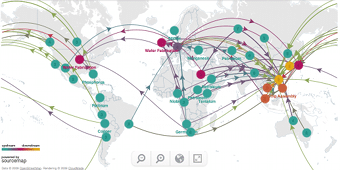
We live in an ever-more unstable world in which massive disruptions, whether natural or man-made, are a frequent occurrence. Companies that make everything from aircraft to mobile phones to cappuccino need to be nimble – sidestepping global calamities that might idle assembly lines or leave customers without their morning cup of coffee. As in other areas, the benefits of technology advancements like cheap, cloud based computing, remote sensors and mobility are transforming the way that companies manage their vast, global network of suppliers. These days, supply chain transparency is all the rage – allowing companies to share information seamlessly and in realtime with their downstream business partners and suppliers. Firms like the start-ups Sourcemap, and LlamaSoft are offering “supply chain visualization” technology that leverages a familiar formula these days: mobility, social networking, crowd-sourced intelligence, and “Big Data” analytics. [There’s more to read about supply chain security on The Security Ledger.] However, as […]
Tag: supply chain
Printable Smart Labels Warn When The Milk’s Gone Bad
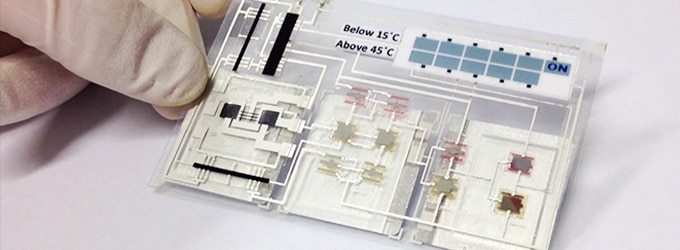
What’s been called “The Internet of Things” or “The Internet of Everything” is a revolution in computing that has seen the population of Internet connected “stuff” skyrocket. By 2020, there will be an estimated 50 billion devices connected to the Internet (or whatever its called then). Today, the list of IP-enabled stuff is already long: phones, automobiles, household appliances, clothing. But, under the hood, a lot of these devices really aren’t much different from the PCs that grace our desks. They have hard drives, CPUs, memory, input devices, and so on. Most are still assembled in factories by humans and machines. This can be done cheaply and, in some cases, automated. But it’s still a labor-intensive and expensive process. But what if you could just “print” working electronics like, say, The New York Times prints its daily newspaper (at least for now!)? That would change everything. For one thing: […]
Protecting Smart Cars And The Supply Chain From Hackers
One theme that frequently comes up in my conversations with experienced security veterans when we talk about security and “the Internet of Things” is the absence of what might be termed a “security culture.” That’s a hard term to define, but it basically describes a kind of organizational culture that anticipates and guards against online attacks. Certainly companies that have been selling software in any great number for any amount of time have had to develop their own security cultures – think about Microsoft’s transformation following Bill Gates Trustworthy Computing memo, or Adobe’s more recent about-face on product and software security. But that culture is lacking at many of the companies that have traditionally thought of themselves as ‘manufacturers’ – makers of “stuff,” but which now find themselves in the software business. Think General Electric (GE) or – even better – auto makers. A couple of months back, I had […]
Podcast: Made In China, Secured In The U.S.
We’ve written a lot about the threat posed by nation-state sponsored hackers to U.S. corporations and the economy. So-called “advanced persistent threat” (or APT) style attacks against corporate and government networks have been linked to the theft of sensitive data and intellectual property. Difficult as it is to stop APT attacks against networks, it’s even more challenging to identify threats one-step removed from direct attacks. Lately, attention has shifted to vulnerabilities in the supply chain of companies selling networking gear, servers and other critical IT components. Concerns about corrupted products from foreign suppliers were enough to prompt the U.S. Congress to hold hearings focused on the threat posed to government agencies by Chinese networking equipment makers like Huawei and ZTE. In this week’s podcast, The Security Ledger talks with Jerry Caponera, of Cyberpoint International. Cyberpoint is a Baltimore, Maryland firm that sells Prescient, a service that verifies where true vulnerabilities exist […]
AppSec And The Ghost In The Supply Chain
Tomorrow afternoon, Security Ledger, with help from our sponsor Veracode, will record its first video conversation. The show’s name: Talking Code (#talkingcode). The topic: application security, and – in particular – securing the supply chain. Joining me for the discussion will by Chris Wysopal, the co-founder and CTO of Veracode and Joshua Corman, the Director of Security Intelligence at Akamai Inc. Two things: you can send us questions or comments on Twitter. Our discussion will be filmed in studio, not live, but we’ll be tweeting comments live and engaging in realtime via Twitter. Just use the hashtag #talkingcode to pose questions. Say the term “supply chain,” and people immediately think of automobile and electronics manufacturers, who must assemble products from components makers scattered around the globe. These days, however, its not just manufacturers who have to worry about supply chains. Almost every company has a “supply chain” in one form or […]