The news keeps coming out of South Korea, where a mysterious rash of hacks and virus infections early Thursday compromised tens of thousands of machines running at banks, broadcasters and other firms, erasing data and causing widespread disruption.
Here’s the latest:
South Korean Officials “Strongly Suspect” North Korea
South Korean government officials made their most direct statements to date (albeit anonymously) on the possible source of the attack, saying that they had a “strong suspicion” that the government of the Democratic People’s Republic of Korea (DPRK) was responsible.
Speaking to the YonHap News Agency, the official, identified as a “high ranking official in the office of President Cheong Wa Dae,” refused to elaborate. However, he may have been referring to the preliminary results of the Korea Communications Commission (KCC) which traced the malicious code responsible for crippling computers at broadcasters and banks to an IP address in China. South Korean officials said the North has used Chinese IP addresses in previous attacks on South Korean government and industry web sites. It’s worth noting that the DPRK is hardly the only state-sponsored or cyber criminal group that relies on vulnerable servers within China to launch attacks, so that’s hardly conclusive proof. But it may be proof enough for South Korea and its allies.
A Messy, Old School Attack
Analysis from a number of leading anti malware firms has emerged in the last 24 hours. Among the first was Alienvault, which disclosed that the malware worked by erasing the master boot record on infected systems, then forcing them to reboot. The MBR is used on hard disk drives and other large-capacity storage devices and contains information on how that device is logically partitioned. The data stored in the MBR is required in order for the device to boot properly.
Other firms to offer their analysis in the last 24 hours include: Avast, Trend Micro and Symantec. Some commonalities in the reports:
The malware overwrote the MBR with the terms HASTATI and PRINCIPES. Both terms would appear to refer to types of soldiers who served in the Roman Legion. Trend Micro points out that the attacks against the media companies weren’t isolated. Other attacks – less publicized – hit the website of a major electronics conglomerate was defaced. Several banks had their web sites compromised and used to plant backdoors on the systems of visitors. Trend doesn’t find any evidence, however, that were coordinated or connected in any way. “The timing may have been purely coincidental or opportunistic,” they conclude.
Symantec, in analyzing the malware – dubbed Trojan.Jokra – and wiper component, concurred with other malware experts that they were “nothing special.” The malware infects systems, kills off processes associated with AV products and then initiates the wipe of the MBR and any attached or networked drives.
Richard Henderson, a Security Strategist at Fortilabs, told The Security Ledger that two of three malware elements that were dropped were well known and associated with Gondad, a Chinese exploit kit used by cyber criminal groups. Some of the command and control servers also were connected to Gondad. Target systems were infected using simple e-mail messages with infected attachments, and there was no evidence that data theft was part of the plan.
“It was just a noisy, messy attack,” he said. “This was designed to make a lot of noise and get a lot of attention.”
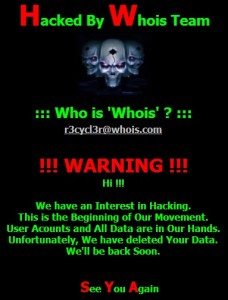
Who Is Whois?
Among the elements that don’t quite add up in all this is the web site defacements that accompanied many of the attacks on targets in South Korea. As Kaspersky Lab reported, the attackers replaced hacked web sites with an image of three skulls and the message “Hacked by Whois Team.” As Kaspersky noted in their post, the defacement message raises serious questions about the origin and purpose of the attack. “If a nation state is NOT behind these attacks, then it’s just cyber-terrorism; cyberwar requires a nation state to be behind the attacks. In general, if the attacks target critical infrastructure, they can be considered cyber-terrorism.”
The Takeaway?
International consensus right now appears to be that the DPRK must be behind the attacks, given recent history – a mystery outage in the North that was blamed on the U.S. and its allies, B-52 flights over South Korean airspace and so on.
That could still be the case. With hardly any economy to speak of, North Korea would have little use for stolen intellectual property, nor is it clear that they’d even know what to steal. They do, on the other hand, have a deep interest in making other nation’s fear their offensive cyber capability. A big, noisy, ham fisted like this may be just their style.
On the other hand, there is an equal or greater amount of evidence that points away from a nation-backed attack. The use of commercial components, the defacements, obscure references to the Roman Legion? It doesn’t all add up, and it’s certainly no slam dunk that the DPRK is behind it. That means that the parties involved should probably keep their powder dry and tone down the bellicose rhetoric until conclusive evidence and attribution are available.
