In-brief: The FBI seized equipment from noted security researcher Chris Roberts on Wednesday, alleging that Roberts may have tampered with the systems aboard a United flight to Chicago. Roberts denies the claim.
Chris Roberts (a.k.a sidragon1), a leading researcher delving into the security of airplanes, was pulled off a plane in Syracuse, New York, on Wednesday by the FBI and questioned, apparently over concerns that he attempted to hack into critical systems aboard a United flight earlier in the day. [Updated to add comments from Mark Rasch. 4/17/2015 11:20]
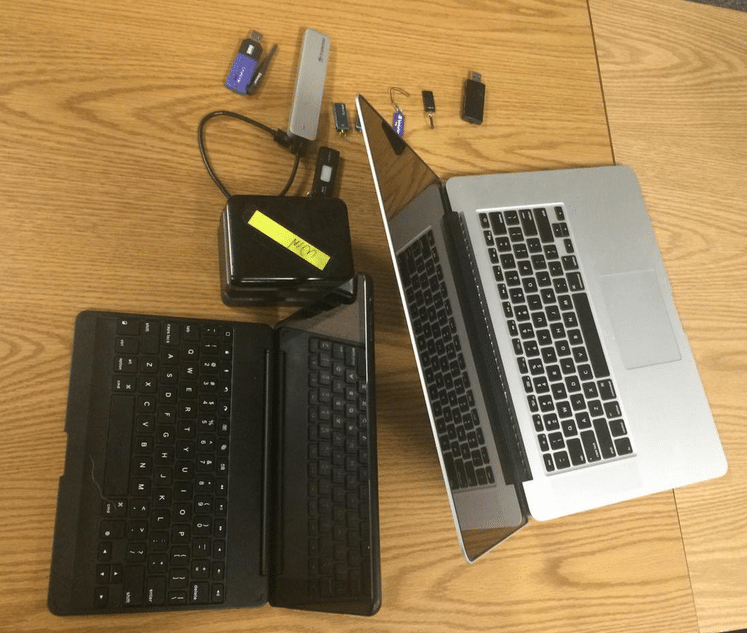
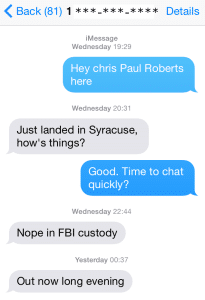
In an interview with The Security Ledger on Thursday, Roberts said that he was questioned by FBI agents for four hours Wednesday evening and then released. (A text message conversation, however, suggests he was detained for around two hours.) His laptop and a variety of external storage devices were confiscated by the FBI, which said it wanted to determine whether Roberts, an authority on security vulnerabilities in modern aircraft, may have accessed sensitive systems on a flight from Colorado to Chicago earlier in the day.
Roberts is the founder and Chief Technology Officer of One World Labs, a security research firm.
In response to mentions of his earlier research on Twitter, Roberts, using the @sidragon1 handle, had tweeted about his ability to hack into in-cabin control systems on the Boeing 737.
“Find myself on a 737/800, lets see Box-IFE-ICE-SATCOM, ? Shall we start playing with EICAS messages? “PASS OXYGEN ON” Anyone ? :)”
EICAS refers to the Engine Indicating and Crew Alerting System, critical in-flight systems.
That apparently got the attention of federal authorities, who were waiting for Roberts when he arrived in Syracuse that evening for a scheduled talk – ironically, to an audience made up of law enforcement.
“Two officers got on, two regular Syracuse PD. They walked back there, and past me. The FBI agents walked on, they walked past me and turned around at which point, I said ‘so, should I get my bags now?’ and they said ‘yes, please, Mr. Roberts,” he told Security Ledger on Thursday.
Roberts has been demonstrating vulnerabilities in the avionics systems used on modern airplanes for the past five years, warning that modern planes have converged critical systems and non-critical systems such as in-flight entertainment and wi-fi in ways that create serious security and safety risks.
He isn’t alone. Ruben Santamarta a Principal Security Consultant for the firm IOActive demonstrated at the 2014 Black Hat Briefings how satellite based communications devices (SatCom) used to provide Internet access to planes in flight could be used to gain access to cockpit based avionics equipment. Brad “RenderMan” Haines has also demonstrated methods for moving from in-flight entertainment systems to critical control systems aboard planes.
Roberts said he had met with the Denver office of the FBI two months ago and was asked to back off from his research on avionics – a request he said he agreed to. But recent weeks have seen him get high profile media attention from Fox news and CNN, who ran stories about the danger of hacking into airplanes in flight.
Those stories apparently got the attention of federal authorities, Roberts said.
“I don’t know what the logic is. They’re probably pissed that FOX picked up on it and CNN picked up on it and it’s gotten a lot more media attention,” Roberts said.
“This has been a known issue for 4 or 5 years where a bunch of us has stood up and pounded our chest and said this is an issue…Are they pissed because there are credible threats and we’re giving those credible threats more intelligence, or because we’re standing up and saying ‘there’s a problem,’ or because they can’t get anywhere with this? I don’t know.”
He described a testy but polite meeting with FBI agents, who accused him of “tampering” with systems on a United flight to Chicago. They requested that Roberts unlock his work laptop and provide a password needed to decrypt the hard drive so they could do a forensic analysis of the hard drive. Roberts says he refused the request because of proprietary information stored on the hard drive. He demanded a warrant to search the computers and hard drives. Roberts indicated via Twitter that he had not received a warrant nor had his equipment been returned.
Amanda Cox, a spokeswoman for the Albany division of the FBI declined to comment.
Mark Rasch, a former Department of Justice Lawyer and now head of Rasch Technology and Cyberlaw said that Roberts’s tweet was “borderline” and that the FBI would almost certainly obtain a warrant to search the devices. Still, he questioned why the agency was following the social media posts of a security researcher closely enough to track down his flight in real time and apprehend him.
“If this guy is going on Fox and CNN and talking about this, they know for certain that he is not a threat,” Rasch said.
Roberts says the real issue is not his research, but the failure of firms like Boeing and Airbus to respond to issues raised by security researchers. Roberts said the airline manufacturers hadn’t learned the lessons of technologies companies like Cisco and Microsoft about the proper response to responsible disclosure by security researchers.
“It feels like this industry is going through the same issues. The problem is, if I break a F5 device or a Cisco device, I’m not harming anybody. I screw around with an airplane, I’m taking 100 to 400 people out of the sky and you’re not recovering from that.”
The FAA and authorities should be taking a more assertive stand in forcing airlines to address known security issues he said.


Pingback: 1p – FBI seizes equipment, alleges plane hacking | Profit Goals
This is precisely the sort of thing he shoild not have been doing. I generally do not side with the feds but what he did was ethically irresponsible and ignoring that and encouraging shit like this is precisely how and why police states come to exist in thebfirst place. If the feds had NOT responded what do you think would have happened? He probably would not have brought down a plane (also because he is a self-aggrandising dude who wants attention) even accidentally but there is a social precedent and it is the same sort of precedent that anti-disclosure was about years ago: it wasn’t about giving the gov more power, it was about not giving them excuses to take it.
Tl;dr: with power comes responsibility to act appropriately. Expect to be held to standards. Do not ezpect it’s okay for you to peetend to do shit that anybody else would get harrassed for doing.
Also he doesn’t really understand aeronautical networks but that’s okay. A lot of bugs require real world conditions that only seem to exist. I am sure this press will get his company more business. It usually does. Can’t people just stop FUDding?
No doubt that making idle and maybe threatening sounding comments about a plane in flight is not a good idea. That said: Chris’s point is that he’s merely talking about research that he has been talking about for 4+ years. In other words “there’s nothing new here.” A bigger question may be whey the FAA and federal government have been unable to address the issues raised by independent researchers in a systemic way. So, rather than ‘killing the messenger’ maybe help deliver the message to airline manufacturers that its time to get serious about cyber risk to planes in flight. Agree?
“This is precisely the sort of thing he shoild not have been doing.” Wrong, wrong, wrong. This is what he was “allegedly” doing and this is EXACTLY what he SHOULD be doing in order to determine HOW to fix the potential problem from those that WOULD DO the WRONG thing with the information!
Would you rather he do the research (whether sanctioned or not) or have some group with malevolent intent beat him to the punch?
Proof of Concept via terroristic threat, even if intended as a joke, is not in any way, shape, or form ethical. That guy who got pulled by the feds for his tweet about ‘destroying New York’ absent even the slughtest bit of context? Ridiculous overreach. Mentioning manipulating specific flight-critial systems, true or not, probably (as Rasch later said) WILL get a warrant. And it probably should. I am not sure he should be convicted of anything (at least not anything with a permament record) but things are getting out of hand if you really believe there is an Us or a They. Especially considering the faxt that someone who IS dissatisfied about their research being ignored actually does wind up fitting a knkwn past profile of someone who MIGHT act. And I am not at all saying he did, would have, or could have. I am stating that people are getting pissed and Chris is getting support for something no ethical security researcher should condone or excuse. Frankly if he got charged and the EFF took his case on I would stop my yearly donation. Thus wasn’t overreach. If they come at him with piled indoctments, sure, maybe. But there are actual gross injustices occuring. You’re just making Chris famous and setting an example (and this is one of my points) that if you don’t get your way (and if he was on his eay to speak at a conference to feds about this he was on his way to getting it ffs) it’s perfectly acceptable to make dubious half-threats to get a response. You know who does that? Five year olds.
tl;dr if he wants to do the research don’t do it on a plane full of people. he didn’t allegedly tweet. he tweeted. let forensics decide if he did get access (on the plane and on his computer if need be… though if he is refusing to give up his encryption keys (and I would too) the problem is he is basically going to contribute to tearing down the right to refuse to hand over keys. If you don’t want to be investigated for hacking an in-flight system when you obviously have the self-proclaimed ability to do so it’s easy: don’t do it OR pretend to do it AND TWEET about it. Better yet don’t do it. How is he investigating these “faults” if he lacks access to jumbos? Either he isn’t doing it or he has access in which case why is he even pretending to do this? clear enough?
tl;dr
His actions are for the good, not bad. He brings to light serious vulnerabilities that need to be taken care of by authorities. Test flights should be conducted to determine vulnerabilities and fixes with various aircraft.
He could have been doing his “tests” with the plane landed or within a hangar, NOT ON THE AIR, risking 150+ lives, just for the fun of it. If he is a serious researcher, he knows he can work with the communication systems with a plane on the ground and without passengers!
Yeah, right. Do you see the airlines giving him time on a plane in the hanger (@ XX thousand $/hr) to show up their weaknesses. And it is obvious that Boeing and Airbus don’t want to do it either since they have had over 4 years to react. No, everybody will stick their heads in the sand until some terrorist uses this weakness to take down a plane and then the media will be shouting “why did we not do anything before now?” And the lawyers will be licking their chops
I applaud this brave researcher for daring to show how stupid and negligent the aircraft manufacturers, airlines and the Government/FAA are.
Are you experiencing a state of bliss?
I disagree with the moppet’s comments. I am a security researcher and this is absolute BS to be honest. There are so many of us that do our research to protect critical infrastructure only to be ignored when the threats are very real. Anyone that thinks us not doing this research will “not” find those wholes is just a d+++a++. The reason being that stopping encryption, research does nothing as don’t you think terrorists are going to do this anyway? What the FBI SHOULD BE DOING is engaging the security community, not pushing it away.
Maybe we should be talking to the CIA or NSA, at least they know why we do research and also do the same research I may add. FBI you’re doing it all wrong and failed. Its time to wake up and engage a community you will never stop, if you did try to stop it, you jeopardize every American’s security and protection. We need to discuss exploits and holes so that these get plugged, not side with corporations that are not doing a fantastic or even “good” job at creating solid and secure code.
Think about it and for heavens sake get someone in that actually knows and understands security and how this community works, we are friends not threats. You should learn from your mistakes because up to now, you obviously didn’t.
I am reaching out, giving you that chance, you should take it. Our nation and our citizens depend on us working together, we have a common enemy…. ISIS and all the other dingbats out there, we don’t have any more time for pissing contests.
(Sorry for the rant, just can’t hear this crap anymore, we don’t have time for this….)
You live in a delusional fantasy world of black and white, good and evil, not realising you’re no more the good guy than the very people you are railing against. This isn’t an epic battle of Them versus You, bucko. Those are fun til you wind up ‘inexplicably’ on the other side.
There are only sides.
You state that their is no black and white … just sides right/wrong, left,right front,back.
So black\white seems to work pretty well in this case.
sides are never only and always 180 degrees apart. or even numbrrs divisible by 90. so no. wrong.
Idiot (this is your ID, not an offensive term from me),
If you are serious researchers, why don’t you fill up a plane with your family members, and play with your security tests while flying with them (your family members), and not with innocent people that can die because of a stupid “research” error that can bring the plane down?
Just a thought, but maybe some of the airlines ought to think about hiring, possibly, some type of “leading researcher delving into the security of airplanes” to actually show them just how vulnerable their systems might be.
Hey – yes. You are seeing auto makers doing just this (notably Tesla). Like many things we rely on, airplanes are – more than ever – just hardware running software.
Sure. But not the ones taking it upon themselves to do so without approval, in-flight, with no common sense, discretion or actual safety in mind.
The only thing that this “researcher” is going to accomplish is getting the wifi system disabled on most aircraft for everyone. Any responsible researcher would work with the Aircraft manufacturers to assist them in improving their security. This guy is just looking to get attention. Say goodbye to in flight wifi. You can blame this guy and his irresponsible behavior for that.
Chris roberts ya got that right I like it it’s all cool to me so ya got me I love this add proud to be. The first to like this thanks chris roberts
I had this exact same discussion re. SCADA systems.
Lesson 1: Security through obscurity is… No security at all!!
Lesson 2: Airgapped systems are only as secure as the weakest link.
Lesson 3: If you are serious about security, get everything vetted by multiple independent
third parties armed with the latest tools and methods.
Lesson 4: NEVER, EVER “Shoot the Messenger”. A falling king does that as a last desperate act.
Here endeth the lessons.
Agreed 100%. As Roberts says: software and hardware vendors learned the “don’t shoot the messenger” lesson 10 years ago and now work with researchers, including offering bounties for vulnerabilities in their products. There’s no reason an Boeing or Airbus couldn’t follow suit. Lesson 5 for researchers: don’t make threatening sounding statements about critical infrastructure, even in jest!!
He wasn’t being a messenger here. He was tweeting to all and sundry in a ridiculously irresponsible manner. So let me get this clear according to some people here’s sentiments: it is okay for HIM to do this sort of thing because he is a ‘researcher’ but how do people know who is serious and who isn’t? for that matter, how many people who have been shouting for attention WILL go down for a ship if they don’t get it ‘to prove their point’?
Someone mentioned scada. For shits and giggles let’s say you started tweeting about how someone like the POTUS or an ex were on an elevator and you had control over that elevator. What is the appropriate response? Let’s say you’re a researcher studying how insulin pumps can be remotelt controlled… and then you tweet that at a diabetics conference after having a blog entry saying you dislike fat people for eating the SAD and becoming lazy diabetics (nb not my opinions, making a point here). Let’s say you get access to a nuclear energy facility and can find you can manipulate the… ha. Right. That’s been done.
There is nothing ETHICAL about using even a hypothetical use case to bully someone or scare or threaten them. If you don’t like shit, change it. You aren’t being witty. You aren’t being clever or smart. And you don’t know shit about unforseen consequences.
BTW what if it was someone who had read his ‘research’ or watched a talk on it and tweeted the same thing?
He wasn’t *arrested*. He was being given (perhaps a rude) triage. Or do you think surveilling everyone constantly so they can always ‘know intent’ (they can’t btw) because someone says they are a whitehat is perfectly peachy keen? “Aww damn dawg, I got clearance to tweet I can crash this plane.”?!
One consideration is that avionics software requires extensive certification. Unlike router or desktop software that can be released with minimal regression testing, avionics hardware and software requires a comprehensive test suite and certification documentation that a Designated Engineering Rep (DER) must approve. The EICAS software would by certified to a higher level than the in-flight wifi and satcom systems. It may not be as simple as installing a commercial firewall between the two aircraft systems to address any potential network security holes. But, it does appear that this issue should be investigated.
But then we need to start looking at the verification process and parties involved. If these concerns have been raised for 4+ years and the certification organizations haven’t made the changes we need to follow the money. Who makes money in the certification process? Who loses money when if something doesn’t pass certification? Why would airlines and the FAA not work on these problems seriously? Because there is financial motivation to not take care of the problem. Has anyone looked into how much money the airlines are making from in-flight entertainment systems and how much they would loose if it had to be disabled until fixed?
If this prompts the FAA to take steps to correct these security problems will anyone regard Roberts as a hero?
This is not the way to go about doing this. From his tweet, if it is reported accurately, he should be arrested and charged with tampering with an aircraft.
The only reason I say this is, you do not do this on an airplane full of passengers. What if he unintentionally caused some type of interruption within the systems. It is the “what if”, the unknown. These types of things can be tested on the ground, never, never in flight with passengers.
Suppose he does manage to trigger an EICAS message. The flight crew is going to have to deal with it. What if it causes the crew to take action that is not warranted, because of a fake message. Hopefully the redundancy of the systems on the aircraft would help them determine a false reading, but what if it doesn’t.
I won’t go into all the other issues that may occur when the plane arrives at its destination.
If he actually did get into the system and they do forensics and show it is true he should absolutely be charged with a few felonies (and this from someone who generally believes a lot of comp crime charges are utter and complete bs and should never exist in the first place).
To toss a shitty CEH requirement out he had no agreement with the compamy, he had no permission to do what he did, and he put lives at risk.
If he did NOT get access then it was just pure irresponsibility and I would suggest he not get hired to do pentests legitimately since he clearly lacks respect for potential clients. Then again most back corriders are full of fuckheads talkkng about their client engagements and sharing privileged information about client networks because, hey, gotta brag.
I have met blackhats with tighter lips and more acruples who’d never ever even consider to fucking joke about doing thus sort of thing. (Invectives judiciously included at times to make my point).
Sorry, bad thumb typing. Most of the typos are obvious so I won’t bother correcting them, but acruples in my last paragraph should read scruples (perhaps less obvious… perhaps ironically)
Oh and in case there are misunderstandings here, saying he should be charged with a few felonies does NOT mean I think he should be pounded by the legal system or punished in some remarkably outsized manner. I am certainly not saying he should go to prison for 8-10 years or even have a felony record. I AM saying he should NOT be accorded special status. If he got in to an in-flight system (and I have some doubts given airgaps) and was actually accessing it in a live case scenario then he hubristically and without giving a shit about anyone else decided his ego mattered more than the actually very tipping-point-prone airplane he was on – or more specifically the lives of those on board. So much could have gone wrong if he was on those systems regardless of his intention that the fact people are taking his side in this literally boggles the shit out of me. Is it because I worked toward a pilot’s license? When to an engineering school? It certainly isn’t my years of experience in security apparently.
I think people are part of a big group delusion. Then again I think that’s what shit has devolved into and was built up into too. Quit being rockstars. You aren’t. If you care about security act like it.
I agree with Mark completely. When I read the news release I figured the “expert” was either probing the aircraft’s electronics to see if he could get in to satisfy his own (professional?) curiosity OR
he was showing off for a friend (which explains his Tweets) or both. In any case he showed not only unprofessionalism but recklessness. In other words the jack-off could have fucked up everything and brought the plane down. Who knows? Maybe that’s what happened to that Malaysian aircraft that disappeared a little over one year ago and no trace of it has yet been found. (?)
Pingback: Χάκινγκ εν πτήσει; Ούτε γι’ αστείο! | deltaHacker
Pingback: FBI Accosts Security Researcher Over Fear That He Hacked His Flight | I World New
Pingback: FBI Accosts Security Researcher Over Fear That He Hacked His Flight | Gizmodo Australia
Pingback: FBI Accosts Security Researcher Over Fear That He Hacked His Flight | The Fat Cat Collective
Pingback: Researcher who joked about hacking a jet plane barred from United flight - The Best Tech News
Incidentally it is his braggadoccio and apparent ignorance that what he did was both reckless and unethical that pisses me off more than anything else (even his recklessness). Or more specifically it compounds his actions. He saw so little wrong with it that he basically made a stink about the feds, apparently lied about how long he was questioned (forgivable; we all go through time dilation and I am sure fed questioning felt twice as long), blasted his story for fame and pity, desired to be the victim, and acted pissed off the feds were basically doing their job.
So, money on it being one of his twitter friends who contacted an agent, not the FBI (or at least only the FBI) keeping tabs out of concern for the possible unintended consequences?
I accepted, in so much as I could, that he may have screwed up. Ehat I find galling is that he doesn’t see it as a f-up and is painting himself as the victim. The only person he is the victim of is himself for making bad choices. Just man up and accept responsibility for makkming a mistake or taking it too far. Don’t think you’re some sort of poster child for a cause. You aren’t. Well, unless your cause is making it so anyone could tweet this stuff on a plane. This is not a matter of free speech. Free speech is saying there is a problem. This is not that
Pingback: Researcher who joked about hacking a jet plane barred from United flight | The other line moves faster.
That’s outrageous, he shouldn’t point out that the manufacturers of airplanes took stupid short-cuts in the design of their onboard digital comms systems, and rely on ignorance to stop their security short-comings from become a serious danger to their passengers!
/sarcasm
For some reason I am reminded of the Ford Pinto and how Ford thought it would be cheaper to pay a few claims for injuries:
http://en.wikipedia.org/wiki/Ford_Pinto#Fuel_tank_controversy
You’re being ridiculous. Let’s put aside the computer itself for a minute. I was only ever (barely) rated for single engine aircraft and anybody with a far higher rating than mine would vehemently exclaim how dangerous it is to even imply something capable of causing panic on any airplane. What exactly do you think this could have done had a fellow passenger seen it? Or a friend/family member on the ground that was in communication with someone on the plane? Never mind the gross irresponsibility amd unethucal nature of what he did, even if he NEVER had ANY access whatsoever he was actually capable of taking down that plane *accudentally*. There is a reason you also don’t say “why yes there is a bomb in this bag” as a joke when the checkin does their rote questioning. If you have ever even joked about THIS you will have a miserable time. And that is before even making it onto the plane and in the air.
Would you feel safe on a flight where this was done? Do you understand just how delicate flights are, especially involving multiple engines? It’s pretty damn close to magic and too much can go wrong to fuck around. Do I hold airlines accoubtable for security? Sure. But this shit isn’t CSI:Cyber or Scorpion. He isn’t in the movie Blackhat. And his move was far far more blackhat than he thinks.
If you want to be treated like a responsible citizen act like one. Don’t expect to have special standards. Don’t think “oh they know who I am” whether they do or not like everyone should and that gives you a pass. It doesn’t.
I could see a 20 year old thinking this is okay (even though it is emphatically not) but seriously, Chris, you’re TWICE that age. I have been around as long as you have but even if I weren’t I would wonder what the hell made you think that was a brilliant move and that you deserve someone else to pay for your defense. At least acknowledge you’re at fault.
Pingback: Researcher who joked about hacking a jet plane barred from United flight | infopunk.org
Conundrum earlier summarized the issues in clear outline. Ultimately it is the same issues whether we are talking about cars, planes, trains, natural gas pipelines, or chemical plants. The industrial security community has been sounding this klaxon for many years with little response. Some have even taken to popular fiction in the hopes of getting the public’s attention (e.g., the recent Flight Track novel about a digital hijacking or Web Games, which anticipated stuxnet-style attacks.
The biggest risks in the airline scenario are not even from onboard access but another level of attack via internet links, the details of which have yet to be disclosed or discussed. All aircraft intrusion scenarios are extremely unlikely, but they are also highly tempting to certain parties, which makes it only a matter of time before the intrusion is not from a bonafide security researcher.
Do you believe Chris’ research is real-world applicable?
The work that Roberts, Santamarta, and others has real-world implications even if the specific vulnerabilities identified so far and their scenarios for use are only remote possibilities. Knowing something is there increases the chances of finding it. What terrorist group would not love to be able to hack into aircraft and bring them down. Most groups will not have the sophistication to work the hack themselves, but the wealthier ones can buy or hire what they lack themselves. And then there’s the ransom scenarios.
AS far as I am concerned, it is not about whether such things are likely to happen but about designing critical systems right in the first place, not cutting corners by putting everything on the same buss or leaving bridges intact or making everything full-time accessible to (from) the Internet.
I no longer consult actively in this area, but my fiction (e.g., Flight Track) is about precisely such potentials. Like Roberts, I am just trying to get public attention on issues that need to be fixed.
–Prof. Larry Constantine (pen name, Lior Samson)
This in no world fits a least harm possible standard. Tom (tqbf) Ptacek – who also has consistently and for decades (been around for a long time, as I have) spoke directly to this in the ycombinator thread on this subject so I won’t reiterate his points; we think a lot alike about this entire debacle. I highly encourage you to read what he wrote.
One thing that drives me nuts about so many “pentesters” is theur utter and apparent inability to understand that not all consequences are intended, especially when it comes to “testing”. In fact from a fuzzing standpoint, it is rarely the bugs we think we find that can cause the most damage. It is often an idiosyncrasy that can cause the most harm. There are a few great books out about this. For a real world example look at the Challenger disaster (not comparing the incident, comparing the investigation): it took Feynman a simple experiment with an O-ring to prove little things not totally understood can have major ramifications when it comes to safety.
I am arguing so much n this thread because people need to realise not having a standard set of ethics is ridiculous. I am not arguing for special status. I am arguing AGAINST special status. Which means people need to think about what they do before doing it, respond appropriately when somebody doesn’t (especially one’s own peer group), and take responsibility if they do fuck up. And by that I don’t mean excusing it either. Trust needs to be earned.
Earning trust, btw, Chris, if you’re reading this, doesn’t mean passing TSA pre-screening. If anything you sort of prove pre-screening has no ability to predict a lack of judgment.
Sorry. This is a lesson that white-hats need to really learn, since this isn’t 1999 anymore and these “lessons” have already been learned the hard by others for going on two decades now.
Don’t joke on the internet about vulnerabilities that could be taken to imply a threat. Its really that simple. If you want to? Fine, but understand that the Alphabet agencies will be around shortly, they will seize your gear, detain you, your name will be leaked to the press, your reputation damaged, etc, etc, etc… None of this is new territory. Its old. Way, way old.
With that being said:
Companies that run critical infrastructure need some sort of responsible disclosure mechanism so engineers who either discover- or just ‘realize’- some major flaw about their system can let them know without having to endure the ensuing indignity of being ‘investigated’ by hysterical cops who struggle comprehending that someone who discloses something is no threat. There are probably a ton of vulns out there that people just don’t bother disclosing because they don’t want the BS drama it would bring into their life.
Awful, awful way to go about things.
Pingback: ste williams – Security researcher barred from United Airlines flight after hack tweet
Pingback: Hacker Detained by FBI After Tweeting About Airplane Software Vulnerabilities. | Tfun
And now Wired is taking everything Chris says at face value, down to the amount of time he was questioned.
I am confused… what part of connecting to in-flight systems repeatedly, and without authorisation, on flights he is on as a pax — and he flatly ADMITS to doing both in the Wired article and to the FBI itself (in the past) — is legal, exactly?
What the hell is wrong with you people?
Does being “exasperate” serve as an excuse now for everything?
exasperated rather
Pingback: Researcher who joked about hacking a jet plane barred from United flight | TechDiem.com
Pingback: Du danger de plaisanter sur la sécurité des avions | Le Diligent
Pingback: Die Ohren des FBI fliegen immer mit | digichonder.ch
Linking this does NOT imply that I think people do not or cannot change. I emphatically believe they can and that our duty in life is to constantly better ourselves and the world around us. That said, this article speaks further to a history of him lacking common sense:
http://m.bizjournals.com/denver/print-edition/2011/01/14/breaking-and-entering-part-of-the-job.html?page=all&r=full
Note many of us who were around a long time ago were experimental back then (before the internet became connected to everything and everything was on the internet). But there’s a massive lack of judgment evidenced in this article that he no doubt thought was good press – the stuff with his father for instance – but most egregious of all was his not having the common sense to realise… oh do I even need to say it? The funny thing is I don’t have a personal grudge against Chris, per se. I have a grudge against a lack of decency, common sense and ethics. I don’t care who it is. The issue for me isn’t just how messed up this instance is. Or how he is contributing to it. People rally around stuff because they want to be part of something. Or overrelate.
He wasn’t “targeted” for being a security researcher. What those of us who’ve been in the field long enough to know how shit works can predict though is that HE WILL CONTRIBUTE to MAKING security researchers be seen as a threat – to security – and thus cause a threat to our liberty. It already started. Why give ammunition and evidence by refusing to exhibit rational thought? Lulz?
Pingback: Hacker on a Plane: FBI Seizes Researcher's Gear | The Security Ledger https://securityledger.com/2015/04/hacker-on-a-plane-fbi-seizes-researchers-gear/
The BizJournals link provides insight into where Chris Roberts came from and what he is about. For whatever reason, he has chosen to be on one side rather than another. At least he is not using his talents and temperamental leanings to steal money and bring down planes. There are many ways people with a taste for adrenaline and deception can put these to good use. For my part, I write stories of intrigue and adventure rather than act them out as Roberts does. Most of his work is at the request of clients, which in my view completely legitimizes what he does. The on-board stunt would seem to be an exception, but I do not see this one action as spelling the end of freelance security research. Like all whistle-blowers, he took chances and pushed the envelope. If the airlines and OEMs are jarred into wakefulness because of the public spotlight, all the better.
–Larry Constantine (pen name, Lior Samson, author of Flight Track)
People who become self-styled whitehats to do what blackhats do with impunity do not have the interests of your security at heart. Nor do gov agencies who recruit them, or companies which think it is ok to experiment on other peoples’ systems without consent. At best that is greyhat, and while greyhat occasionally has its moments, those moments are very very easy to bend past the point of acceptability; in this case I think it goes further than that. Did you really look at the language in that article?
Whitehats, to be good, need to likely think like blackhats to protect things… but not act like them. Or break the barrier between protecting and potentially harming. A lot now want to play both (ask me how many of these whitehats I saw cheering chaos in 2011 and supporting the very things that’d turn out to be federal operations to entrap hackers; the lines are not as clear as they should be. While I am not condemning it, I keep seeing instances where the people “normal people” rely on the protect them are basically believing themselves impervious to the law because, label. But label doesn’t mean anything. Ethics should mean something (and I mean that about the gov not just non-gov types). There are no enforced norms about what is ok or not ok. There are no in-group consequences shuttling egregious oversteps of ethical considerations. And so the feds have the ammo they need because there are no reasonable boundaries.
You are all being ridiculous. First of all to show you how ignorant Chris Roberts is: 1)the 737 fleet doesn’t even have an EICAS system onboard. 2)Oxygen mask auto deploy is not digitally controlled, it requires an actual pressure sensor switch to see cabin pressure altitude to climb above a predetermined and physically set, set point. No software involved in this system to hack. More to the point how do any of you, including Mr. Roberts know that Boeing, Airbus, the FAA, and the airlines haven’t made use of both internal and external security specialist to review their designs. By the way most WiFi systems installed by the airlines are not designed by Boeing or Airbus, but they all do require FAA oversight and approval. Of the onboard WiFi systems I am personally aware of (several), they have no digital tie in to the Aircraft systems that can be used to access/program or even talk to flight systems what so ever. In addition on a Boeing Aircraft the pilots yoke and rudder pedals have full, final, complete mechanical authority over the aircrafts flight controls. the autopilot or any other system of the aircraft cannot, I will repeat, CANNOT fly the aircraft against the pilots physical inputs. I am not familiar enough with the newer Airbuses to make the same statement about the Airbus but I would think so. If and when someone integrates the aircrafts digital systems into some form of outside access that does not require direct physical interface with the aircraft’s systems (i.e. WiFi updates,etc) then you will have something to worry about. but right now to my knowledge on commercial aircraft used in the western hemisphere that is not the case.
Befuddled,
I agree with much of what you are saying. That said, he (supposedly) was splicing into actual hardwired cables, not the wifi. He is conflating things for press. My point is regardless of whether there was or wasn’t EICAS on board, either he is a total liar and misrepresenting things while incidentally accessing things he would have no right to do (or not, and lying about that to the FBI and news stations too) or he is ignorant of what he proclaims to be an expert of and doesm’t know it (my money is on a split here but not sure what precise percentages are since he is so vehemently attempting to control the narrative and get sympathy and the feds won’t go on record yet – one reason I suspect he was doing hings he shouldn’t have been and no ethical researcher would have – and that indictment land is soon to ay him a visit (fed MO)).
He is dangerously incompetent, either solely from a common sense standpoint or both common sense and technical standpoint. As I have not had the luxury of getting my own large jet test flights with free reign to attempt to hack them even on the ground, and he certainly didn’t midair, so much of the specifics are moot. They matter but they miss the point, which is he had a long history of endangering others, regardless of what the system was.
To use a reasonable man argument, the reasonable man seeing his tweet and having no context, would likely be disturbed by his tweet alone. In a midflight 737. That’s not even screaming fire in a crowded (security) theater… it is screaming fire in a crowded (security) theater that is thousands of miles in the air, and reliant on people acting civil. Panic alone can still bring down airliners. So hypothetically can splicing into a wire on a flight. Tho I have no interest in proving that by hopping on a jet, tweeting about it to get press after being questioned by feds for doing so in order to garner pre-indictment support and/or business, etc, after having actually done it twenty or so times already.
I would be delighted to hear more on your take of this from a non-wifi perspective if you’re game and willing to discuss this more thoroughly. I can even accept being corrected. What bothers me is how few people are evwn asking the right questions and operately purely from an emotional, tribe mentality. The more I think about this the more I wonder if flighttalk oughtn’t have a thread on this (tho they might by now already; I am behind on my forum reading).
Befuddled is right about the systems in the older 737 but wrong about 787s (and recent Airbus models). In these fully fly-by-wire systems, the pilots do not fly the plane; the computers do. The positions of the flight controls (yoke and peddles or side-sticks) are merely inputs to computer programs. There is no direct “mechanical authority” associated with these controls.
As to the ability to hack through Wi-Fi into the avionics, this has been actually demonstrated. The particular vulnerabilities are varied and subtle, involving shared routers, crossover points for diagnosis, common wiring harnesses, etc. Boeing et al. no doubt have their own security consultants, but then so does Microsoft, and yet new exploits are being devised and uncovered all the time.
The holes in the security of on-board systems are serious enough and established enough for the GAO to recently issue a report calling for action on the part of the OEMs. The fact that avionics subsystems, entertainment, network components, and Wi-Fi systems come from different vendors is part of the problem as it makes back-door access, software sloppiness, and crossover points all that much harder to identify and eliminate.
Whether Chris Roberts is competent or not or acted ethically or irresponsibly is not the primary issue. None of that has anything to do with the fact that commercial aircraft are vulnerable to digital hijacking. Roberts tweaks the noses of the authorities, Santamarta and others demonstrate actual penetration schemes, I write novels to get people thinking. It’s all part of a process to draw attention to a serious problem.
–Larry Constantine (pen name, Lior Samson)
We get you want us to read your book by now btw; you detract from your statements by plugging it. Wanted to say that first; it isn’t an attack but a suggestion. It is harder to take things at face value when an agenda may appear to exist. And you do have decent points, though I do not agree with all of them.
First off, I am going to try to modulate my response. I am sure by now stcking my nose this far into things has made me “interesting” and I can live with that but there’s no point in tweaking noses either.
In flight wifi is THEORETICALLY capable of this, and theoretically so only on certain birds. IOActive (not a fav company of mine but credit where due) has said there are HYPOTHETICAL weaknesses they may have found a couple years back, which they tested only in their lab, and presented at BlackHat. This is one reason I framed my question as I did earlier about real world applications. Hypotheticals are not real-life examples. They are hypotheticals. If I hypotheticise that I can hack into NASA (FBI: I am not nor would I thanks) that wouldn’t give me the right or privilege to try to prove it can (or cannot be done). Ego should NOT control this space.
Everything – EVERYTHING has weaknesses. And you don’t need to be anywhere near a flight to hack into OnStar, INMARSET, or any satellite system (*not that I would be willing to prove this but that is my point). Everything is vulnerable to something given extensive parameters to work with. FDE is great til you get cold boot attacked or evil maided (or your prng is deliberately weak). All the HIPAA laws innthe known universe cannot save you from a stupid employee. All the opsec in the world cannot protect you from backdoored firmware baked into the chip. All the fearmongering in the world can’t ever truly prevent other people fucking around with any technology because every tech has weaknesses, be they code, infrastructure, network stardards and connectivity, people, or any of a thousand other things.
Only a fool would believe there are no weaknesses in ANY tech, even if those weaknesses are edgecases resulting in real world versions of bsods or kernel crashes (or even faulty wiring).
What if, since you seem to be American, one framed 9/11 as a bunch of guys aiming to prove you can take over jets using only boxcutters, and called themselves ‘security researchers’? I choose this example, crude as it us, to make a point. One doesn’t need to proclaim themselves a terrorist to generate bad laws and propagate terror based on hypotheticals. The world as it exists right now hangs on so many threads. People need to choose their heros and causes wisely. If not everyone will get clobbered by the quite game theory derived rule of sunk costs… and create the very world they say they want least.
I am all for research and PROPER disclosure to appropriate organisations. But this sort of thing is more like saying “woohoo I have boxcutters on a flight”. It doesn’t matter if your intention is to rack up tweets. You’re bringing about the very police state you fear. Stop thinkinh they think like you do. Exercise some strategy. Put yourselves in THEIR mindsets. Extrapolate at how useful unethical practices of ethical research can be used against you. Learn to network instead of expecting their hero worship.
And quit thinking networking means blind support. It doesn’t.
And I wasn’t kidding about the sat systems. But the same could be said about intercepting ground to air comms… or any of a hundred other scenarios. By proclaiming shit like this you just create the shortest path to the most chaos.
Honestly people dom’t NEED in-flight wifi or mobile phones in the first place, anyway. Sometimes I think one of Dantes levels of hell should be reserved to people who use up allll their neighbours diminishing leg space and mental space by yapping on phones, playing games full-force, and generally being self-centered entitled brutes. There is a time and place for some of this but things have gotten ridiculous.
Hmm…I think that we’re being rather tough on Chris Roberts here. The fact is: he did do responsible disclosure to the companies involved (Boeing, Airbus) and they – as far as we know – haven’t taken any steps to address the issues he raised privately and in public. That could be because there is no threat – that the attacks are not practical and therefore don’t need to be patched. But if that is the case, then the companies in question should probably make a statement to that affect. I think its possible to find fault with how Mr. Roberts did his research or the way in which he brought it to light. The fact for airlines, carmakers, smart appliance makers, critical infrastructure providers, however, is the same: you are all software companies and are now a part of the same vulnerability/patch “ecosystem” as companies like Adobe or Microsoft. They also battled furiously – for years – to try to shame independent security researchers into disclosing “properly” (that is: quietly and in private). In the end, however, the vulnerabilities that they expected to be given for free (and without embarrassing press) turned out to be salable commodities on a global market (black, grey and white). Now they simply do what the market dictates: they offer bug bounties and pay $$ for the vulns, then patch and disclose them promptly. Boeing, Airbus, etc. will soon find themselves in the same position – both paying for the information that folks like Roberts offer and keeping the public (or at least the Feds) abreast of the status of any exploitable holes affecting critical systems. My 2c.
(True) posit: hoods of cars can be easily popped. Equally true posit: brake lines (or radiator hoses or (insert here) can be cut). These are vulnerabilities the way Chris jacked into a wired network. Why are you not outraged at this? What’s more most automotive vehocles now are computerised to such an extent that they are heterogeneous as all get out between models.
Would you be outraged if some bus mechanic “joke tweeted”they were working on a passenger bus and ‘found the brake system… what shall I do with that? :)’? What if it were the irritating guy down the street who delivers pizzas and has the same equipment? What if it were a ten year old brat? What if it was just some 16 year old with a pair of wire cutters? What if they had the equipment and just walked up and down the street popping hoods to everyone’s car, attaching their diagnostic systems, maybe tweaking around to see how the cars are all different.. or buses… or whatever.
Now imagine the same situation thousands of feet in the air, with hundreds of people on board, and zero control. Did he have ANY right whatsoever to plug inti ANYTHING om that plane without express permission?
Here’s a clue: no pemtest client in theur right mind would ever ever ever ever ever ever permit this in ANY way under ANY scope. This isn’t a software bug, but he may have found some and crashed the plane or started a massive panic if he was unlucky – or maybe just panic is lucky given the alternatives.
People aren’t being too hard on him. They are overly supporting his irrespomsible actions that could’ve got someone killed and WILL wind getting ACTUALLY ethical research chilled and even non-fame-whores held suspect, as well as creating broadly wriiten punitive laws will like all punitive laws be stretched to serve agendas. The feds aren’t taking away his rights. He will help get ours taken away though. Especially this year, the way laws are going.
Also, does he expect noone to be flying for years til all the planes are “upgraded” to his liking? If it’s really that dangerous why does he fly so much?
Quit supporting him. He will make all of us illegal. As I have stated again and again, with power comes responsibility.
ps: “Now they simply do what the market dictates: they offer bug bounties and pay $$ for the vulns, then patch and disclose them promptly.” is one of the most idealistic and credulous statements, ever. The people who really pay do NOT patch things,,, or inform the vendir… and the sellers rarely know eho thungs go to. Even if it is NOT patched, blackmail NEVER becomes the ethical answer.
Well – its simply a fact that vendors (including Adobe, Microsoft) offer paid bounties for vulns and have verbose and transparent disclosure (albeit: after alerting major customers and downstream partners). I’m not sure how that is “idealistic and credulous” its just a statement of fact.
One place offers you 1000$ for weeks’ of work. Another offers you 50-200x as much, via a ‘trusted intermediary’ who sells these to ‘trusted parties in the “whitehat” community.
See also: kitchens.
Idealism is dangerous.
“Whether Chris Roberts is competent or not or acted ethically or irresponsibly is not the primary issue. None of that has anything to do with the fact that commercial aircraft are vulnerable to digital hijacking.”
And that is so off-base I just wanted to leave it hanging there. Give me logical rational explanations of why it is not at all important. Incompetence is incompetence. It never ends well and usually ends with people on a terrible terrible path by following it… later they wonder how they got there. And I am trying to explain that now, ahead of time, though history will bear this out. People are never believed til they are proven right Then they’re despised for not being wrong like everybody else. You seem like a person who wantscpositive change. It doesn’t come from believing the groupthink pack. It comes from really sitting down and mapping out, over days or weeks if need be, exactly how the flow charts of sll of these actions might play out.
>> Still, he questioned why the agency was following the social media posts of a security researcher closely enough to track down his flight in real time and apprehend him.
NSA is scanning everything, everyone is being watched.
While this is true, this is not why. Think for a minute.
He was on his way to give a presentation to feds and other people. He has been doing this for years. No doibbt his twitter handle is on the top of his slide deck. No doubt feds followed him. This wasn’t a DM or any kind of private message. He was already under investigation as is and no doubt he was watched by them too. But 99,99% it was one of his twitter followers, who was probably also a fed, or maybe someone just with a TSI clearance… or just a normal peeson who followed him and realised what a totally dangerous line he crossed.
There are enough real conspiracies against citisens and non-citisens alike nowadays. Do not feed into false extensions. You weaken the message, not strengthen it.
(ps: weakening the message is what they want)
Pingback: Episode 36 | Gun Blog Variety Cast
@not a police state moppet – My agenda in fiction is pretty simple: get people thinking and raise public awareness of real issues. But I won’t mention the book again. 🙂
You are right, of course: every complex system has vulnerabilities and security gaps. The issues are how many, how big, and what are the consequences if the defenses are breached. Attractive, high value targets with lots of holes or ones with digital welcome signs are particularly important to secure to the best of our ability rather than playing semantic games of denial and diminution. Or shooting the messengers.
Frankly, I am less worried about on-board hacking of aircraft than about the ease with which gas transmission pipelines can be remotely hacked. And, yes, I’ve written about that, too, but won’t mention the book. 🙂
In both cases, I would hardly call the vulnerabilities “theoretical,” since actual attack scenarios have been demonstrated. As more and more of our communication, transportation, and energy infrastructure and more and more of our everyday physical environment is fully computer-controlled and fully connected 24/7, the vulnerabilities multiply along with the temptations.
This is not scaremongering. I don’t think many of the security researchers and consultants are saying, “Watch out, digital hijacking is an imminent threat,” or “Hackers are soon likely to blow up the pipelines going into Manhattan.” The message from most is about prudent action. In a typical suburban neighborhood, the odds of theft may be low, but it is still prudent to lock doors and alert the local police while you are away on vacation.
There may be conflicts of interest and financial agendas on all sides. Security companies and consultants make money on their services and products, so drawing attention to gaps is in their interest. Boeing makes money on its planes and makes even more money (in the short run) if it doesn’t have to fix problems with low probability of occurrence, so deflecting attention or minimizing risks is in their best interests. And, yes, I make money off my writing, although we are talking about chump change compared to what I made as a design consultant. Like many “missions,” it is essentially not-for-profit. Still, we all do our bit in different ways. You, too. 🙂
Will reply tomorrow, just pinging the thread so you know to check again then in case you have follow-ups on notify.
Sorry, lots of work. Need to be brief.
You wrote:
“Frankly, I am less worried about on-board hacking of aircraft than about the ease with which gas transmission pipelines can be remotely hacked. And, yes, I’ve written about that, too, but won’t mention the book. 🙂
In both cases, I would hardly call the vulnerabilities “theoretical,” since actual attack scenarios have been demonstrated. As more and more of our communication, transportation, and energy infrastructure and more and more of our everyday physical environment is fully computer-controlled and fully connected 24/7, the vulnerabilities multiply along with the temptations.”
… Reminds me of Clarke or Schwartau circa the 90s… the fact of the matter is that generally this stuff doesn’t happen unbidden in a society that isn’t completely off the rails. Most people in the world are far more interested in protecting themselves and their families and maybe retaliating for gross oversteps of power and impinging upon their autonomy. They aren’t sitting around plotting things like this for several years. That’s hardly strategic or expedient. Point of fact, there is no need to be ‘creative’ to cause harm, but once the work is done and made public, the work is done and you just add to the arsenal of what is relatively easy, while increasing FUD dramatically.
In smaller ways this can be like publicly releasing a wordpress or magento or kernel local (or exim remote, or what have you). Metasploit at any time, and Havij (and sqlmap while somewhat less user-friendly) are a pretty good exemplification that making it ea
Oops…
Are pretty good exemplifications that making things easier make things more common and even mundane, and desensitise people to the results of the thing in the first place… instead of getting in it becomes a numbers game – and trying to out mass scan faster than everyone else to own the most blah. It is the desensitisation that ultimately winds up being far more dangerous than even the publication of exploits for fame or profit (yeah tell yourself it is to fix shit, the Society of the Spectacle likes statements like this too). Then, when it is used, you get the ego syntonic result of being able to say “I told you so”… only the problem is, you told them how to do it.
Doing the work is WORK. And for those NOT living in the 303, being an American Whitehat CTO who gets paid to tweet and do “original research” on avionics (or pipeline) equipment THEY do not even have access to legitimately… that is a luxury even a lot of *whitehats* do not have the resources to do. Roberts said it took years. And sure some people have years to work on hobbies but one thing DOING the WORK usually inadvertently teaches those to whom it brings great hardship is *wisdom*, at least in part.
I coukd go on but I won’t.
Mr. Moppet seems to be looking for attention.
Pingback: Χάκινγκ εν πτήσει; Ούτε γι' αστείο! - Hack Slot Entry
Pingback: Federal Affidavit Alleges Researcher Hacked Planes In Flight | The Security Ledger
Pingback: Computer security expert claims to have hacked plane’s sytems | The Red Pill Blog