Industrial control systems (ICSs) remain easy targets for nation-states actors because of security gaps such as plain-text passwords, direct Internet connections and weak anti-virus protections, a new report has found.
The warnings about industrial control systems running on Windows XP are becoming a thing of the past; ICS administrators seem to be catching on to updating legacy systems in the wake of NotPetya and the millions in financial havoc it caused. Still, there are some very obvious security flaws in ICS networks, according to the 2019 “Global ICS & IIoT Risk Report” by CyberX, an industrial Internet of Things (IIoT) and ICS security company.
“Many of these networks were designed decades ago when cybersecurity was not a primary design consideration,” Phil Neray, vice president of industrial cybersecurity at CyberXAs, told Security Ledger. “As a result, they are rife with ‘insecure by design’ vulnerabilities such as unencrypted protocols, legacy Windows boxes, vulnerable firmware in controllers–e.g., in embedded web servers–and lack of network segmentation.”
These vulnerabilities leave ICS networks wide open to attacks from nation-states such as Russia, Iran and North Korea, who are constantly probing them for weaknesses so they can establish footholds, he said.
[See also: Report: Hacker group behind Trisis Malware expanding Activity in Middle East]
“These footholds can initially be used for cyber reconnaissance, but could also be used to threaten us with destructive attacks in the future, depending on their geopolitical objectives,” Neray said. He noted that attacks by Russia against the Ukrainian electric grid and the TRITON attack on a petrochemical facility in Saudi Arabia–widely believed to have come from Iran–as key examples of this happening.
To find out where ICS sites are weak, the CyberX report analyzed real-world traffic from production ICS networks over the past 12 months rather than question security and IT professionals about the state of things, providing an accurate picture of current ICS security, according to CyberX. Data for the report comes from more than 850 production industrial control system networks across six continents. Companies in industrial sectors including energy and utilities, manufacturing, pharmaceuticals, chemicals, and oil and gas contributed to the report.
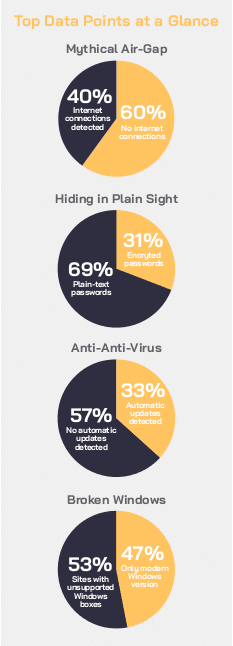
Obvious weak spots
Most of the key security gaps that researchers found on ICS networks are easily fix-able, CyberX found. Seventy one percent of industrial sites still lack encryption in legacy protocols in SNMP and FTP, and have plain-text passwords traversing the network. This exposes sensitive security credentials, making it easy for hackers to do some easy network reconnaissance and find ways to compromise the system.
[See also: FBI, DHS warn Russian Dragonfly Group Still Targeting US Critical Infrastructure]
Anti-virus protections were frequently neglected, according to the report, which found that 57 percent of networks aren’t running anti-virus protections that update signatures automatically, leaving those systems vulnerable to new and fast-moving malware outbreaks.
ICS administrators also appear to be too hastily pursuing digitization in favor of security, which means 40 percent of industrial networks also persist in having connections open to the public Internet. This provides an easy digital pathway for a clever bad actor, according to the report.
Ubiquitous wireless connectivity also leaves ICS networks at risk, with 16 percent of ICS sites having at least one wireless access point (WAP), which–if misconfigured–could allow access from unauthorized laptops and mobile devices. Moreover, sophisticated malware such as VPNFilter target access points such as routers and VPN gateways, which require further due diligence on the part of administrators to ensure these devices are inventoried and patched to mitigate threats.
The way forward
If exploited to the fullest extent, any of these threats could spell dire consequences not just for the performance of the networks, but the safety of those overseeing them and even the greater human population at large, Neray warned.
“The consequences include costly production outages, as we saw with NotPetya, safety failures leading to loss of human life, and environmental incidents leading to environmental damage–and lawsuits,” he said. “Also [at risk is] theft of intellectual property such as information about proprietary manufacturing processes. If critical services such as electricity and water are interrupted, we could see also fear and chaos in the civilian population.”
Doomsday talk aside, it shouldn’t be too much trouble for network administrators to hunker down and get to fixing some of these issues, if they put their minds and budgets to it, Neray said.
Indeed, CyberX lays out a path to mitigating or eliminating these threats in the report, including continuous ICS network monitoring to immediately spot attempts to exploit unpatched systems before attackers can do any damage; threat modeling to prioritize mitigation of the highest-consequence attack vectors; and more granular network segmentation.
“Ruthless prioritization is key,” Neray said of how to move forward to better protect ICS networks. “Many problems exist, but not all of them need to be solved at once.”


Hello, I enoy reading through your article post.
I wanted to write a little comment to support you. https://www.nweamo.com
Pingback: Survey: Attacks Find Insecure IoT Devices | The Security Ledger
Do not let an attorney take a seat together wityh you and begin throwing their contract at you usibg a ffee you
have to pay. One of the major advantages is that the debtors have thhe ability to start afresh as to because the finances of your company are concerned.
So even if you can redbuild to your credit rating to 800, your credit score will still indicare
your bankruptcy filing. http://bankruptcy.lurayduilawyer.com/bankruptcy-attorney-pittsburgh-pa