One of the ‘subplots’ of the Internet of Things revolution concerns embedded devices. Specifically: the tendency of embedded devices to be either loosely managed or – in some cases – unmanageable. The future holds the promise of more, not fewer of these. That’s the gist of a piece I wrote for InfoWorld, and that you can read here. In short: we’re already seeing the beginning of a shift on the threat landscape. While attacks against traditional endpoints (like Windows desktops, laptops and servers) are still the norm, there are more stories each day about cyber criminal groups and malicious actors who are compromising non-standard endpoints like home wifi routers. In March, for example, the security consultancy Team Cymru identified a botnet consisting of some 300,000 compromised home routers and other in-home devices. The virus called “TheMoon” was also identified spreading between vulnerable home routers and other embedded devices. The […]
Tag: Microsoft
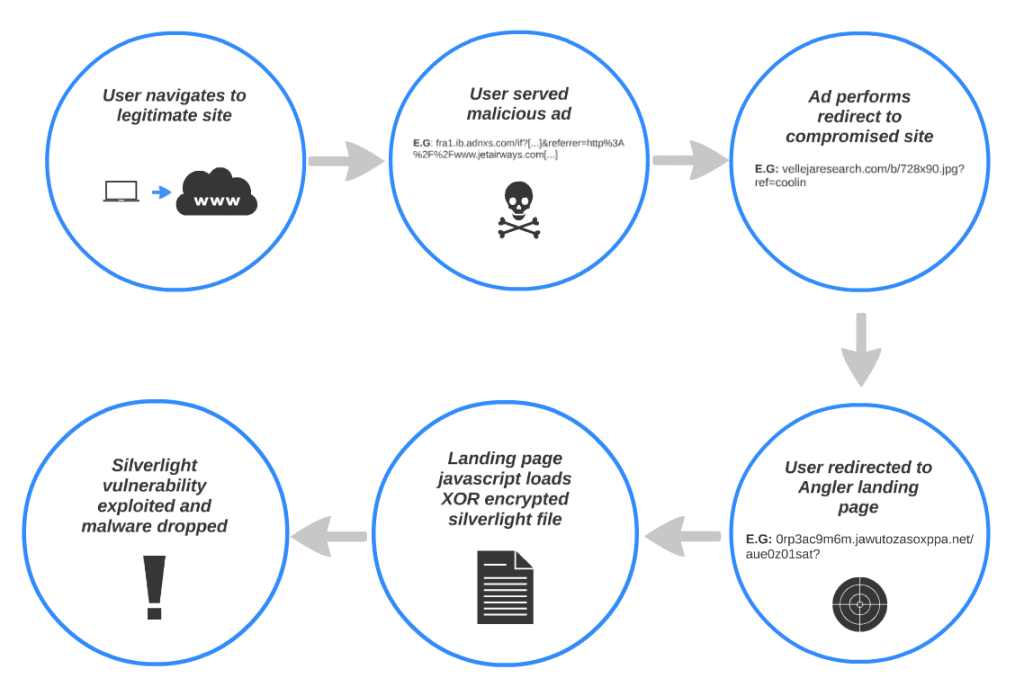
Cisco: Microsoft Silverlight Exploits Fueling Drive-By Attacks
Cisco Systems is warning that Silverlight exploits are being used in a rash of drive-by-download attacks, many tied to malicious advertising (or ‘malvertising’) campaigns. Writing on Cisco’s blog, Levi Gundert of Cisco’s Threat Research Analysis and Communications (TRAC) team said that Silverlight exploits are the “flavor of the month” and have been added to the popular Angler exploit kit since late April. “Since April 23rd we have observed substantial traffic (often from Malvertising) being driven to Angler instances partially using Silverlight exploits,” Gundert wrote. Attacks leveraging vulnerable instances of Silverlight are actually outstripping attacks against Java and Adobe Flash – the two platforms that have long been the preference of cyber criminal groups and exploit kit authors. Silverlight was the subject of a patch in March, MS04-014, to fix a vulnerability that could allow remote attackers to bypass a security feature. The vulnerability would allow an attacker who controls an attack website to launch specially […]
Heartbleed Prompts Fiscal Lifeline For Open Source
One of the most powerful (and substantive) realizations to come out of the news about the ‘Heartbleed’ OpenSSL vulnerability was that open source projects need help and attention from the tech community that relies on their fruits. I’ve written about this before – noting Apple’s reluctance to put some of its considerable cash hoard towards supporting open source projects it relies on (like the Apache Software Foundation), as have others. [Read Security Ledger’s coverage of the Heartbleed vulnerability here.] Now that idea appears to have taken root. On Thursday, the Linux Foundation announced the creation of the Core Infrastructure Initiative, a multi-million dollar project to fund open source projects that are in the critical path for core computing functions. The CII group has some substantial backing. Google, Cisco, Microsoft, Facebook, Amazon, IBM, Intel, Samsung, Fujitsu and VMWare all signed on to the CII Steering Committee. (Surprising (or not): Apple was not one of the firms supporting […]
History Suggests Heartbleed Will Continue To Beat
The SANS Internet Storm Center dialed down the panic on Monday, resetting the Infocon to “Green” and citing the increased awareness of the critical OpenSSL vulnerability known as Heartbleed as the reason. Still, the drumbeat of news about a serious vulnerability in the OpenSSL encryption software continued this week. Among the large-font headlines: tens of millions of Android mobile devices running version 4.1 of that mobile operating system (or “Jelly Bean”) use a vulnerable version of the OpenSSL software. Also: more infrastructure and web application players announced patches to address the Heartbleed vulnerability. They include virtualization software vendor VMWare, as well as cloud-based file sharing service Box. If history is any guide: at some point in the next week or two, the drumbeat will soften and, eventually, go silent or nearly so. But that hardly means the Heartbleed problem has gone away. In fact, if Heartbleed follows the same […]
Facebook Joins In Tech Industry Demands For Surveillance Reform
Facebook on Tuesday reiterated calls for reform of laws pertaining to government surveillance practices in the U.S. and elsewhere. The company, in a blog post, urged governments to stop bulk collection of data and enact reforms to limit governments’ authority to collect users information to pertain to “individual users” for “lawful purposes.” The company also called for more oversight of national intelligence agencies such as the US National Security Agency, and more transparency about government requests for data. The blog post was authored by Facebook general counsel Colin Stretch. Facebook reiterated its calls for surveillance reform in recognition of “The Day We Fight Back,” a grass roots effort to use Tuesday, February 11th as a day to rally support for more civil liberties protections. [Read more Security Ledger coverage of Facebook here.] The date is the one year anniversary of the suicide of Internet activist Aaron Swartz. Leading online […]