Editor’s Note: This article has been updated to include comment from Medtronic and from the researchers. A bit more on that: I spoke to the fine researchers who conducted this study. They are concerned that people might casually read the headline or first couple paragraphs and conclude that listening to Weezer will kill them. Listening to Weezer will not kill you. Listening to Weezer will not interfere with your implanted defibrillator if used under normal conditions. Their experiment (and my article) make this clear, but you do have to read down a bit in the article to get that, and I know not everyone does that. In any case, the health benefits of using an implanted defibrillator in accordance with your doctor’s instructions, far outweigh any risk from EMI or other electronic tampering. – PFR 5/22/2013.
Listening to Weezer could kill you. Literally.
That’s the conclusion of an unusual experiment by university researchers who used a snippet from the 90’s alternative rock band’s “Island in the Sun” as the basis for EMI (electromagnetic interference) attacks designed to overwhelm implanted heart defibrillators or even trick them into firing.

The Weezer-based attack is described in a paper presented on Monday at The Annual IEEE Symposium on Security and Privacy in San Francisco, California. In it, the researchers describe EMI attacks on analog sensors used in implanted heart defibrillators by Medtronic, Boston Scientific and St. Jude. In tests, the researchers showed that – under ideal circumstances – electromagnetic impulses could disrupt the ability of the device to accurately operate, or induce defibrillation shocks from a distance of one- to two meters.
The paper: Ghost Talk: Mitigating EMI Signal Injection Attacks against Analog Sensors was presented by researchers from the Universities of Michigan, Minnesota and Massachusetts, as well as The Korea Advanced Institute of Science and Technology (KAIST) and Beth Israel Deaconess Medical Center in Boston. The full paper can be viewed here. (PDF link)
Steve Campanini, a spokesman for Boston Scientific, said the company doesn’t comment on “these issues beyond published product information available on our web site.”
Medtronic spokesman Joey Lomicky said the company was looking at the report that Medtronic pacemakers, defibrillators, and implantable cardiac monitors have been “designed and tested to operate normally during a patient’s exposure to the electromagnetic fields commonly encountered in the work, home, and other environments.”
Patients with Medtronic cardiac devices should maintain a recommended minimum distance of 6 inches (15cm) between Bluetooth or Wi-Fi emitters and the implanted cardiac devices, he advised.
St. Jude did not immediately respond to a request for comment.

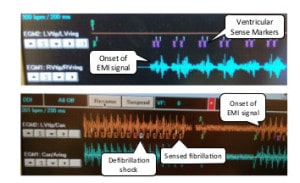
For their experiments, researchers used a “specially crafted EMI” device at a variety of power settings and distances to measure susceptibility of sensors in implantable medical devices and consumer electronics. The device, a signal generator that operates in the 9.00 kHz–2.02 GHz frequency range to modulate and transmit signals, sent test waveforms including a simple 440 Hz sinusoid, and an “arbitrary audio waveform” called the “Weezer” – a snippet of the band’s 2001 hit “Island in the Sun.”
Their findings? The defibrillators and other consumer electronic devices containing microphones are vulnerable to the injection of errant or malicious signals.
“Our measurements show that in free air, intentional EMI under 10W can inhibit pacing and induce defibrillation shocks at distances up to 1–2 m on implantable cardiac electronic devices.” However, the effectiveness of those attacks dropped dramatically when the medical devices were put in settings – like a saline bath – that better approximated their environment once implanted in patients. The same experiment on submerged devices showed that EMI attacks were effective only at distances less than 5cm.
The research team included Kevin Fu, a professor of computer science at The University of Michigan who teaches a course on medical device security has performed ground-breaking research into the security of medical devices.
The experiments don’t suggest an imminent danger to patients who have implantable defibrillators, but do raise concerns.
All four tested devices – the Adapta and InSync Sentry by Medtronic, the Cognis 100-D by Boston Scientific and the Promote by St. Jude – stopped pacing at distances from .68 m up to 1.57m in open-air tests. Only one of four implantable defibrillators was fooled into actually executing a defibrillation (shock) using an EMI attack in an open air test – that was Medtronic’s InSync Sentry, which was induced to issue a shock at a distance of 1.67m. Once the devices were submerged in a saline solution – an approximation of the environment of an implanted device – none were shown to be susceptible to pacing interference or induced shocks using EMI. In a test with only the device leads submerged in saline but the device left unsubmerged, EMI attacks were only effective at very short distances – around 3-5cm, researchers found.
The experiments raise questions about how much attention medical device makers are paying to the possibility of malicious or accidental interference with implanted devices, which do not feature defenses against EMI attacks.
To counter possible EMI attacks, the researchers designed a proof of concept defense, including analog shielding for defibrillators and a “signal contamination metric” that can spot efforts to spot attempted signal injection attack that try to mimic a cardiac event in the device wearer using what is described as “a novel defense mechanism that probes for forged pacing pulses inconsistent with the refractory period of cardiac tissue.”
Medtronic spokesman Joey Lomicky said the company’s implantable defibrillators already have some of those features.
“To protect our patients, several safeguards are built into Medtronic implantable cardiac devices to protect the devices from normal daily interference. Such safeguards include; a titanium shield, passive and active filters that help distinguish between natural heart beat signals and electromagnetic interference (EMI) signals,” he wrote.
The research is just the latest to raise concerns about the safety of implantable medical devices that rely on implanted and remote sensors to monitor the condition of the patient or relay information to and from external monitoring stations.
In recent years, security researchers have shifted focus from hacking networks and endpoints to implantable devices such as pacemakers, defibrillators and drug infusion devices. Their work has revealed sometimes glaring security vulnerabilities in the software and hardware used by life-sustaining devices. Notably, in 2012 Barnaby Jack – then a researcher at the firm McAfee – demonstrated a method for remotely controlling several types of Medtronic insulin pumps.
In January, researchers Billy Rios (@xssniper), a security researcher at Google, and Terry McCorkle (@0psys), the CTO of SpearPoint Security and Terry McCorkle said an informal audit of medical devices from major manufacturers, including Philips showed that they have many of the same kinds of software security holes found in industrial control system (ICS) software from the same firms.Their research suggests that lax coding practices may be institutionalized within the firms, amplifying their effects.
In an interview with The Security Ledger, the researchers said that medical device makers are generally doing a better job at security.
“It seems as if medical device manufacturers are addressing security earlier in the design process,” said Denis Fu Kune, part of the University of Michigan team.
However, the problems they discovered are widespread in devices that rely on analog sensors.
“This is not only issue of medical devices. There are a lot more devices that have sensors – in ATMs, and automobiles and so on,” said Yongdae Kim of The University of Michigan. “We want people to be aware of the issue.”

