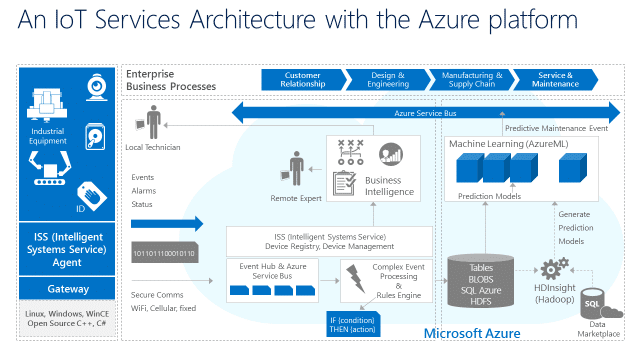
In-brief: Microsoft Corp. made a major play for the Internet of Things platform space, announcing Azure IoT Suite – a cloud based platform for accelerating and managing Internet of Things products.
Tag: Microsoft
Market Consolidation for The Internet of Things Has Begun | Forbes
In-brief: It’s early days, but consolidation among Internet of Things players has already begun, with tech giants cementing their position.
At Summit, in search of Leadership on Cyber Security
In-brief: President Obama will address technology leaders at a Summit at Stanford University on Friday. But technology industry leaders say that much hinges on Washington’s ability to pass needed legal reforms.
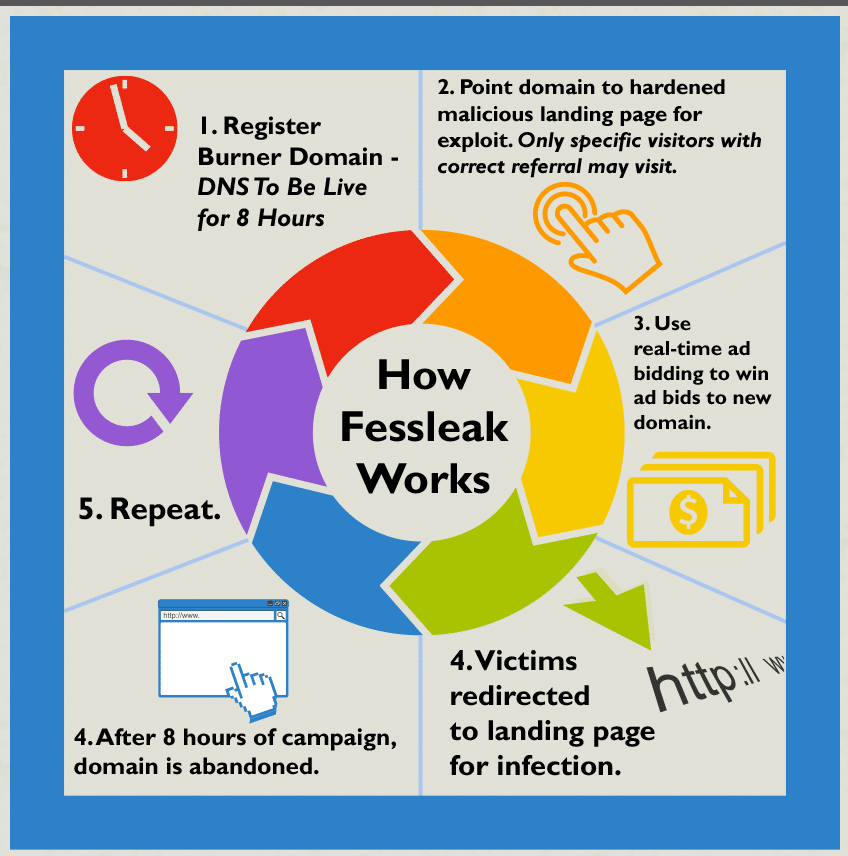
New Ransomware, FessLeak, Taps Adobe Flash Flaws
In-brief: A new and sophisticated ransomware family dubbed “Fessleak” is spreading in malicious advertising (or “malvertising”) campaigns by exploiting newly disclosed flaws in Adobe’s Flash technology.
Microsoft Plays for IoT with Windows 10 for Raspberry Pi
In-brief: Microsoft is making good on promises that its next version of Windows will be a player on the Internet of Things, announcing support for Raspberry Pi 2.