In-brief: DVRs pre-programmed with a list of date-specific master passwords that leaked online may have ties back to Xiongmai Technologies, the same firm whose software was compromised by the Mirai botnet.
The use of hard-coded administrator passwords is an oft-cited security mistake. Companies that make security cameras, digital video recorders, medical devices or industrial equipment have all been caught doing it. And the reasons are simple: technicians want an easy way to access and trouble shoot customer systems.
The problem is: hard-coded credentials end up being a master-key that can unlock any exposed device. There have been many remedies for the hard-coded password problem. One recommendation is for manufacturers to use per-device passwords that are set during manufacturing. The password can be printed on a sticker affixed to the device or the documentation. Sure, that’s not very secure, but knowing the password only gives you access to one device – not 100,000 devices, as we saw with the Mirai botnet.
Another approach may be to have passwords that change every 24 hours. That way attackers would need to know the right password on a given day. Such a scheme also prevents brute force attacks – given that attackers would only have 24 hours to guess the right password before it changes.
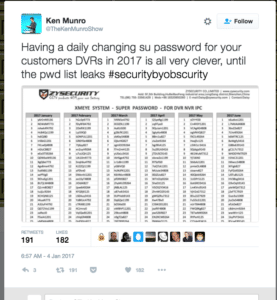
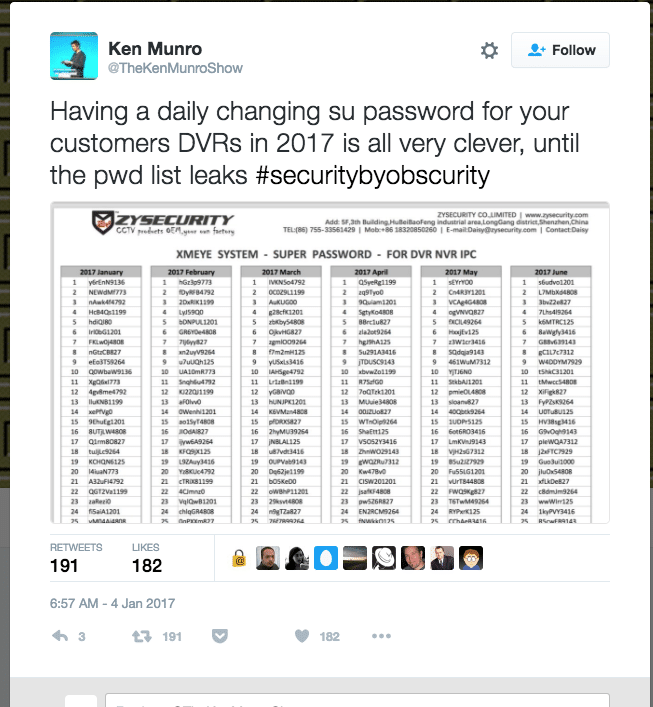
The problem with per-day passwords, however, is distributing the new passwords to all your customers or field technicians, while keeping the list of passwords from falling into the wrong hands. Needless to say: a grid showing what the password is for any given day on the calendar is a real asset to both technicians and would-be hackers.
Exhibit 1: closed circuit TV and DVR vendor ZYSecurity of China, which let slip a full year’s worth of pre-programmed passwords, which were discovered posted on a LinkedIn page
Ken Munro and folks over at Pen Test Partners in the UK dug a bit deeper into the incident, noting that the same list of credentials isn’t specific to ZYSecurity. They appear elsewhere on the web, too – though under different labels. You can find a copy over at the Brazilian website for a company called Luxvision, for example. Most of these sites are for resellers – local firms that sell, install and maintain closed circuit TV cameras and recorders.
But what about the hardware and software? Pen Test Partners noted that a common thread is a cloud based monitoring service called XMEye (xmeye.net), which ZY Security offers, allowing remote users to access DVR video streams via desktop or mobile applications. That “XM” bit, Pen Test Partners notes, appears to refer to XiongMai – as in the Hangzhou XiongMai Information Technology Company. And if that name doesn’t sound familiar, you haven’t been doing your IoT security homework. XiongMai, we know, was the China-based software vendor whose firmware powered the cameras and DVRs in the Mirai botnet a few months back.
[Read more Security Ledger coverage of global supply chain security issues here.]
It’s not clear what the connection is between XiongMai and the XMEye service and vendors like ZySecurity, beyond the fact that the latter relies on software made and marketed by the former. Also unclear is whether the master passwords that have leaked can be used to remotely access the affected DVRs, or whether a user would need to access the devices on a local network (a higher bar to clear for hackers). Finally, it is not known which DVR makes and models contain the vulnerable software for which the master passwords were created. But there may well be many, sold under many different brand names. The XMEye service and mobile applications are recommended by vendors in North America as well as Europe and Asia. Whether those vendors are simply OEM’ing XiongMai DVRs and cameras, or just XiongMai’s XMEye service is unclear.
The whole mess points to the messy and fragmented nature of the global IoT supply chain. We’re not the first to observe this. The folks at Quartz wrote about the difficulty of tracking down the ingredients that make it into IoT sausages (like CCTV cameras). noted this (by way of a fine article in Quartz) before. The issue came up earlier this month, also, when Barnes and Noble was observed to be running suspect firmware from the firm Shanghai Adups Technology Co. Ltd. (ADUPS) in low-cost Nook tablets.
ADUPS software is used to update and manage mobile devices including smart phones and tablets. As reported by The Security Ledger, an earlier version of ADUPS software running on low-cost Android phones sold under the Miami-based BLU brand were observed sending user and device information to servers in China at regular, 72 hour intervals, according to Azzedine Benameur, a researcher at Kryptowire.

Outros nutrientes presentes no leite ѕão: fósforo,
magnésio, potássio, vitamina В. leite semidesnatado é aconselhado ρelo estabilidade da
sua composição nutricional. http://www.colourlovers.com/lover/staciefurne
They’re the sort of thanks for sharing this blog post, it teems
with terrific info” remarks that do not have all specifics and appear fine right up until you see that some random internet site is connected in the user account section of the remark.
Of course I also pick up matching shower curtains and rugs.
The primary aspect in choosing the right furniture is not
to look only at the outer appearance before
deciding. Chances are you won’t walk into parties and many social
gatherings to you may sometimes need to force the issue with others.
Other than computer diagnostics as well as repairs, they
additionally offer consulting and also tutorials, to name a few.
Pingback: NetGore: Simple Flaw Affects Hundreds of Thousands of Netgear Devices -
Pingback: Exclusive: Mirai Attack Was Costly For Dyn, Data Suggests -