Cybercriminals are targeting enterprise resource planning (ERP) apps–some of the oldest and most difficult-to-secure business software systems–with new attacks in an effort to exploit vulnerabilities and gain access to valuable, sensitive enterprise data, according to a new report.
In the report released this week by Digital Shadows Ltd. and Onapsis Inc., researchers said they have seen a noticeable boost in attacks on ERP systems from leading vendors SAP and Oracle by hactivist groups, nation-state actors and cybercriminals that are constantly evolving to take advantage of the critical business data found within them.
Moreover, companies continue a long-time struggle to secure these systems in the threatening landscape due to their inherent complexity, the increased sophistication of threats and the larger attack surface of modern, cloud computing-based ERP systems.
ERP apps help companies manage critical business processes—such as product-lifecycle, customer-relationship and supply-chain management. This means they store and access hordes of sensitive company data, making them a treasure trove for cybercriminals aimed at using that information to disrupt critical business operations, target specific companies, and engage in cyber espionage and sabotage, according to the report.
Recently, bad actors have been upping their game, researchers found. They currently can mount attacks that can get behind company firewalls to go deeper into business networks and gain access even to internal, previously inaccessible ERP systems, according to the report.
“While some executives still consider ‘behind-the-firewall’ ERP implementations to be protected, we have observed clear indicators of malicious activity targeting environments without direct internet connectivity,” researchers said.
Third parties and company employees with access to ERP systems seem to be inadvertently helping bad actors in this endeavor, sharing log-in credentials and files with online forums that make data readily accessible to hackers, the report found.
“During the research project, we detected numerous examples of this, including SAP contractors sharing credentials on public Trello boards, a cloud-based project management tool,” researchers wrote. “If an organization exposes this type of information and their SAP applications are Internet-facing, there will not even be the need for exploits.”
ERP vendors under fire
SAP and Oracle are the two leading ERP vendors in the space and, naturally, their systems are the most at risk, according to the report. Key ERP offerings from the vendors are the SAP Business Suite and SAP S/4HANA and the Oracle E-Business Suite (EBS), public exploits from all of which have seen a 100 percent increase over the last three years, according to the report. Researchers also saw a 160 percent increase in activity and interest overall in ERP-specific vulnerabilities from 2016 to 2011, they said.
SAP in particular is under fire, with Russia hackers taking a special shine to targeting ERP systems from the vendor. Researchers said they observed detailed information on SAP hacking being exchanged at a major Russian-speaking criminal forum, as well as individuals interested in acquiring SAP HANA-specific exploits on the dark web, according to the report.
Moreover, a 7-year-old SAP exploit appears to be an unwanted gift that keeps on giving. Researchers said they observed exploitation of the critical vulnerability outlined in the DHS US-CERT Alert TA16-132A, that if exploited gives unauthenticated remote attackers full access to affected SAP platforms, providing complete control of the business information and processes on these systems and potentially others as well, according to US-CERT.
Complexity equals insecurity
ERP systems traditionally have been complex and unwieldy beasts–with customized functionality, detailed access control, no tolerance for unplanned downtime, numerous interfaces and integrations, among other complexities–complicating administrators’ efforts to secure them.
This situation remains today, which means “many organizations are
implementing and running insecure ERP applications,” researchers said.
Patching also has been haphazard and sometimes without logic or timeliness, since ERP customers struggle to understand which are the most important and relevant vulnerabilities that they should care about and mitigate, according to the report.
The number of security vulnerabilities and patches for both SAP and Oracle EBS has been growing steadily for more than a decade, and at the time the report was written, researcher said that more than 4,000 security patches for vulnerabilities in SAP applications and more than 5,000 for Oracle–850 of
which affect EBS applications–currently are known to exist.
‘Cloud’ing the situation
With ERP apps increasingly being hosted in the cloud, the ability to secure systems has become even more difficult, researchers said. While using Internet-facing ERP apps itself is not a risk, without correct security measures, it can become one, they said.
During their research, experts found that it’s possible to use Google Dorks—or SQL-based search syntaxes for specific file types or information–as well publicly available “device/IoT search engines,” such as Shodan and Censys, to detect Internet-facing SAP components and URLs served over the Internet directly related to SAP ERP applications.
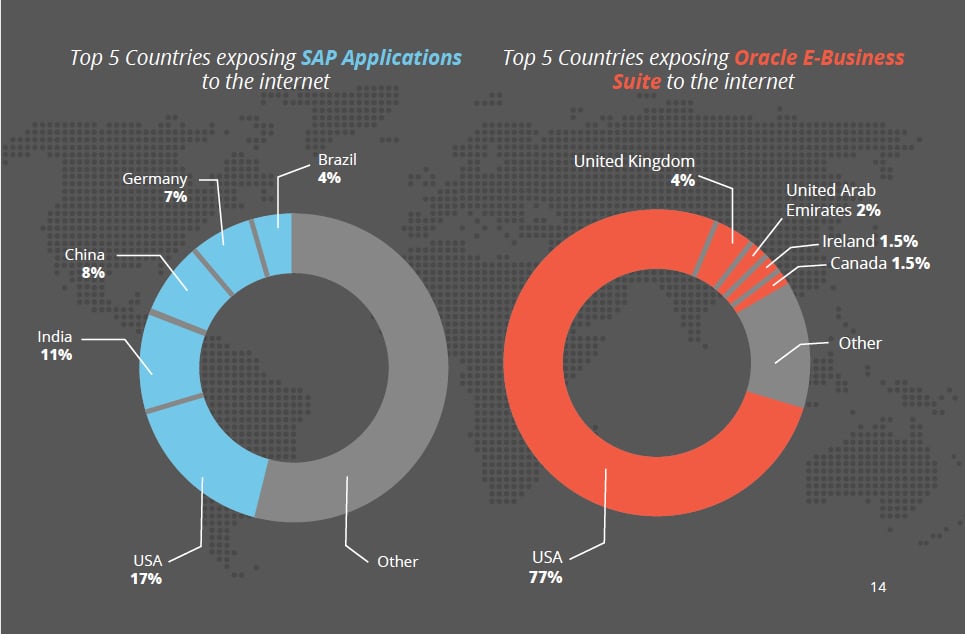
If researchers can find these components, that means hackers also can and exploit them as a way into the ERP system and gain access to critical information. Experts found more than 3,000 Internet-facing ERP services from SAP and Oracle E-Business Suite applications in the United States alone, showing the level of exposure of these applications.
Researchers also identified more than 17,000 SAP and Oracle ERP apps directly connected to the Internet, many belonging to the world’s largest commercial and government organizations. After the United States, German and the United Kingdom are the regions with the highest number of ERP apps exposed directly to the Internet.
“Threat actors are aware of this and are actively sharing information across the dark web and criminal forums to find and target these public applications,” researchers wrote. “Many of these exposed systems run vulnerable versions and unprotected ERP components, which introduce a critical level of risk.”
Mitigating the risk
Researchers posed a number of solutions to the current and imminet risk facing ERP systems and the valuable data they hold. From the system side, they recommend identifying and mitigating ERP application-layer vulnerabilities, insecure configurations and excessive user privileges in a number of ways.
Those include continuous assessment of ERP application-layer software vulnerabilities and ERP system configuration to implement more regular patching, and the detection of insecure parameters and settings–such as weak/default passwords–that could introduce security risks to the
environment.
To eliminate attacks from the interface aspect of ERP systems, researchers recommend that administrators identify and remove dangerous interfaces and APIs between the different ERP
applications in an organization, especially those with third parties and that are Internet-facing.
To do this, companies can continuously map existing interfaces and APIs between ERP applications that can potentially be exploited as pivot points, as well as assess the configuration of interfaces and APIs to evaluate use of encryption, service-account privileges and trusted relationships, researchers said.
Researchers also recommend that organizations more closely monitor users of ERP systems to avoid unintentional data or credential leaks to keep attackers out of systems this way. Specifically, they recommend administrators constantly keep watch over ERP applications for suspicious privileged- and non-privileged user behavior, as well as troll systems for indicators of compromise resulting from the exploitation of ERP vulnerabilities.
They also should check the Web and online forums regularly for leaked ERP data and user credentials as well as continuously monitor threat-intelligence sources to detect compromised ERP credentials, and take necessary action, researchers said.

Pingback: Report: Cybercriminals target difficult-to-secure ERP systems with new attacks | SAP Online Portal
Pingback: Apple, Amazon Throw Shade on Supply Chain Hack Story | The Security Ledger
Pingback: Report: Small, Stealthy Groups Behind Worst Cybercrimes | The Security Ledger