In-brief: a report by the Cloud Security Alliance calls for a bottom up remake of infrastructure to support connected vehicles and warns of more, serious attacks as connected vehicles begin interacting with each other and with connected – but insecure – infrastructure.
The ecosystem of connected vehicles is in full expansion, but car manufacturers and industry stakeholders still need to come up with a way to prevent unauthorized data transmissions between different components that interact with connected vehicles, according to a new report from the Cloud Security Alliance (CSA).
Technology designed to allow remote message exchanges with and between connected automobiles could pose security risks, CSA says in its report, which delivers a set of recommendations for stakeholders in the automotive industry to move towards a more secure connected vehicle environment.
Connectivity in vehicles continues to grow despite the fact that car makers do not have a comprehensive ecosystem in which connected vehicles operate, CSA said. For example: connected vehicles already integrate with mobile applications via cloud infrastructurefor controlling functions remotely is already available for multiple brands. Major automotive suppliers and tech firms like Google and Apple have, in recent years, introduce third-party mobile applications such as Bosch’s Drivelog Connect, Hyundai’s Bluelink, and Google Play.
However, those connections have also been the source of problems. In June, 2016, an errant mobile application update knocked out radio, GPS and environmental controls to Lexus vehicles. With cars poised to connect to smart homes, smart roads, smart cities and smart businesses, the CSA report predicts that threats will increase as well, given a wider attack surface.
Connected car manufacturers and suppliers need to respond by adopting a uniform security framework for connected vehicles, CSA concludes. “In the near future, connected vehicles will operate in a complex ecosystem that connects not only vehicles between each other and the traffic infrastructure, but also with new forms of connectivity and relationships to cloud-based services, smart homes, and even smart cities,” said Brian Russell, Chair of the CSA IoT Working Group.
“For a safe and secure transportation system, the community must take a fresh look at the larger picture, and develop the policies, designs, and operations that incorporate security throughout the development,” he added. In this case, the community is defined by Original Equipment Manufacturers (OEM), suppliers, traffic infrastructure developers, traffic management centers, suppliers, aftermarket developers and any other entity related to the connected car industry.
The security recommendations from CSA take into consideration not only electronic hardware and software present in an automobile, but also third party platforms interacting with connected cars, such as mobile applications, road traffic equipment and infrastructure, wireless messaging and communication protocols.
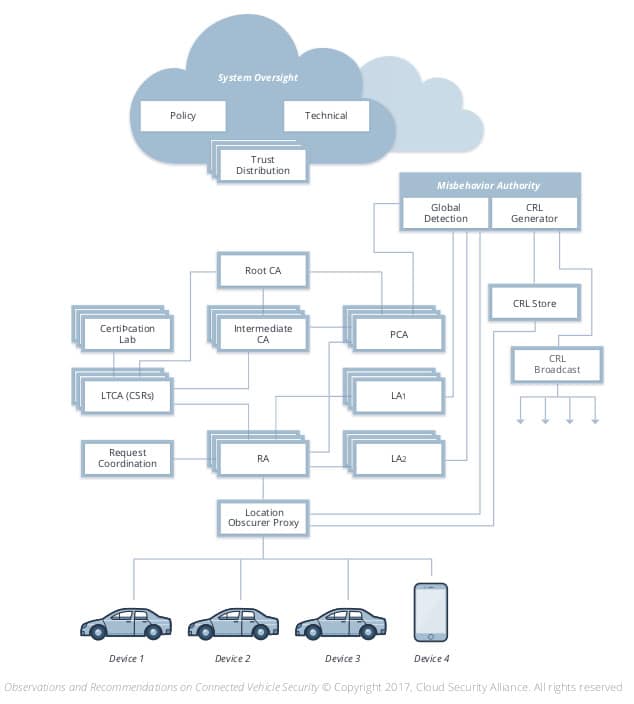
A stepping stone in achieving the correct security posture is to implement processes and standards built on secure systems engineering lifecycle. Code verification (both static and dynamic) for software used in connected vehicles and other smart infrastructure is called for, as are red teams to test the strength of the end result before it goes into production. Communications within and between connected vehicles and other devices should use proper encryption that follows NIST and ENISA standards on cryptographic protocols, or digital signatures from Security Credential Management System (SCSM), a proof-of-concept public key infrastructure specifically built for vehicles.
For example: one issue that has been exploited by researchers to show weaknesses in connected cars is lack of full network segmentation between critical and non-critical elements, allowing access to sensitive and safety critical functions like brakes and steering through less important components, like radios and environmental controls. Such an approach was used by researchers Charlie Miller and Chris Valasek in launching a successful, remote proof of concept hack of a Jeep Cherokee.
CSA also warns that connected traffic infrastructure makes it an attractive target for an attacker and could be used to attack vehicles or otherwise undermine road safety. “RSUs [road side units] often have on-board GPS connectivity. Many RSUs are accessible via a standard RS-232 serial interface to the device, and most do not provide any form of high assurance tamper resistance.” Research by the firm IOActive found that cities and municipalities are anxious to adopt “smart” infrastructure, but struggle to balance “smartness” with security, according to IOActive researcher Cesar Cerrudo.
Those underlying vulnerabilities could compound the challenge of securing smart vehicles.
The key to eliminating as many risks as possible before cars become part of the looming interconnected future is a collaboration between all parties and embracing the safety standards defined by organizations watching the latest technological developments. Connectivity in automobiles is still at the beginning and numerous problems have already been pinpointed. The recommendations from CSA are pertinent beyond the current context and offer a good foundation for the super-connected tomorrow.