Nearly a week after Marriott disclosed a massive breach of its Starwood reservation system, customers complain that the company has not communicated with them to tell them whether they are affected. Marriott says it is sending “rolling” emails to hundreds of millions of victim
Tag: Web
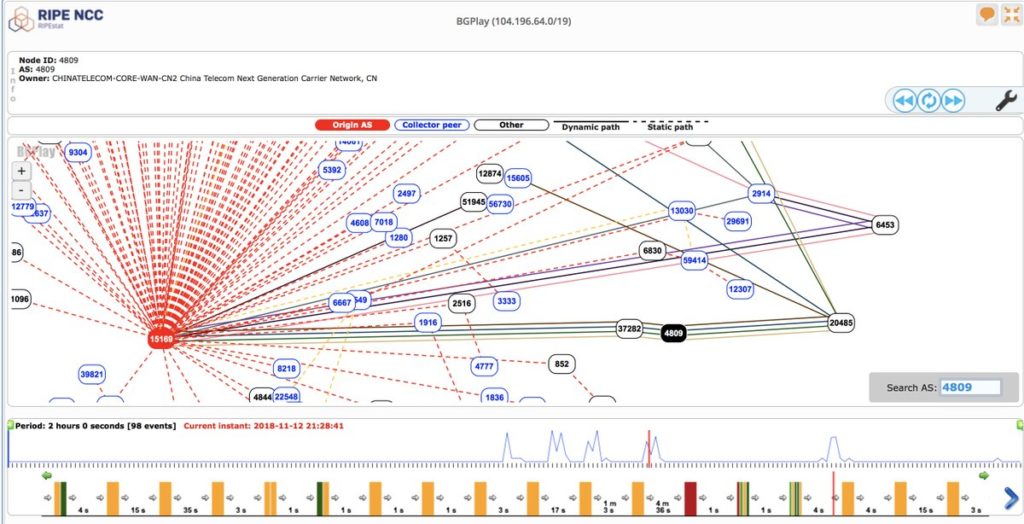
Nigerian ISP Hijacks Google Traffic, Sends It Through Russia and China
A small Nigerian Internet service provider (ISP) hijacked traffic meant for Google data centers on Monday, re-routing local traffic through China and Russia and making some hosted services temporarily unavailable for users.
Massive Facebook Breach Affects 90 Million Accounts
Facebook forced a reset of more than 50 million user accounts on Thursday and would force another 40 million account resets in the coming days, citing a major breach of the site’s security that allowed unknown attackers to take over people’s accounts.
Report: Financial industry in crosshairs of credential-stuffing botnets
Botnets mounting credential-stuffing attacks against the financial industry are on the rise, with a more than 20-percent uptick in a two-month period, a new report from Akamai has found.
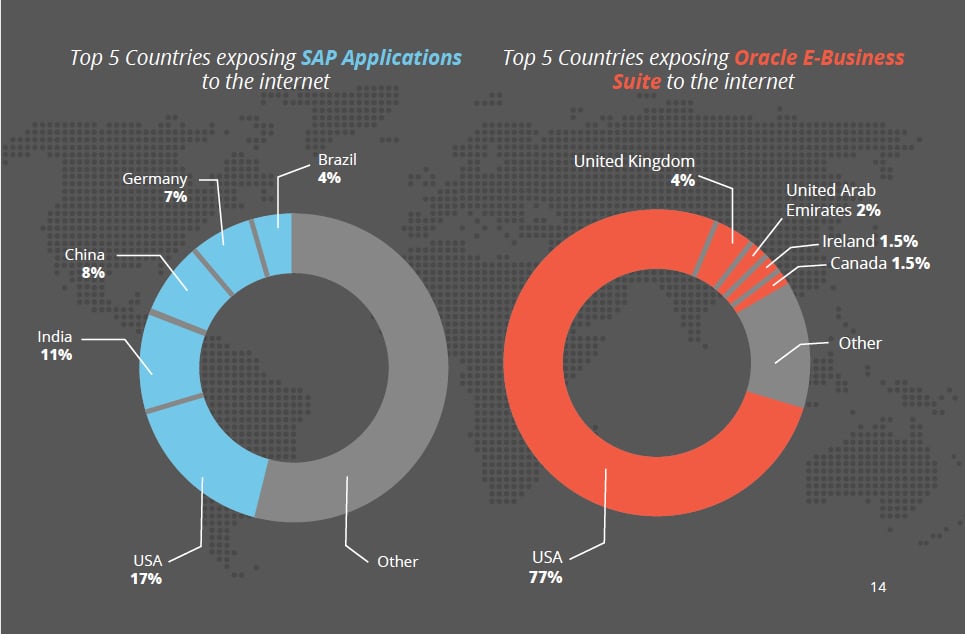
Report: Cybercriminals target difficult-to-secure ERP systems with new attacks
Cybercriminals are targeting enterprise resource planning (ERP) apps–some of the oldest and most difficult-to-secure business software systems–with new attacks in an effort to exploit vulnerabilities and gain access to valuable, sensitive enterprise data, according to a new report.