In-brief: a botnet of 120,000 cameras that takes its orders from servers based in Iran uses a long-ago disclosed security vulnerability in camera software to spread. The flaw affects over 1,000 different models of cameras, Trend Micro reports.
Trend Micro reported Tuesday that its researchers have uncovered yet another malicious botnet of around 120,000 compromised IP (Internet Protocol) cameras. This one takes its orders from servers based in Iran.
The botnet, dubbed Persirai, has been discovered trying to hack into more than 1,000 different models of IP cameras from a range of original equipment manufacturers (OEMs). The devices report back to command and control servers hosted on Iranian (.ir) domains, among other locations, Trend said.
The botnet is just the latest to cobble together compromised Internet connected cameras. That technique famously allowed the Mirai botnet to spread to hundreds of thousands of systems and launch some of the largest distributed denial of service (DDoS) attacks seen to date.
The Persirai botnet compromises Internet connected cameras by abusing the Universal Plug and Play (UPnP) protocol, which is supported on many IP cameras and allows them to be managed remotely. After locating publicly accessible IP cameras using UPnP, the attackers use a command injection attack to force the camera to load a ‘drive by download’ website and that pushes a malicious program that is installed in memory on the running device.
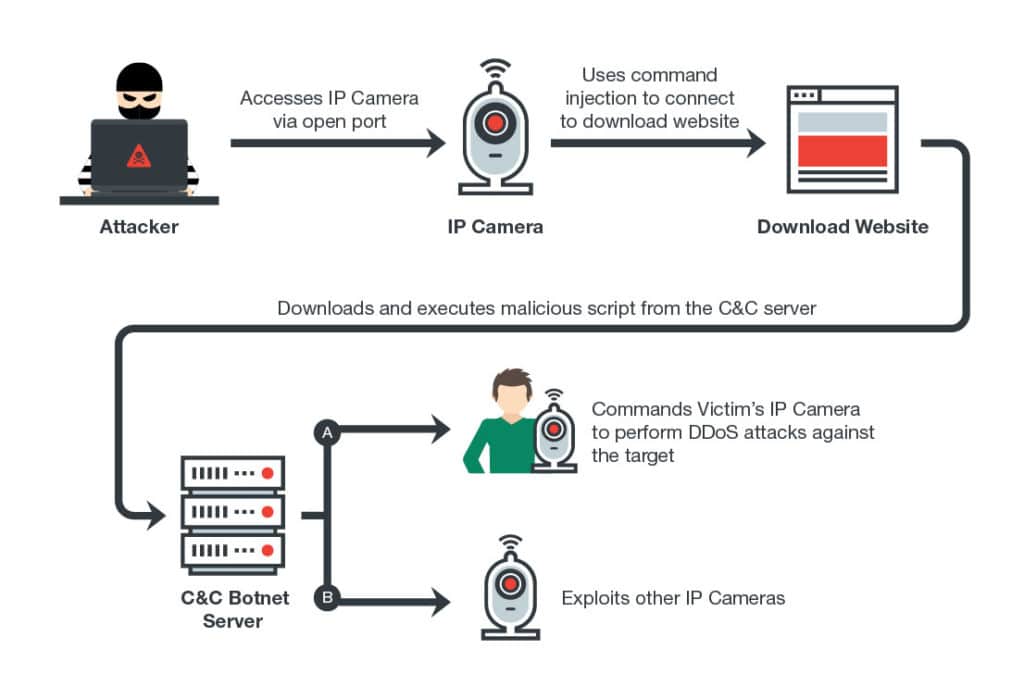
Once in control of the device, the hackers behind the scam can use them to launch denial of service attacks or to scan for and compromise other cameras, Trend said. It attacks them using a wide spread security flaw in camera firmware that was disclosed in March and that affects more than 1,000 different IP camera models. That flaw allows attackers to extract a password file from compromised devices, giving them access to- and control over the camera.
[You might also like: “Merchants of Doh: Cameras, DVRs, NAS fall down on security.“]
Trend also noted the role that “usual suspects” played in the creation of the botnet.
“A large number of these attacks were caused by the use of the default password in the device interface,” researchers Tim Yeh, Dove Chiu and Kenney Lu wrote. In addition to using a strong password, users should also disable UPnP on their routers to prevent devices within the network from opening ports to the external Internet without any warning, they said.
However, even with solid security practices, users can fall victim if vendors do not also shoulder responsibility for patching known holes in device software (or “firmware”), the researchers noted.
