It’s another day, another face-palm moment for the home surveillance camera industry.
Just one month after the Federal Trade Commission (FTC) settled a complaint with the maker of SecurView, a line of poorly secured home surveillance cameras, a researcher at the firm Duo Security has found a slew of even more serious security holes in the IZON Camera – a popular product that is sold in Apple Stores and Best Buy, among others. A review by The Security Ledger found dozens of such systems accessible via the public Internet, in some cases allowing anyone to peer into the interiors of private residences and businesses.
Mark Stanislav, the Security Evangelist at the firm Duo Security, presented the details of a security audit of the IZON camera at a security conference in New York on Tuesday. Stanislav documented troubling security lapses including a wide-open configuration with exposed ports for accessing the device by Telnet and HTTP. IZON also used unencrypted communications and video streaming to and from the devices and an undocumented and hidden username and password for each camera’s Web backend that could allow a remote attacker to spy on the camera’s owner.
He presented his findings at the Rochester Security Summit in Rochester, New York on Tuesday. In an interview with The Security Ledger, Stanislav said that he discovered the problems with the IZON camera while performing a nmap scan of his home network in search of a recently deployed Raspberry Pi device over the Summer.
“I saw this device with TELNET Port 23 open on the network and a bunch of other weird ports,” he said. Being an information security professional, he decided to investigate and ended up identifying an IZON camera that was deployed in his living room as the culprit.
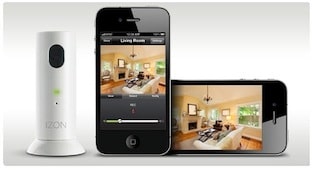
IZON is an iOS compatible device that’s manufactured by Stem Innovation LLC, a Salt Lake City, Utah company. The linux-based “smart” camera has the slick look and feel of Apple’s products and is sold in Apple Stores, as well as other retail outfits for around $130 per device. IZONs are powerful devices with integrated camera and microphone. They’re marketed for their easy integration with devices running Apple’s iOS operating system and for easy set-up and management. The cameras have motion detectors and other security features that allow them to issue alerts and capture short video segments which can be stored in the cloud for remote viewing.
Under the hood, however, Stanislav said the IZONs fall well short of the mark in protecting customers’ privacy. The lack of secure port configuration, including an exposed Telnet port, means that IZON devices that are not deployed behind a router could be visible and accessed directly from the Internet, with attackers having the option of uploading or downloading content directly from the device. A quick search using the hardware-focused search engine Shodan found 65 such devices online in July spread across a dozen countries, Stanislav said.
Stanislav analyzed the IZON mobile application running Version 1.0.5 of the company’s mobile application and Version 2.0.2 of the IZON device firmware. He found hardcoded and shared administrative (“root”) credentials buried in its application code. Those credentials would allow an attacker to log into any deployed IZON device as an administrator as a “superuser” and change the configuration of the camera, upload malicious code or disable the device, Stanislav told Security Ledger.
By abusing root access on the device, an attacker could also elevate the permissions of the user account to give that account administrative access to the device, he said. Finally, Stem does not secure video streamed from the cameras using RTSP (Real Time Streaming Protocol), meaning that anyone connected to the same network as the IZON camera could intercept video streams by carrying out a “man in the middle attack.”
An integrated web server that runs on the IZON device and is used to provide a graphical interface for the camera also poses a major privacy risk. The web server is configured with a hidden and easily guessed user account that allows anyone with access to the Internet or, in some cases, the wireless network the device is deployed on to log into the Web interface of the camera, view live video and audio collected by the device and view other configuration details, Stanislav reported.
Using the search engine Shodan.org, Stanislav compiled a list of scores of IP addresses of IZON cameras exposed on the Internet – some deployed behind simple DSL broadband connections. A review of that list by The Security Ledger revealed a handful of exposed Web interfaces that allow anyone with an Internet connection and knowledge of the default user name and password to take control of the camera: viewing a live video feed, making video recordings that can be automatically uploaded to YouTube or other cloud-based services, and even sounding audio alarms. In one case, the camera appeared to be deployed in a private residence in Kissimmee, Florida, where an elderly couple were seen caring for an infant. Others showed the interiors and exteriors of private residences – some occupied, others obviously vacant.
More concerning, the exposed cameras also expose longitude and latitude information that can be used to locate the devices.
In addition to weak device security, Stanislav found a number of serious problems with Stem’s implementation of video streaming and cloud-based management features for the IZON cameras. Specifically: Stem contracted with the firm IntelliVision, a provider of “Video Intelligence and Automated Monitoring solutions,” to manage video alerts captured by IZON devices. Stanislav said that Stem’s implementation of IntelliVision’s service is deeply flawed. The researcher said he discovered that videos captured by IZON “alerts” are lumped together, unencrypted, in a single virtual container on Amazon’s cloud. They can be accessed using simple HTTP without any authentication required to view a specific video, so long as the requestor knows the URL, including an MD5 hash value for the file he or she wishes to view.
“If you know the URL of one of these video clips, you can go to any computer and put the URL in and view that video,” he warned. Customers who use the iOS application to delete stored videos from Amazon’s cloud may also be disappointed: Stanislav’s research suggests that Stem does not actually groom videos marked for removal from their cloud storage service, Stanislav said. Furthermore, Stanislav found administrative credentials for Amazon’s S3 cloud service hard coded into the IZON mobile application, which suggests that Stem is using the same credentials for every customer account.
The issues raised by Stanislav are similar to those that prompted the FTC to file a complaint against TRENDnet, the maker of the SecurView home security cameras. The FTC alleged that TRENDNet sold “faulty software that left (the cameras) open to online viewing” by anyone who knew the device’s IP address.
Under the terms of a settlement with the Commission, announced in September, TRENDnet agreed to stop misrepresenting the “security, privacy, confidentiality, or integrity of the information that its cameras or other devices transmit,” as well as “the extent to which a consumer can control the security of information the cameras or other devices store, capture, access, or transmit.” The California-based company was also required to establish a comprehensive information security program to address security risks in its products and to obtain third-party assessments of its security programs every two years for the next 20 years.
Stanislav said that the FTC’s pursuit of TRENDNet should have been a red flag for other companies that make IP-enabled cameras and other sensors for the consumer market. “What the FTC took objection to was the collective amount of failures within the IP camera platform. It wasn’t one issue, but multiple issues that, collectively, caused a problem.”
Contacted by The Security Ledger, the FTC was not able to offer comment on the issues with the IZON cameras prior to publication.
Despite that, Stanislav said it has been “slow going” getting Stem Innovation to address the substance of his findings. He first contacted the company on September 6, with frequent e-mail exchanges to Stem’s support desk, CEO and CTO since.
Contacted by The Security Ledger, Stem Innovation CTO Matt McBeth said that the IZON firmware, server system and iOS applications tested by Stanislav have since been updated, and that the research contains “inaccurate and misleading information.” Stem did not provide specific information about any inaccuracies. But McBeth said that Stem Innovation take its customers’ privacy seriously. “We are committed to making IZON the very best IP camera system,” he wrote.