The compromise of device maker Asus Live Update Utility is just the latest evidence that sophisticated attackers have software supply chains in the crosshairs.
Tag: supply chain
Report: Chinese Ties to US Tech Firms put Federal Supply Chain at Risk
China poses a serious and immediate cybersecurity threat to the federal supply chain in part because of connections Chinese state-owned enterprises (SOEs) have to key tech companies working in the government sector, a report recently issued by the U.S. China Commission has found.
Iran Taps Chafer APT Group amid Civil Aviation Crisis
Iran’s Chafer hacking group is targeting aviation repair and maintenance firms in an apparent effort to obtain information needed to shore up the safety of that country’s fleet of domestic aircraft, according to research by the firm Symantec.
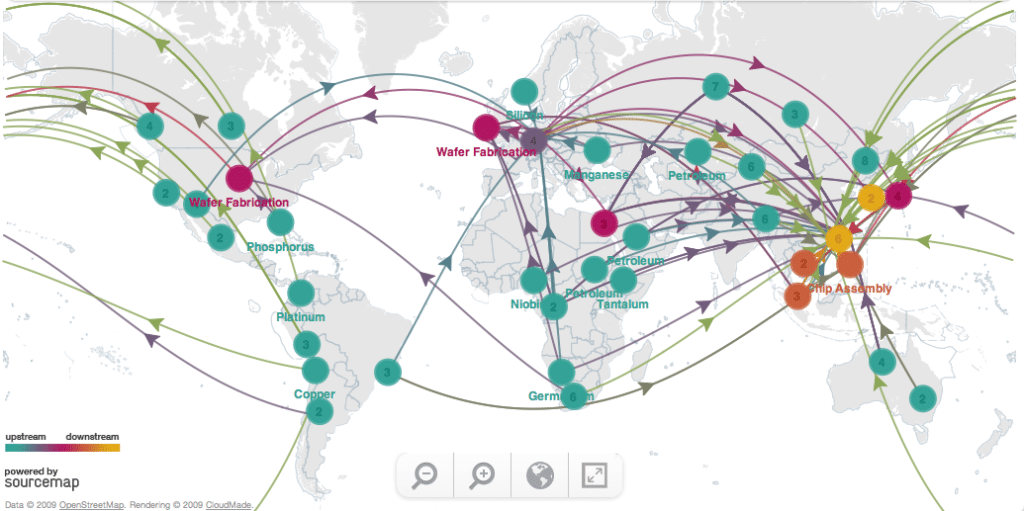
Software’s Sausage Factory: The Supply Chain
In-brief: Experts warn that supply chain insecurity run broad and deep, threatening the security and integrity of technology dependent organizations.
Another Supply Chain Mystery: IP Cameras Ship With Malicious Software
In-brief: The discovery of a malicious link buried in software for a common IP camera sold on Amazon and other online retail outlets is just the latest example of supply chain based threats to connected products.