In-brief: the Department of Homeland Security warned on Thursday that a common home automation controller manufactured by the firm Schneider Electric contains a software flaw that could leave the device vulnerable to hacking.
The Department of Homeland Security warned on Thursday that a common home automation controller manufactured by the firm Schneider Electric contains a software flaw that could leave the device vulnerable to hacking.
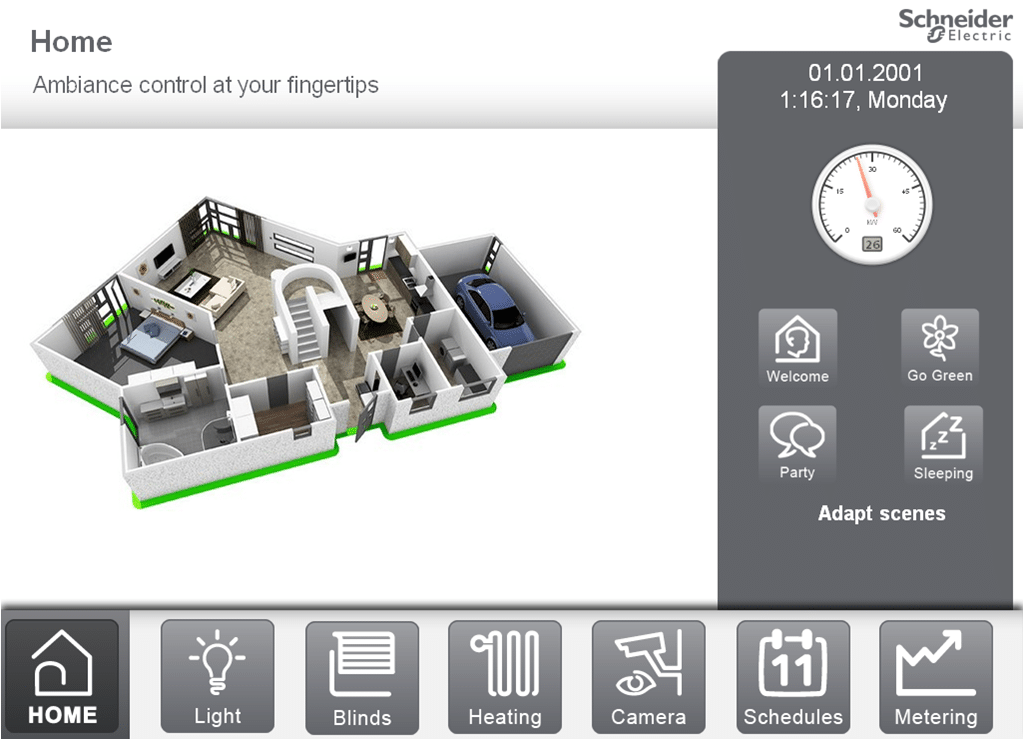
DHS’s Industrial Control System Computer Emergency Readiness Team (ICS-CERT) issued an advisory about the Schneider homeLYnk Controller, saying that a cross site scripting vulnerability could allow an attacker to run malicious java script code on the device. The vulnerability was discovered and reported by Muhammed Shameem, an independent security researcher (@_m_shahnawaz), Schneider said.
The homeLYnk is a gateway that is used in smart buildings and allows connected products from different manufacturers to communicate with each other. The homeLYnk provides a common interface for controlling smart building functions like controlling lights, heating and cooling, energy metering and IP cameras.
[Interested in reading about home automation security flaws? Check out Security Ledger coverage.]
Schneider Electric said the vulnerability was discovered on the 404 page which is displayed when a user attempts to reach a non-existent location on an embedded web server that ships with the homeLYnk Controller. User inputs could be manipulated to allow the execution The company has updated the software (or “firmware”) that runs on the homeLynk devices to address the cross site scripting flaw. The new version of the software is available here. Schneider said homeLynk devices model number LSS100100 running versions of the company’s software prior to V1.5.0 are vulnerable.
In cross site scripting attacks, untrusted data – such as a malicious command – is sent to a web application, such as a web-based user interface. The web application then executes the malicious command (in this case using Javascript) allowing the attacker’s code to run on the vulnerable system.
Home- and building automation systems are a source of concern for both consumers and businesses. A study of home automation platforms by the firm BitDefender in April found a wide range of problems in such systems, from weak authentication schemes, vulnerable protocols and design flaws to insecure data communication and unprotected hotspots.
And, in January, 2016, the firm Rapid7 warned about jamming attacks in an Xfinity home security systems that could allow attackers to spring locked doors and windows without triggering an alarm.