
In-brief: A new company, PFP Cybersecurity, says it can detect malware infections almost instantly by analyzing changes in the way infected devices consume power. The company is targeting industrial control system and critical infrastructure with new products.
Everybody knows that anti virus software isn’t doing its job. Or, at least, it isn’t doing the job that most companies want it to do: spotting malicious software – all of it.
The question is: what technology can do that, and across the myriad of endpoints that need to be secured: SCADA and industrial control systems, connected infrastructure, Internet of Things, and so on.
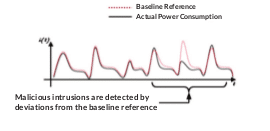
Last week’s S4 Conference in Miami included a presentation by one company that thinks it has the answer – or at least the beginning of an answer: PFP Cybersecurity. The Vienna, Virginia-based company that will announce a product next week that it says can identify malicious software infections and other abnormalities on critical systems by observing fluctuations in their power use.
The company grew out of research funded by the U.S. Departments of Defense and Homeland Security. It says its anomaly detection technology can do what antivirus software can’t: instantly detect the presence of malicious software by monitoring the way that software changes the patterns of power consumption or RF (radio frequency) radiation.
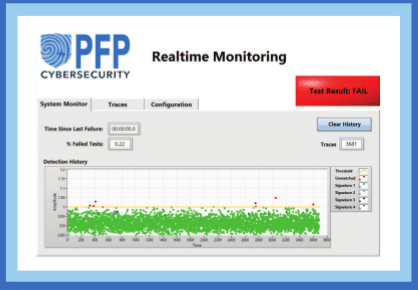
The technology has many applications: from detecting Stuxnet-type attacks on critical infrastructure to identifying counterfeit hardware and low-level software used in critical systems used by government, industry and the military.
The PFP solution includes P2Scan, which combines a small, hardware sensor that is deployed within the device being managed with a back-end management and analysis engine. For most deployments, the sensor needs to be physically implanted within the chassis of the hardware it is monitoring. For example, it might be glued onto the exterior of a CPU of a critical system. Once deployed, the sensor monitors the performance of the hardware and establishes baselines for power consumption.
Jeff Reed, the founder and president, says that the technology can spot infections at the instant they occur, rather than weeks or months after the fact. Malware like Stuxnet, for example, produces a noticeable change in the power use of the infected system that is well differentiated from its normal operating state.
Ideally, PFP would like its technology to be embedded with chips by manufacturers like Intel. It would add only modestly to the cost of manufacturing the chips and make the power monitoring capability available to anyone, said Thurston Brooks, PFP’s Vice President of Marketing.
The company is also developing a product called eMonitor. That is a rack mounted appliance that is intended for use in industrial control system (ICS) environments and that monitors SCADA and ICS systems for malicious or suspicious activity in realtime. For example: the company can map the unique power signature associated with each, distinct set of “ladder logic” within a programmable logic controller (PLC) of the type targeted by Stuxnet. If any of those paths is corrupted or subverted, the PFP technology would detect it immediately, said Steven Chen, PFP’s Executive Chairman.
The advantage of the PFP technology is its ability to work across different hardware and software platforms. Unlike traditional endpoint protection products, it is platform agnostic.
[Read more Security Ledger coverage of SCADA and ICS security.]
The weakness of the technology is that it is less effective monitoring more complex and varied systems such as laptops and desktops, where the unique – and changing- mix of hardware and software components makes it more difficult to baseline power consumption accurately enough to detect anomalies, the executives conceded.
Still: there are plenty of specialized applications in need of anomaly detection to keep PFP busy. The company is engaged in a Department of Energy trial to monitor relays and PLCs from Schweitzer Electric at the DOE’s Savannah River National Lab facility. Those are part of a DOE grid modernization project, Brooks said.
Progress to secure industrial systems has been slow, despite a steady drumbeat of warnings from security researchers about the danger of malware and cyber attacks. Among other presentations at the S4 Conference was one that showed how attackers are adapting banking malware to attack industrial control system software. Kyle Wilhoit, a senior threat researcher with Trend Micro, claims to have found 13 different crimeware variants disguised as SCADA and industrial control system (ICS) software. The malware posed as human machine interface (HMI) products, including Siemens’ Simatic WinCC, GE’s Cimplicity, and as device drivers by Advantech.
