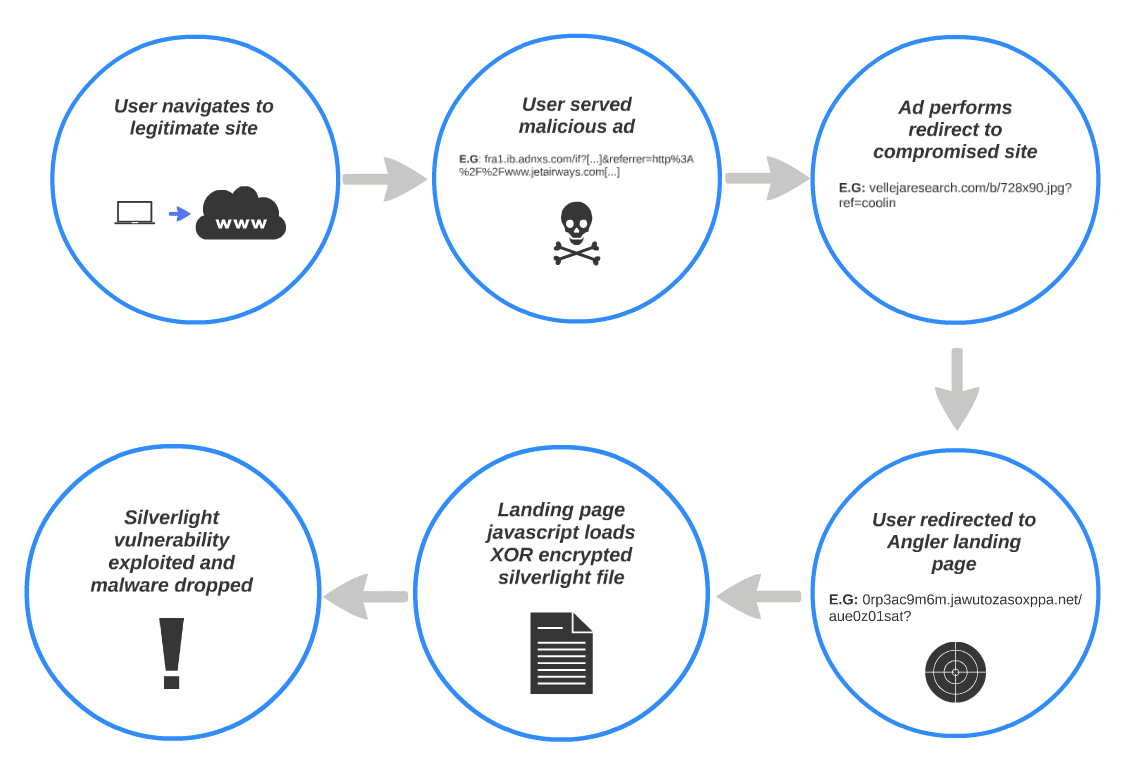
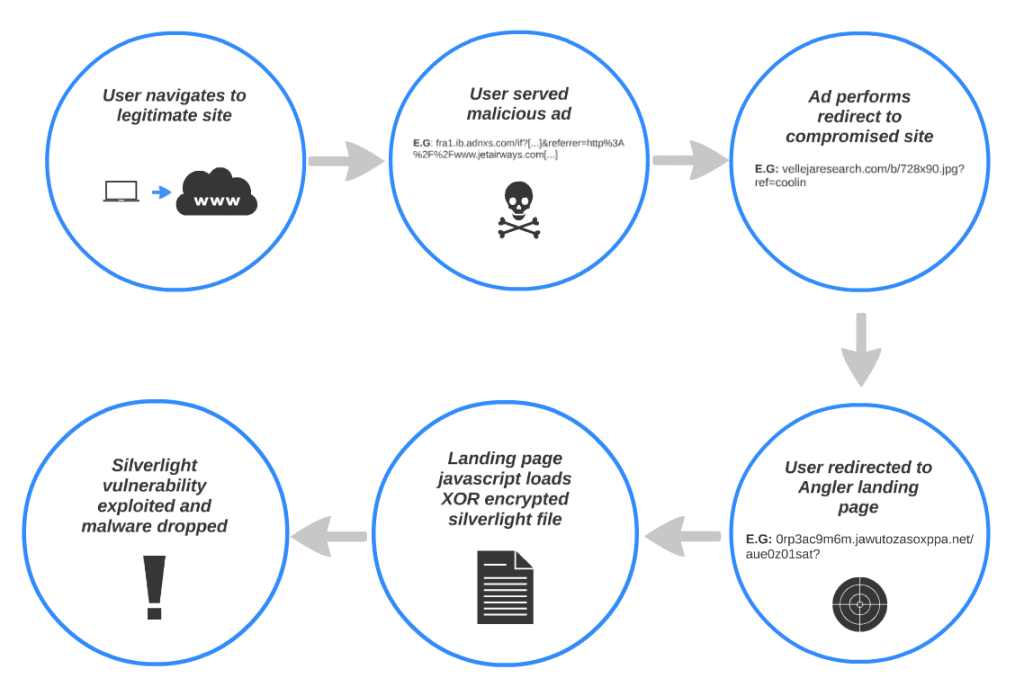
Cisco Systems is warning that Silverlight exploits are being used in a rash of drive-by-download attacks, many tied to malicious advertising (or ‘malvertising’) campaigns.
Writing on Cisco’s blog, Levi Gundert of Cisco’s Threat Research Analysis and Communications (TRAC) team said that Silverlight exploits are the “flavor of the month” and have been added to the popular Angler exploit kit since late April. “Since April 23rd we have observed substantial traffic (often from Malvertising) being driven to Angler instances partially using Silverlight exploits,” Gundert wrote.
Attacks leveraging vulnerable instances of Silverlight are actually outstripping attacks against Java and Adobe Flash – the two platforms that have long been the preference of cyber criminal groups and exploit kit authors.
Silverlight was the subject of a patch in March, MS04-014, to fix a vulnerability that could allow remote attackers to bypass a security feature. The vulnerability would allow an attacker who controls an attack website to launch specially constructed Silverlight content that would exploit the vulnerability. All versions of Microsoft Silverlight prior to build 5.1.30214.0 are affected.
The latest attacks use malicious advertisements to trick victims into visiting the malicious site serving Silverlight based attacks. Cisco said the attack consists of multiple stage web redirection that lead to the site running the Angler Exploit Pack. The attacks are delivered using either Adobe Flash or Silverlight. Successfully exploited systems have the malicious payload installed: a Trojan Horse program that opens two listener ports and initiates a TCP connection to a remote host located in Brazil, Cisco said.