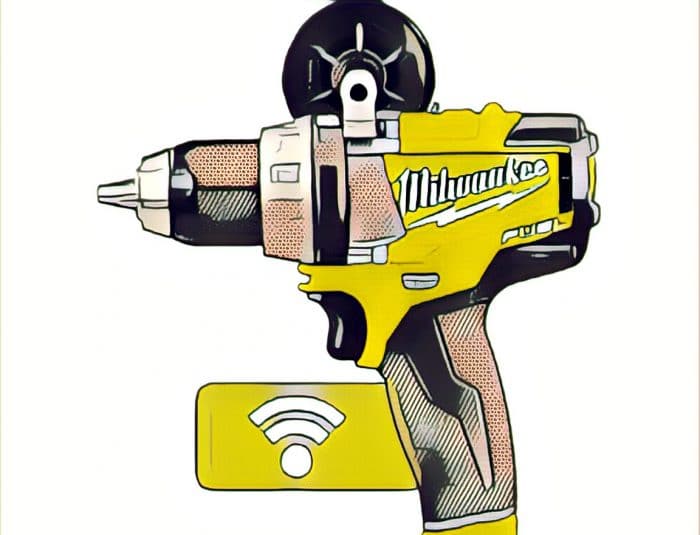
In-brief: Is there cause for hope? A new analysis of a connected power drill by a researcher at DUO Security finds that it’s actually pretty secure. But challenges remain for connected device makers.
Duo Security
State of the Endpoint: Vulnerable Software, Click-Happy Users
In-brief: a study of millions of mobile and desktop endpoints finds continued problems with out of date software and a willingness to fall for phishing attacks.
OEM Software Leaves New Windows PCs Vulnerable
(credit: Duo Security)
The next time you’re in the market for a new Windows computer, consider this: if it comes from one of the top five manufacturers, it’s vulnerable to man-in-the-middle attacks that allow hackers to install malware.
That’s the take-away from a report published Tuesday by researchers from two-factor authentication service Duo Security. It found third-party updating tools installed by default threatened customers of Dell, HP, Lenovo, Acer, and Asus. The updaters frequently expose their programming …read more
You’re Invited: A Conversation on Password Security and Targeted Attacks
A note to Security Ledger readers that I’ll be facilitating a really interesting conversation this afternoon on password (in)security and how weak user authentication can undermine even the best laid security plans. The SANS Webinar, Security for the People: End User Authentication Security on the Internet” kicks off at 3:00 PM Eastern today (12:00 PM Pacific). You can register to join us using this link. My guest is DUO Security researcher Mark Stanislav, a frequent Security Ledger contributor and one of the smartest guys out there when it comes to passwords, authentication and securing the Internet of Things. There’s plenty to talk about: weak authentication schemes are the root cause of any number of prominent breaches – from the recent attacks the Apple iCloud accounts of A-list celebrities, to the breach at retailer Target (reportedly the result of a phishing attack on an HVAC contractor that Target used.) Mark and I […]
New Calls For A Common Hardware Vulnerability Database At Black Hat
The Black Hat briefings made its reputation as a forum for star security researchers to unveil hair raising vulnerabilities in hardware and software. But Black Hat has become a more corporate event and collaboration is much in evidence these days. The latest example: the first roundtable discussion ever held at Black Hat. Speaking on Wednesday, Don Bailey, CEO of Lab Mouse Security, and Zach Lanier, Senior Security Researcher at Duo, facilitated a lively discussion of embedded system security before a group of attendees arranged around a table with a few more chairs off to the side. Bailey asked the audience to start the conversation, and he and Lanier then moderated the discussion. The conversation started with discussion of new secure chipsets, such as ARM TrustZone, and the fact that few institutions are using them. One factor is cost. Some organizations are gravitating toward open source chipsets such as Ardinuio, which […]