Fresh off their discovery of a previously unknown (‘zero day’) security hole in Microsoft’s Internet Explorer web browser, researchers at the security firm Fireeye say that they have evidence that a string of sophisticated attacks have a common origin.

In a report released on Monday (PDF), the firm said that many seemingly unrelated cyber attacks identified in the last year appear to be part of a “broader offensive fueled by a shared development and logistics infrastructure” — what Fireeye terms a ‘supply chain’ for advanced persistent threat (APT) attacks.
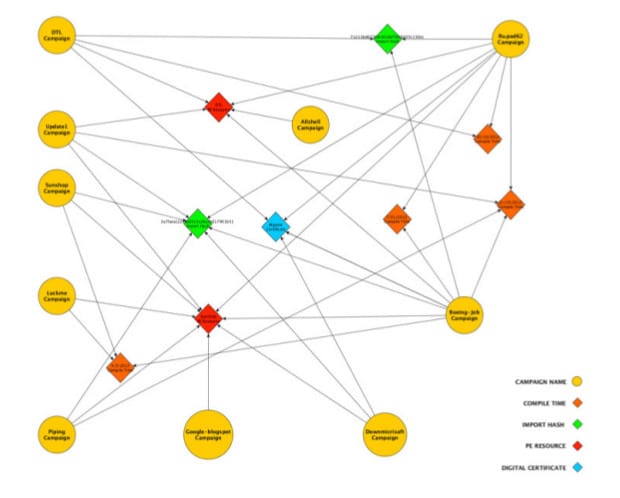
At least 11 APT campaigns targeting “a wide swath of industries” in recent months were found to be built on a the same infrastructure of malicious applications and services, including shared malware tools and malicious binaries with the same timestamps and digital certificates.
“Taken together, these commonalities point to centralized APT planning and development,” Fireeye wrote.
The attacks link at least 11 separate malware campaigns that were previously considered to be separate. They include a large operation dubbed the “Sunshop Campaign,” which Fireeye first wrote about in May of this year to other campaigns with names like “Piping,” “Luckme” and “Boeing Job.”
The company analyzed the components of those attacks and observed shared characteristics that linked them. Specifically, Fireeye believes that the malware used in the attacks are “likely the result of a set
of common ‘builders’ developed by a shared development and logistics infrastructure.”
Builders are tools that allow malware authors to mass produce variants of malicious programs. Subtly modified variants are often successful at fooling signature based anti-virus detection engines.
The 11 campaigns all used variants of the same malware families, including PoisonIvy, Gh0st, 9002 and Kaba. The variants had the same compile time and other distinguishing characteristics across campaigns. Other shared elements between the attacks include digital certificates that are used to sign malicious executables, making them look legitimate.
A factory-like malware production operation likely backs each of the campaigns, with strict separation of duties and specialization around activities like malware development, package creation, intrusion operations and command and control. “This separation of tasks is more efficient and supports a faster tempo of offensive operations,” the firm wrote.
Fireeye makes signature-less endpoint protection software and counts a number of high-profile public- and private sector firms as customers. Its researchers have been among the first to identify new attacks, including a recent round of malicious software infections that relied on the exploitation of a previously unknown Internet Explorer vulnerability.
It is not clear that the latest attacks, which made use of the Internet Explorer zero day, are also a product of the same operation.
In an interview with The Security Ledger, Fireeye’s Manager of Threat Intelligence Darien Kindlund said that his company discovered the most recent APT-style attack using the zero day Internet Explorer hole at a customer who was targeted at the tail end of what Kindlund described as a month-long attack aimed at employees of commercial firms with interests in “international security policy.” He said Fireeye documented two victim organizations and hundreds of infected endpoints, but that there were likely other victims that Fireeye was not aware of.
The company has linked the attacks to an operation it has named “Deputy Dog,” which dates to August. That attack also relied on a zero-day exploit in Internet Explorer that was used in targeted attacks against organizations in Japan and the February, 2013 attack on the U.S. security firm Bit9.
But the company isn’t ready to say whether the latest attack is linked to the same APT operation that left fingerprints on the other, eleven operations, Kindlund said.

