It has been almost a decade since Troy Hunt launched HaveIBeenPwned back in December, 2013. In the intervening decade, the site has become a fixture of the cybersecurity landscape: a one-stop online shop for anyone who worries that their personal information had been wrenched free amidst the global tsunami of data breaches, “double extortion” ransomware attacks and face-palm security lapses.
Hunt’s site was such a success because it took a simple approach to a complex problem: aggregate disaggregated breach data, then let the public search across it to determine whether they were personally impacted by a breach – and take action to protect their identity. Even better: Hunt offered (and still offers) his service as a free, public service: allowing individuals to search leaked and stolen data troves for email addresses, passwords, and more. (Check out our 2019 podcast interview with Troy (Episode 130) here!)
Development Secrets: The Final Frontier
These days, however, SQL database dumps and exposed Amazon S3 buckets aren’t the only source of leaked information. Increasingly, malicious actors are turning to secrets stored in source code to facilitate hacks and other malicious campaigns.
Episode 233: Unpacking Log4Shell’s Un-coordinated Disclosure Chaos
Consider the attack on CircleCI, disclosed in January, 2023, that saw the company telling its customers to urgently update API and OAUTH tokens, SSH keys and other secrets stored in code. Then there was the revelation, in September 2021, that a flaw in the Travis CI platform, a software-testing solution used by more than 900,000 open source projects, could have allowed malicious actors to extract secure environment variables like signing keys, access credentials, and API tokens from public open source projects. Events like these have been major red flags for DevOps organizations in recent years that malicious actors had code – and development organizations more generally – in their crosshairs.
DevOps Gets Its Own HaveIBeenPwned
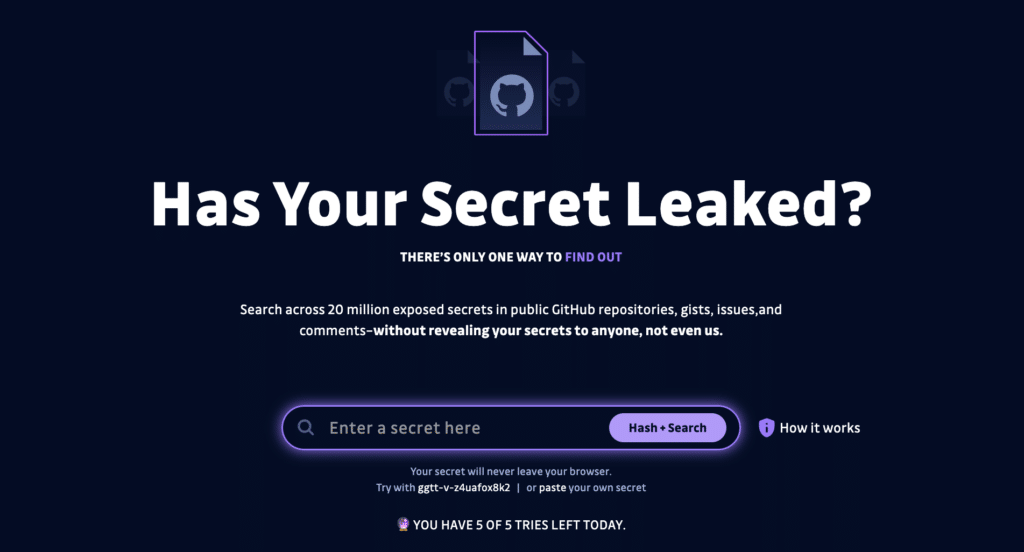
Those growing risks are now prompting a response, including the DevOps world’s own version of HaveIBeenPwned: ‘HasMySecretLeaked,’ a free toolset from the folks at GitGuardian that helps security engineers determine if any of their organization’s secrets have leaked via the GitHub open source repository.
Announced on Tuesday, HasMySecretLeaked is an online database containing over 20 million records of hashed secrets leaked via public sources, including GitHub.com. Users can submit a hashed version of their secret in the search console. HasMySecretLeaked will then scan its repository for a perfect match and return a “yes” or “no,” without revealing other secrets or their locations in the process.
Firms are embracing Open Source. Securing it? Not so much.
“Knowing whether your ‘vaulted’ secrets have leaked publicly is just one API call away. We built a privacy-safe and secure process that returns an unequivocal answer to the crucial question: Has my secret leaked?” said Eric Fourrier, co-founder and CEO of GitGuardian.
Platforms like GitHub have steadily increased support for features that allow developers to detect credentials and other sensitive information that lurks within source code. Earlier this month, for example, GitHub announced an expanded secrets scanning feature that allows developers to receive alerts if self-hosted keys are exposed in a code commit, and notify GitHub partners of leaked secrets in public repositories.
What SolarWinds Tells Us About Securing the Software Development Supply Chain
GitGuardian says that ‘HasMySecretLeaked’, goes further: enabling systematic leak checks for every secret in the DevOps pipeline and notifying security teams if hardcoded secrets in organization-owned repositories, Slack workspaces, or Jira projects, have leaked to public sources the organization cannot control or see.
Under the hood: lots of spilled secrets
Behind HasMySecretLeaked is GitGuardian’s substantial repository of leaked secrets data. The company has long scanned every public commit on GitHub for leaks of more than 350 types of secrets, including API keys, database assignments, and developer secrets. In 2020, it uncovered 3 million exposed secrets. That number jumped to 10 million exposed secrets in 2022.
Episode 216: Signed, Sealed and Delivered: The Future of Supply Chain Security
The capability is integrated into the GitGuardian Platform. GitGuardian users will also be able to access ‘HasMySecretLeaked’ from the command-line interface ggshield and use plug-ins to pulling secrets from third party tools like HashiCorp Vault and AWS Secrets Manager, staging them in local environments before leak inspection, the company said in a statement.
Given the possibility of the new service being abused, GitGuardian has also taken steps to harden the service and prevent abuse. That includes the development of specialized protocols to prevent abuse and “brute force” attacks. Individuals are limited to five, anonymous searches after which they will be required to register with GitGuardian and use its ggshield tool to run additional tests, according to GitGuardian CMO Carole Winqwist.
So-called “secrets sprawl” is a major challenge for development organizations that are managing both internal- and cloud-based development infrastructure, not to mention third party risk from contract developers and software supply chain partners.
Those risks have been laid bare through hacks and other disclosures. In September, 2022, an attacker breached the security of the ride sharing firm Uber by harvesting credentials from Powershell scripts discovered on an internal company Slack, for example. Then, in October, 2022, Toyota acknowledged that access to a database containing information on close to 300,000 users of its T-Connect mobile telematics application was exposed for five years after a contract developer inadvertently posted a database access key to their public GitHub repository in 2017.


Pingback: Sickened by Software? Changing The Way We Talk About 0Days – Raymond Tec