A group representing the Uyghurs,a persecuted religious minority in China, faces unrelenting, targeted cyber attacks that appear aimed at stealing sensitive data and otherwise undermining the group’s activity, according to a new study by researchers at Northeastern University in Boston as well as the Max Planck Institute for Software Systems and the National University of Singapore. A study of more than 1,400 suspicious email messages sent to members of groups representing the Uyghur minority found that more than three quarters of the messages contained malicious attachments. The messages targeted 724 individuals at 108 separate organizations. Moreover, researchers found overlap between the individuals associated with the Uyghur World Contress (UWC) and western targets such as the New York Times and U.S. embassies. The study, “A Look at Targeted Attacks Through the Lense of an NGO” is being presented at the UNENIX Security Conference in San Diego on August 21. (A copy of the full paper is […]
Crime
Zombie Zero Underscores Supply Chain Threat
A security start-up, TrapX Security, made a splash this week with the story of a new piece of malware, Zombie Zero, which wormed its way into logistics and shipping firms on shipping scanners sold by a Chinese firm. The malware was discovered during a trial demonstration of TrapX’s technology at a shipping and logistics firm. It was implanted on embedded versions of Windows XP that ran on the scanning hardware and in a software image that could be downloaded from the manufacturing firm’s website. “This malware was shipped to large logistics companies embedded in the operating system,” Carl Wright, an Executive Vice President at TrapX told The Security Ledger. TrapX declined to name the firm on whose behalf it worked or the manufacturer whose scanners were compromised. It said 16 of 64 scanners sold to the victim firm were found to contain malware. Published reports also note that malware say scanners with another variant of the same malware […]
Update: Cyber Spies Digging For Clues On Iraq?
The folks over at CrowdStrike have dug deep into a campaign of targeted cyber attacks targeting Washington D.C. think tanks and say they have evidence that whomever is behind the attacks has taken a sudden interest in U.S. policy towards Iraq. Editor’s Note: This story was updated to include comments from Adam Meyers, Vice President of Security Intelligence at CrowdStrike. – PFR July 8, 2014 14:30 Writing on Tuesday, CrowdStrike CTO Dmitri Alperovitch described a new campaign by a group they dubbed “DEEP PANDA” that was targeting think tanks specializing on U.S. foreign policy and national security. Alperovitch said CrowdStrike observed a pronounced shift in targets from think tank experts on Asia to experts on Iraq and the Middle East in recent weeks. The shift corresponded with the rapid escalation of violence in Iraq as the Islamic extremist group ISIS took control of large parts of the country. “This actor, who was engaged in […]
Industrial Control Vendors Identified In Dragonfly Attack
Two of the three vendors who were victims of a targeted malware attack dubbed ‘Dragonfly’ by the security firm Symantec have been identified by industrial control system security experts. Writing on Tuesday, Dale Peterson of the firm Digitalbond identified the vendors as MB Connect Line, a German maker of industrial routers and remote access appliances and eWon, a Belgian firm that makes virtual private network (VPN) software that is used to access industrial control devices like programmable logic controllers. Peterson has also identified the third vendor, identified by F-Secure as a Swiss company, but told The Security Ledger that he cannot share the name of that firm. The three firms, which serve customers in industry, including owners of critical infrastructure, were the subject of a warning from the Department of Homeland Security. DHS’s ICS CERT, the Industrial Control Systems Computer Emergency Response Team, said it was alerted to compromises of the vendors’ by researchers […]
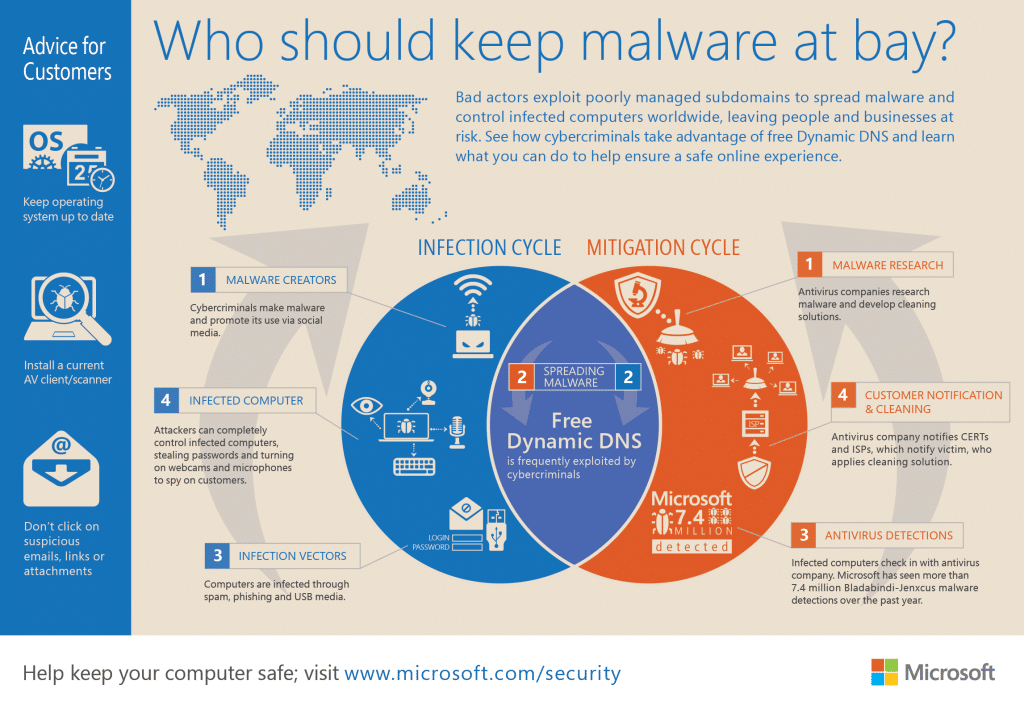
Microsoft Uses Courts To Take Down Malicious, Managed DNS Services
Microsoft Corp. has taken action against yet another cyber crime network, taking control of- and shutting down a managed DNS (domain name system) operated by the firm No-IP that were being abused by cyber criminals, the company said on Monday. The domains were associated with malware families named Jenxcus and Bladabindi that are believed to have infected on some 7.5 million systems, globally. The malicious programs – which are used to spy on the operators of infected systems – use Dynamic DNS services like NO-IP to communicate with command and control systems used to manage infected systems. Dynamic DNS makes the malicious systems more difficult to trace. In a post on Microsoft’s Digital Crimes Unit blog, Richard Domingues Boscovich, the company’s Assistant General Counsel said that the company had filed a civil case on June 19 naming two foreign nationals: Mohamed Benabdellah and Naser Al Mutairi along with a U.S. company, Vitalwerks Internet Solutions, LLC (doing […]