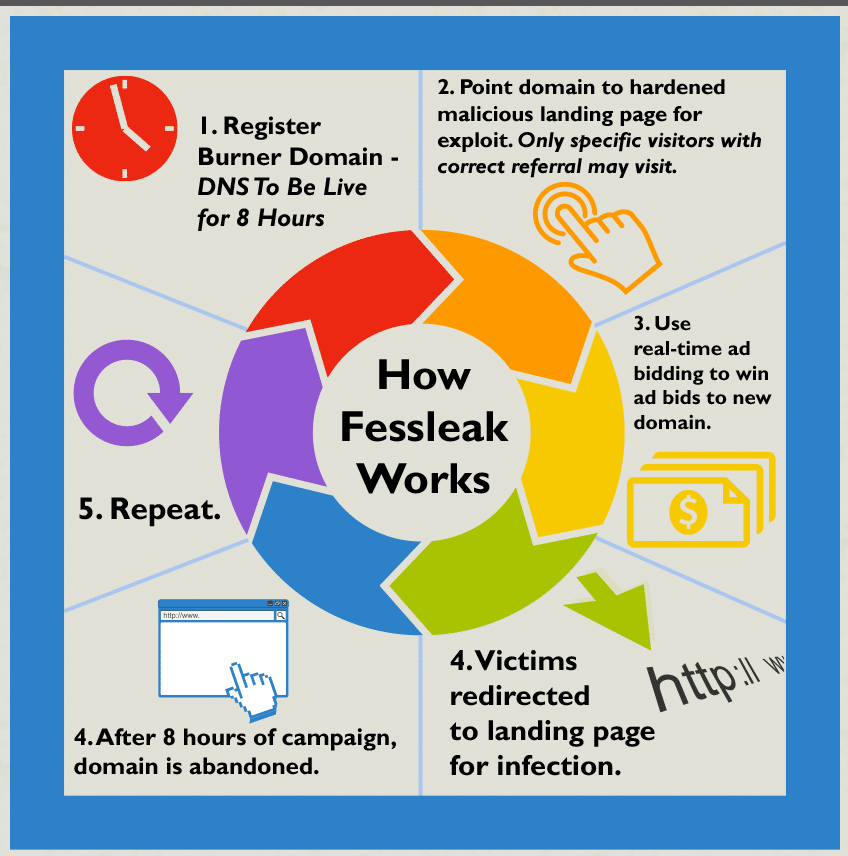
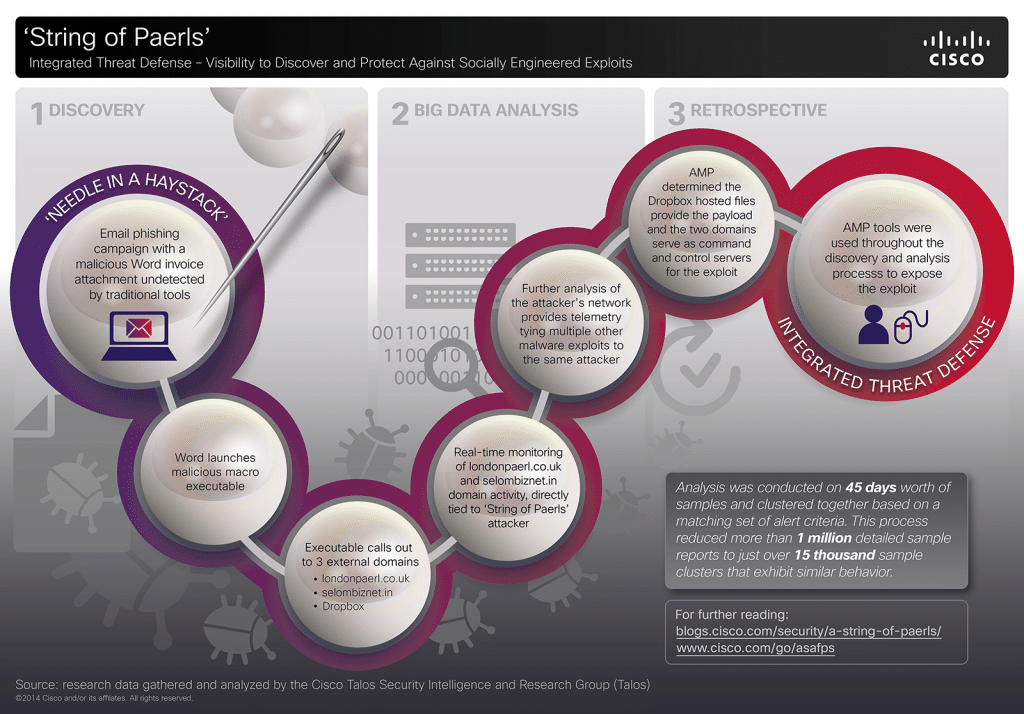
In-brief: A new global botnet is built on lightly secured home broadband routers in developing nations, according to a report from the firm Incapsula.
command and control
The Deadly Game of Cyber Mis-Attribution | Digital Guardian
In-brief: Tools to attribute cyber attacks are still primitive – leading to potentially damaging mis-identification. (This post first appeared on the Digital Guardian blog.)
New Ransomware, FessLeak, Taps Adobe Flash Flaws
In-brief: A new and sophisticated ransomware family dubbed “Fessleak” is spreading in malicious advertising (or “malvertising”) campaigns by exploiting newly disclosed flaws in Adobe’s Flash technology.
With Multi-Vector Attacks, Quality Threat Intelligence Matters
In the last year, the world’s attention has been riveted by a series of high-profile hacks of major corporations in retail, finance and the entertainment industry, among others. Each of these incidents is unique, involving different threat actors and motives. However, each of these attacks is also a sterling example of what we, at Cisco, term “multi-vector attack” that employs a range of technologies, deployed in numerous stages, to penetrate the defenses of the target organization. Here at Cisco, we have studied these attacks in-depth and have identified some commonalities among these multi-vector attack, and useful approaches to combat them. This blog post will discuss some of our findings. About Multi-Vector Attacks Any cyber attack, large or small is born from a weak link in the security chain. These weak links take many forms: poorly configured Web servers, gullible employees or vulnerable-but-common applications like Microsoft Office, Adobe Reader and Java are common examples. Multi-vector attacks […]
Regin Espionage Tool Active since 2008 | Symantec Connect
Symantec on Sunday published research describing a new family of malware that it claims has been circulating, quietly, for close to six years. (Gulp!) According to a post on Symantec’s Security Response blog, Regin infections have been observed as far back as 2008, but the malware went quiet after about 2011, only to resurface in 2013 in attacks on a wide range of targets including private and public entities and research institutes. Symantec also observed the malware used in attacks on telecommunications firms and say it appears the malware was being used “to gain access to calls being routed through their infrastructure.” In a separate research paper, Symantec describes the malware, dubbed “Backdoor.Regin” as a multi-staged threat that uses encrypted components – installed in a series of stages – to escape detection. The key the malware’s stealth is compartmentalization, Symantec found: “each individual stage provides little information on the complete package. Only by acquiring all five stages is it possible […]