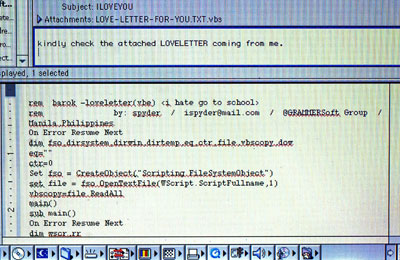
We like to throw around the term ‘Advanced Persistent Threat’ casually these days to refer to a whole range of sophisticated and persistent attacks – usually on high value targets. But a blog post today by Cisco Systems makes clear that many otherwise sophisticated attackers do just fine with some pretty low tech and old school methods. Case in point: an attack Cisco is dubbing “String of Paerls-” a series of attacks on companies involved in research and what Cisco calls the ‘industrial manufacturing vertical.’ According to the report, the attacks start with a decidedly old school attack: a Microsoft Word document that includes a malicious Office Macro.”When the victim opens the Word document, an On-Open macro fires, which results in downloadin and executable and launching it on the victim’s machine.” Now, macro-based attacks are truly vintage. They first came to light in the late 1990s, with the Melissa virus – an early and successful […]
Crime
Why I’m Not in a Hurry for a ‘Smart Home’ – WSJ
If you didn’t read it on Sunday, The Wall Street Journal sent columnist Christopher Mims to the home of SmartThings CEO Alex Hawkinson to get a tast of what ‘smart home’ living is like. Mims came away impressed – but also skeptical that the complexity of layering so much technology into our everyday routines is bound to have more bad outcomes than good ones. “Other than people who have very specific reasons to add automation to their homes, I have no idea why anyone would do it, even if the equipment were free…Even when smart-home technology works as advertised, the complexity it adds to everyday life outweighs any convenience it might provide,” he writes. As for the smart home ‘killer app,’ Mims quotes Hawkinson as saying that home security and monitoring seems to be the most promising application of smart home technology right now. Google’s acquisition of DropCam is just […]
Code Spaces Probably A ‘Target of Opportunity’
The spectacular collapse this week of Code Spaces, a cloud-based code repository, may have been the result of a an unspectacular “opportunistic” hack, rather than a targeted operation, according to one cloud security expert. The sudden demise of the online application repository has sent shock waves through the tech industry, laying bare what some say are lax practices among many cloud-based application and infrastructure providers. But the attack itself was almost certainly the result of a larger, indiscriminate cyber criminal campaign, said Jeff Schilling, the Chief Security Officer of Firehost, a Texas-based secure cloud provider. “This is something we pretty frequently: companies get held ransom with a DDoS attack, and if that doesn’t work, (the attackers) will resort to doing other things,” Schilling told The Security Ledger. But Code Spaces almost certainly wasn’t the only company the extortionists worked on, Schilling said. Instead, the company was likely caught up in a wide net […]
Wired Imagines Our Dystopian Connected Home Future
Over at Wired.com, the ever-provocative Matt Honan has a great little thought exercise on the “nightmare” that could come from connected home technology gone wrong. His piece, The Nightmare on Connected Home Street, is a first person narrative of a man who wakes up to discover he’s transformed into a cockroach inhabiting a virus infected home. “Technically it’s malware. But there’s no patch yet, and pretty much everyone’s got it. Homes up and down the block are lit up, even at this early hour. Thankfully this one is fairly benign. It sets off the alarm with music I blacklisted decades ago on Pandora. It takes a picture of me as I get out of the shower every morning and uploads it to Facebook. No big deal.” The story goes on to chronicle some of the other dystopian features of connected home malware – the hacked “Dropcam Total Home Immersion” account that […]
This Week In Security: Ebay’s School of Hard Knocks
It’s the end of another busy week in the security world. As we’re wont to do at The Security Ledger, we had DUO Security Evangelist Mark Stanislav in to the deluxe Security Ledger Studios to talk about the events of the week. On the agenda this week: the continued fallout from the hack of online auction giant eBay. The company ran into a thicket of criticism this week for the breach and its botched response. Despite knowing about the security breach for weeks, eBay seemed unprepared for the fallout once the news became public. Beyond its statements to the press, the company hadn’t taken steps to streamline the (inevitable) flood of customers who wanted to update their password. In fact, more than a day after the news broke, eBay still hadn’t made mention of it on their home page. What lessons can we learn from the breach at online auction […]