In-brief: Security experts are warning that so-called “file-less” attacks on commercial networks operated by banks and other firms are spreading and harvesting sensitive information, like administrator user names and passwords.
Security experts are warning that so-called “file-less” attacks on commercial networks operated by banks and other firms are spreading and harvesting sensitive information, like administrator user names and passwords.
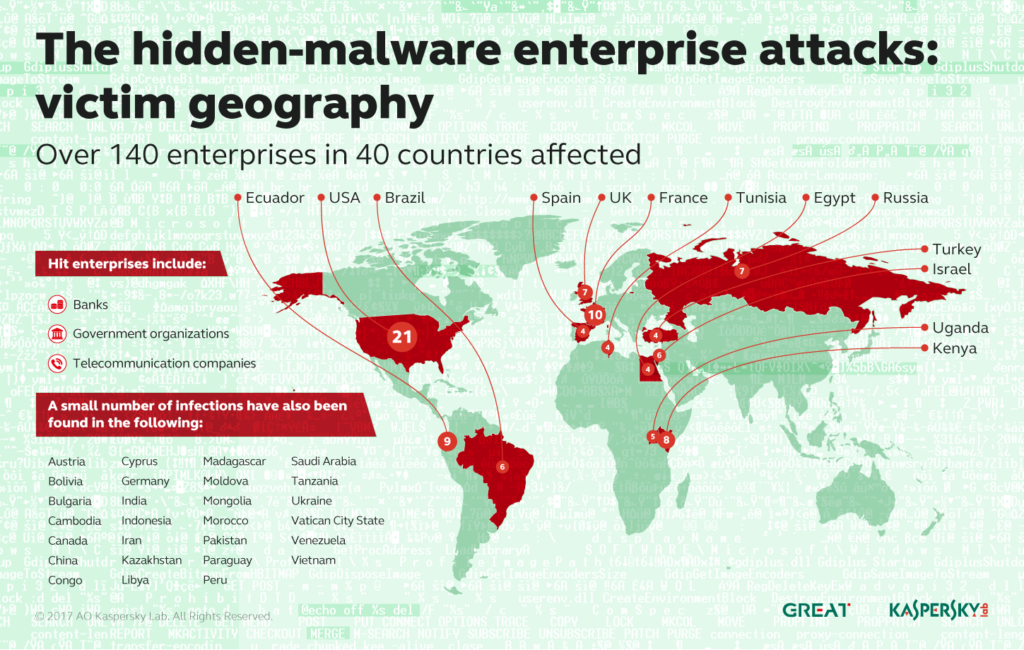
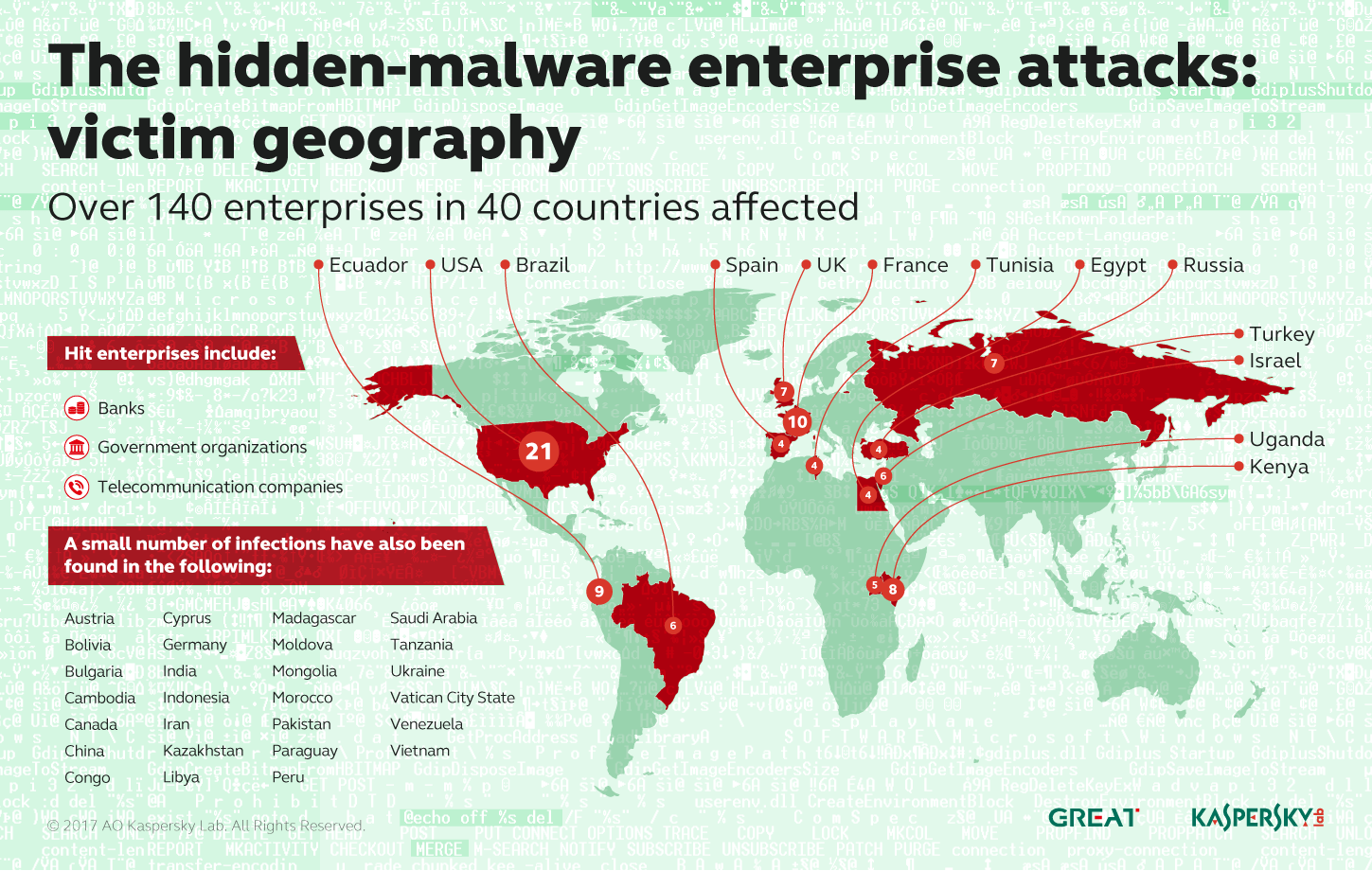
A report by the anti-virus firm Kaspersky Lab said the company identified a file-less malware attack while helping a bank investigate suspicious activity on its network. Kaspersky subsequently identified attacks on 140 other networks globally linked to the same file-less malware. The U.S. and France home to most of the incidents.
Kaspersky said the source of the attacks isn’t known and that attackers took steps to cover their tracks. Still, aspects of the attack bear a resemblance to attacks attributed to Advanced Persistent Threat (APT) groups with names like GCMAN and Carbanak, both of which are believed to have roots in Russia. Both groups have targeted the banking sector before, including attacks on ATM systems and bank networks.
This is just the latest incident linked to file-less malicious software, which runs from an infected systems random access memory (RAM) and Windows file registry, but is not permanently installed on its hard drive. Because no malicious files are placed on the infected system, security software often overlooks file-less malware. Kaspersky identified two pieces of malicious software used in the attack. Both were designed specifically to run in memory.
In the incident investigated by Kaspersky, attackers made use of standard Windows features and common administrative software tools to establish a foothold on victims’ networks and then expand their presence.The company said scripts written in PowerShell were found in the Windows registry of infected systems. Also, a utility called NETSH, a utility that allows network administrators to modify the network configuration of a computer. That was used to create a tunnel out of the victim’s network to servers belonging to the attackers and used to control the malicious software, Kaspersky said.
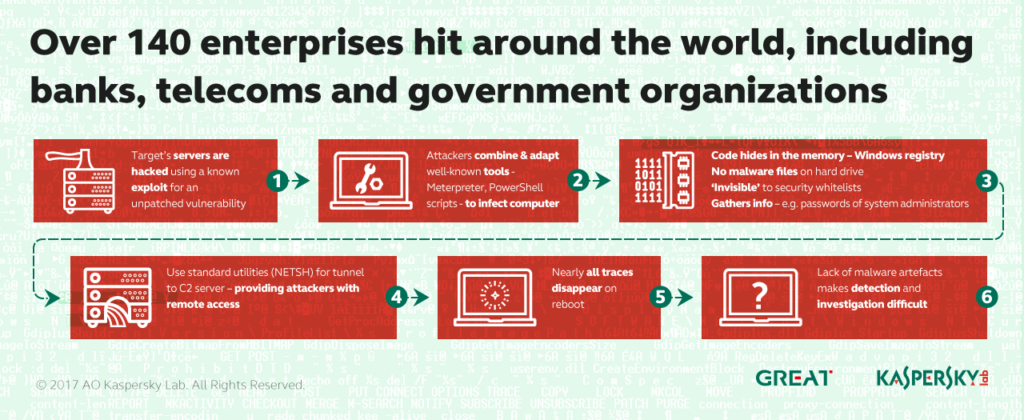
File-less malware is becoming more common, and is a means of “a clever hacker (turning) the operating system against itself,” wrote researchers at the firm Cybereason in January. Hackers are particularly making use of native Windows administrative tools like WMI (Windows Management Instrumentation) and Powershell, which are trusted implicitly by the Windows operating system and treated as safe programs by most anti-virus programs. Proof of concept tools, like Powersploit, build on these platforms allowing attackers to perform actions like keylogging, screen captures, data exfiltration and running shellcode, Cybereason said.
Kaspersky said that identifying the attacks was difficult, and required organizations to pay close attention to the various and subtle signs of infection.

Pingback: Attacks Target Bank and Business Networks