The question of whether or not Russia has been involved in ongoing cybercrime is on the minds of many. A new report by Analyst1 offers new intelligence on the matter.
Tag: malware
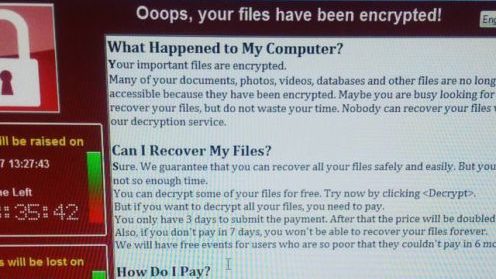
Episode 169: Ransomware comes to the Enterprise with PureLocker
In this episode of the podcast, sponsored by PureVPN, Michael Kajiloti of the firm Intezer Labs joins us to talk about the origins and makeup of PureLocker, a new family of ransomware designed to target production servers in the enterprise.
Episode 158: How NotPetya has Insurers grappling with Systemic Cyber Risk
We talk to Bruce McDonnell of the East West Institute about how insurers are responding.
Episode 155: Disinformation is a Cyber Weapon and APTs warm to Mobile Malware
In this week’s episode of the Podcast (#155): Jerome Segura of Malwarebytes joins us to talk about how disinformation campaigns and cyber crime are part of the same toxic cocktail in the world’s trouble spots, like Ukraine. Also: Adam Meyers of CrowdStrike joins us to talk about that company’s first ever report on mobile malware, which is gaining currency with advanced persistent threat (APT) groups.
Episode 153: Hacking Anesthesia Machines and Mayors say No to Ransoms
In this week’s podcast episode (#153): The researcher who discovered serious remote access security flaws in anesthesia machines by GE says such security holes are common. Also: the US Conference of Mayors voted unanimously to swear off paying ransoms for cyber attacks. But is that a smart idea? We’re joined by Andrew Dolan of the Multi State Information Sharing and Analysis Center to talk about it.