Botnets mounting credential-stuffing attacks against the financial industry are on the rise, with a more than 20-percent uptick in a two-month period, a new report from Akamai has found.
Bad actors from the United States, Russia and Vietnam are using credential stuffing attacks to try to compromise financial services firms, Akamai says in its latest State of the Internet report.
Credential stuffing attacks use “botnets” of compromised systems to flood websites with lists of usernames and passwords gathered from data breaches. The attacks can be used to assume an identity, gather information, or steal money and goods.
Akamai reports seeing significant botnet traffic on networks in financial services organizations of all types and sizes aiming to perpetrate these type of attacks, with 100 billion malicious login attempts from the beginning of November 2017 until the end of June 2018.
“What we’re seeing is that institutions of all sizes–from the very largest to much smaller one–have this threat,” Rich Bolstridge, Akamai chief strategist of financial services, told Security Ledger. “If you think you’re too small to have this risk, you’re wrong.”
The report found that these types of attacks lately have increased substantially, with 8.3 billion malicious login attempts in May and June, versus 6.4 billion in March and April. One such attack was so significant that it caused a major financial company’s login attempts to jump from an average of approximately 50,000 an hour to over 350,000 in one afternoon, according to researchers.
What’s even more troubling is that nearly half of financial organizations don’t have resources or protocol to prevent these types of attack, resulting in a loss of credibility, profit and other negative effects associated with the attacks, according to the report.
This is unwise, Bolstridge warned, as it leaves companies completely defenseless in the face of bad actors using botnets to credential-stuff their way to financial gain, or at the very least wreak havoc on a system by plaguing it with availability issues.
“Organizations should be prepared and include in their risk assessment what it would take to defend themselves against such an attack,” he said.
Dark Web inspires new attacks
Bolstridge cited a number of reasons for the increase in credential-stuffing attacks. One is that the credentials used in the attacks are from past data breaches and increasingly are becoming available for sale on the Dark Web, he said.
Another is that attackers don’t themselves need advanced coding or hacking skills to use this type of attack.
“You don’t need to have the technical skills to write a script that will try these user names and passwords,” Bolstridge said. “The botnets or the builders of the botnets go through that work and they are becoming much more sophisticated.”
Akamai sourced the data in the report from two of its own products. The first is Bot Manager Premier, which gathers intelligence from Akamai’s tools to classify bots and help customers combat malicious botnets based on their specific needs. The second source of data is Akamai’s Cloud Security Intelligence (CSI) platform, which collects data from multiple products across the company’s network to help feed intelligence to other Akamai products.
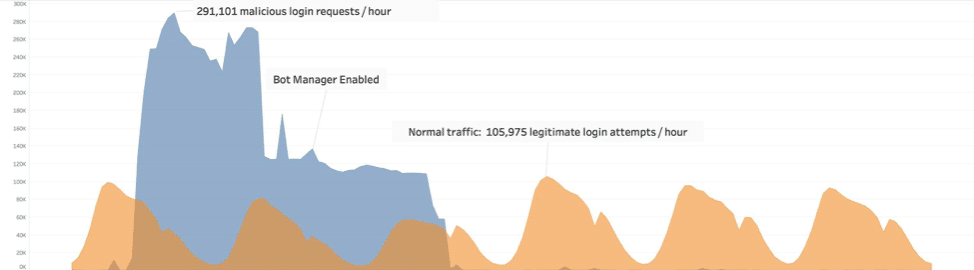
Tale of two attacks
The report specifically examines two attacks on financial sector that demonstrated common themes that can alert organizations to credential-stuffing attacks to help defend against them and prevent future attacks.
The first was detected after network administrators noticed a significant boost in traffic on the network of a Northern American credit union on the smaller scale of many financial-services organizations, Bostridge said. Further examination of the spike in traffic revealed three botnets targeting the network, only one of which was making the particular noise that alerted administrators to the attack, researchers found.
One of the other botnets discovered in the attack had actually been under the radar for some time, slowly and methodically trying to break in to the network. This actually can be more troublesome for an organization than a more obvious attack style, Bostridge said, because it can remain undetectable enough to do serious damage, he said.
“This low-and-slow type of attack is something that slips below the radar,” Bostridge said. “It only takes one successful one to cause a real problem.”
The second major botnet attack outlined in the report happened at a Fortune 500 financial services institution where a seven-fold spike in login attempts alerted administrators to a problem. Investigation into the activity found a credential-stuffing botnet sending hundreds of requests a minute to the company’s servers, researchers found.
In the case of both attacks, companies did not react to the situation until it became obvious there was a major traffic problem on the network, which is typical in how many organizations approach security, Bostridge said. However, a proactive approach would be better than a reactionary one in the case of credential-stuffing attacks, which “can become severe really quickly,” he said.
The way forward
Aside from the obvious–using credentials to steal information or funds from financial services organizations and banks–credential-stuffing attacks also have a number of other negative ramifications for companies, Bostridge said.
“The impact is very broad,” he said. “Even beyond the accounts being breached, there is major impact against the institutions.”
Given the risk and result of such attacks, it’s prudent for companies to begin to acknowledge that the threat is real, and take the initial steps to keep an eye out for these attacks on their networks, Bostridge said.
“Institutions of all sizes need to educate themselves on what this threat is,” he said.
This can be done by staying abreast of the latest news available on these types of attacks as they occur, as well as look to information-sharing groups that financial institutions use to share knowledge to learn about the attacks.

Pingback: Bank Attacks Put Password Insecurity Back in the Spotlight | The Security Ledger
Pingback: Podcast Episode 123: HaveIBeenPwned's Troy Hunt on Marriott's Big Mess and GreatHorn on the Asymmetric Threat of Email