In this episode of the podcast (#235) Justine Bone, the CEO of Medsec, joins Paul to talk about cyber threats to healthcare organizations in the age of COVID. Justine’s firm works with hospitals and healthcare organizations to understand their cyber risk and defend against attacks, including ransomware.
Tag: medical devices
Episode 198: Must Hear Interviews from 2020
Trying times have a way of peeling back the curtains and seeing our world with new eyes. We
Episode 184: Project BioMed – The Fight to Repair Medical Devices
In this episode of the podcast (#184) Kyle Wiens of iFixit joins us to talk about Project BioMed: an international, crowd-sourced effort to expedite repair of medical devices by making service and repair manuals available online. In our second segment, we speak with Jonathan Krones, one of an army of volunteer engineers, archivists and librarians who took on the task of cataloguing medical device repair information.
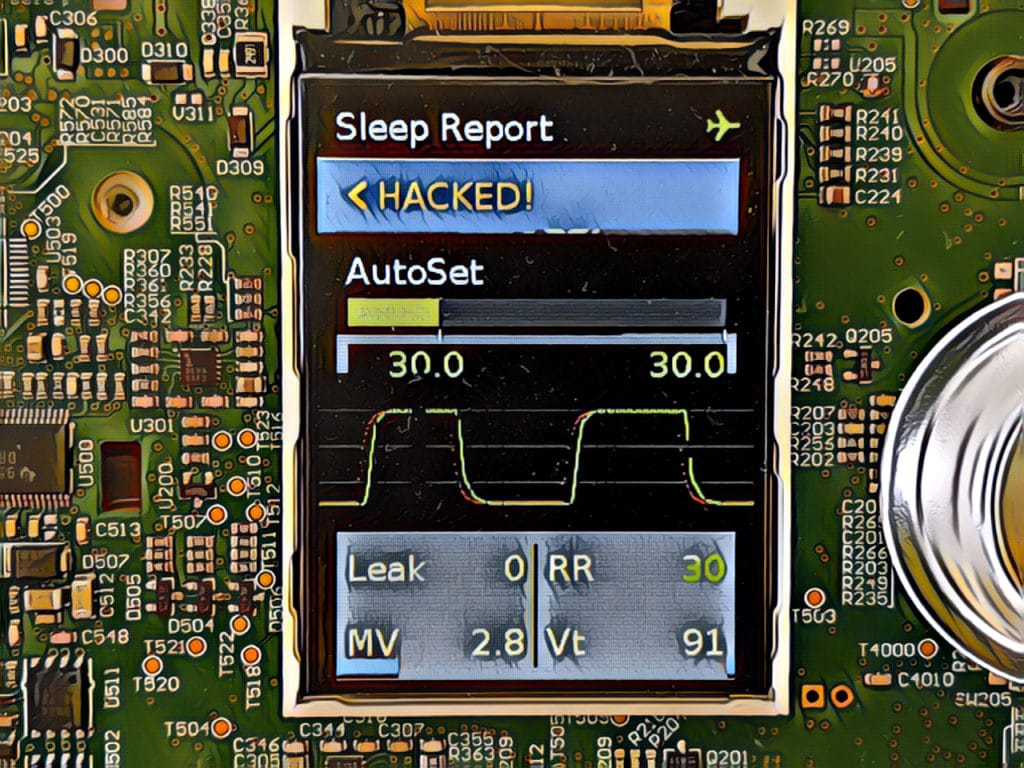
Episode 182: Hackers take Medical Devices ‘off label’ to Save Lives
In this episode of the podcast (#182) Trammell Hudson of Lower Layer Labs talks to us about Project Airbreak, his recent work to jailbreak a CPAP machines and how an NSA hacking tool helped make this inexpensive equipment usable as a makeshift respirator.
Episode 153: Hacking Anesthesia Machines and Mayors say No to Ransoms
In this week’s podcast episode (#153): The researcher who discovered serious remote access security flaws in anesthesia machines by GE says such security holes are common. Also: the US Conference of Mayors voted unanimously to swear off paying ransoms for cyber attacks. But is that a smart idea? We’re joined by Andrew Dolan of the Multi State Information Sharing and Analysis Center to talk about it.