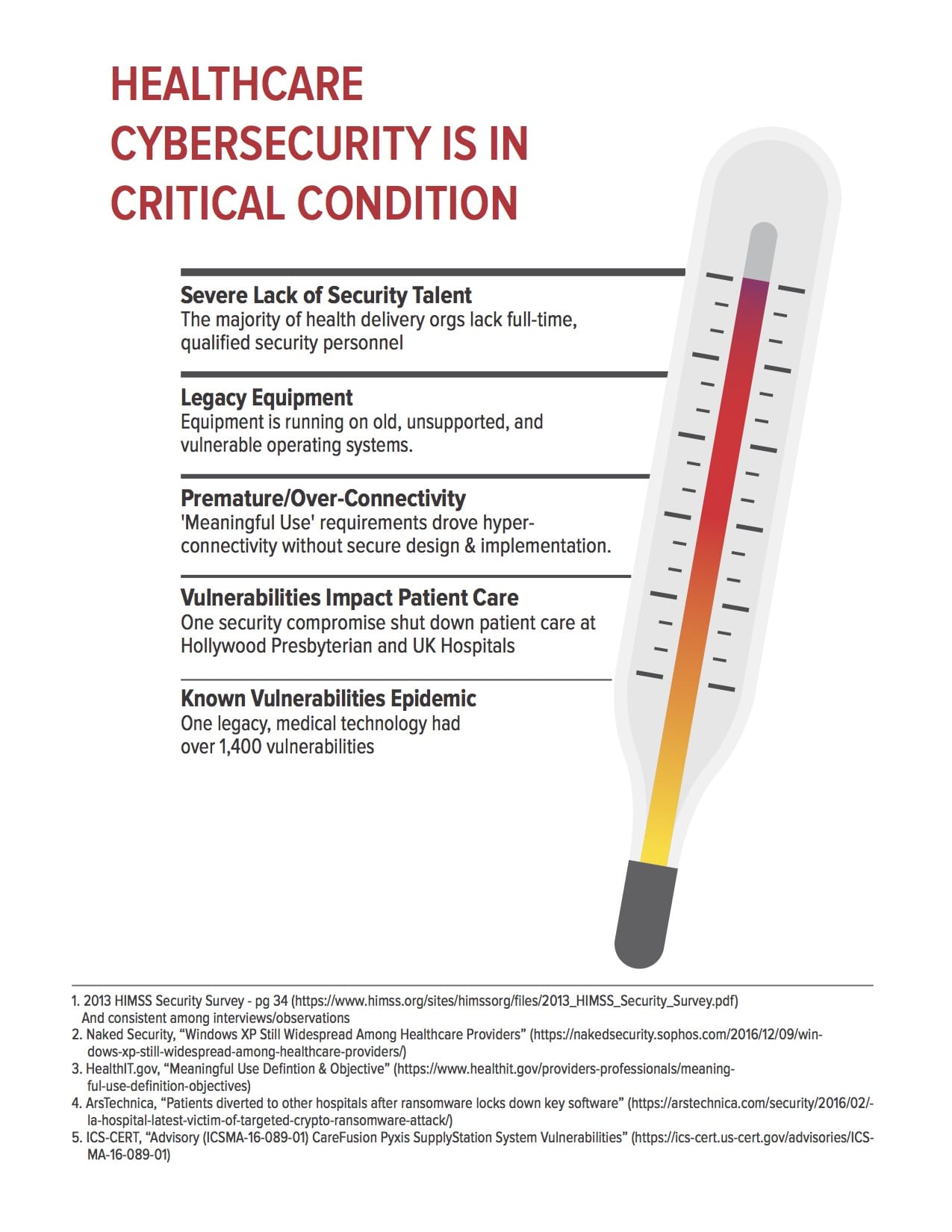
On the controversial issue of medical device security, the report suggests that the Federal government and industry might use incentives akin to the “cash for clunkers” car buyback program to encourage healthcare organizations to jettison insecure, legacy medical equipment. Medical device makers need to do a far better job designing products in line with accepted secure development practices and should be urged to publish a “bill of materials” with medical devices that accounts for all hardware and software used in a device, including open source software components.
Incidents like the WannaCry outbreak, which disrupted the delivery of medical care at scores of UK National Health Service facilities are shots over the bow, warning of what could be far more disruptive and widespread attacks said Joshua Corman, the Director of the Cyber Statecraft Initiative at The Atlantic Council and a founder of the group I Am The Cavalry.
Healthcare organizations rely heavily on connected medical devices, but most are small and cash strapped organizations that lack expertise in information security.
“Healthcare is target rich and resource poor,” Corman notes, adding that Internet connected healthcare equipment can’t be used irrespective of security and privacy concerns. “If you can’t afford to protect it, you can’t afford to connect it,” Corman said.
The Task Force was established by Congress with the passage of the Cybersecurity Act of 2015 to study the challenge of securing the healthcare industry from cyber attacks. It counts representatives from both private sector and public sector organizations as members, including the Chief Information Security Officer for the Centers for Medicare and Medicaid Services at the U.S. Department of Health and Human Services, the CIO of Cook Children’s Health Care System, the Chief Technology Risk Officer of insurer Kaiser Permanent and representatives from testing organization Underwriters Lab and security companies including Symantec and FireEye.
The report was released to the Chairs of leading House and Senate Committees that oversee the healthcare and information technology sectors. Among them: Senator Lamar Alexander, the Chairman of the Senate Committee on Health, Education, Labor, and Pensions, Representative Greg Walden, the Chairman of the House Committee on Energy and Commerce, Senator Ron Johnson the Chairman of the U.S. Senate Committee on Homeland Security and Government Affairs.
The report describes the U.S. healthcare system as a “mosaic” of large health systems, single physician practices, public and private payers, research institutions, medical device and software companies, the U.S. healthcare sector services a diverse and widespread patient population, often through small practices and rural hospitals. The complexity of the system introduces risk and complicates the job of establishing comprehensive cyber security standards.
In other areas, federal regulations like the Affordable Care Act’s emphasis on electronic health record systems have increased risks by consolidating information from multiple health providers and networks on a single, cloud based system. Further mandates will add programmatic access to that data in ways that can increase patients access to their data, but that will also introduce risks that are difficult to measure and that have yet to be fully appreciated, the report notes.
FDA approval of medical devices can take six years or more, while devices have useful lives that may be measured in decades. Still, support by vendors like Microsoft, whose software is used to manage medical equipment, ends at around the eight year mark after initial release, resulting in products that are unsupported for much of their useful life, Corman notes.
“Cyber issues have been around for many decades now, but the nature of the attacks and tools used has changed rapidly,” Anura Fernando, the Principal Engineer for Medical Systems Interoperability & Security at Underwriters Laboratories told The Security Ledger. “It has put us in a situation where we do not have the breadth of skills to deal with this niche area of cyber security.”
Corman of The Atlantic Council agreed, noting that healthcare organizations have quickly become a preferred target for cyber criminals and nation state actors. “Healthcare organizations have always been prey, but there wasn’t sufficient interesting from predators. Those days are over,” he said.
In addition to understanding general purpose computing and information security, healthcare cyber security demands clinical domain expertise that encompasses the risk to patients and the purpose and functioning of medical devices, said Fernando, who was a Task Force member. The report calls on the public and private sector to partner in areas like accreditation and certification for what’s termed “cybersecurity hygiene.” Regulatory agencies could then rely on those private sector partners to test, validate and certify medical devices and other technology, Fernando said. Some recommendations – fairly tactical.
The report comes amidst a dawning recognition that the nation’s biomedical infrastructure is highly connected and vulnerable, said Dale Nordenberg, the Executive Director of the Medical Device Innovation, Safety and Security Consortium.
Nordenberg has been working to raise awareness about cyber risk in the medical field for years but said that recognition within healthcare organizations, among medical device makers and in academic and policy circles was slow. “These are the unintended consequences of emerging technology,” Nordenberg said. “We didn’t anticipate the interface between cyber and human risk…or at least not with significant cognition to take action.”
Delays in recognizing the risks posed by connected devices has created the current state of affairs with tens of millions of connected, but vulnerable devices. “We’re starting from the point where we already have a lot of work to do,” he said.
Nordenberg said the recommendations of the report underscore the need for what he called a “significant mobilization of resources” that stretches across different industry sectors. Priority should be given to areas that directly affect patient security and safety, he said. “This isn’t about the device. It’s about the patient and populations,” he said.
That said, flaws in medical devices and the software that supports them presents one of the clearest risks to patient safety. An analysis by the Task Force of what the report calls a typical healthcare “value chain” identified 151 potential risks, ranging from loss of patient confidentiality to risks to patient safety. Laboratories, patient service centers and medical devices and equipment accounted for the bulk of 23 identified risks to patient safety. Risks included the loss or modification of data, disruption of systems or processes, and asset loss or disruption due to software vulnerabilities, the Task Force concluded.
Recent evidence supports that notion. Recent research by the firm Whitescope found thousands of vulnerabilities in the hardware and software for implantable cardiac devices manufactured by four, different vendors. Those design flaws, including the use of permanent (or “hard-coded”) user credentials and insecure communications could be used to interfere with the functioning of a device, or provide attackers access to other, privileged systems on a medical network, the firm concluded.
That followed a 2016 report by the firm MedSec released a report on vulnerabilities in devices manufactured by St. Jude Medical. A subsequent report by the U.S. Food and Drug Administration (FDA), released in April, found that St. Jude Medical knew about serious security flaws in its implantable medical devices as early as 2014, but failed to address them with software updates or other mitigations, or by replacing those devices.
To tackle the problem, Congress needs to take a holistic approach, notes Fernando of Underwriters Laboratories. “We’re not dealing with silo’d and vertical industries. There’s a lot of cross cutting.” Funding from the federal government won’t solve the problem alone, but federal money can promote activities that, over time, will result in public sector and industry action to improve cyber security, he said.
Download the complete report here.


Pingback: Healthcare Industry Cybersecurity Report – Cyber Security
Pingback: [Older] Update: Cash for Medical Device Clunkers? Task Force calls … | Dr. Roy Schestowitz (罗伊)