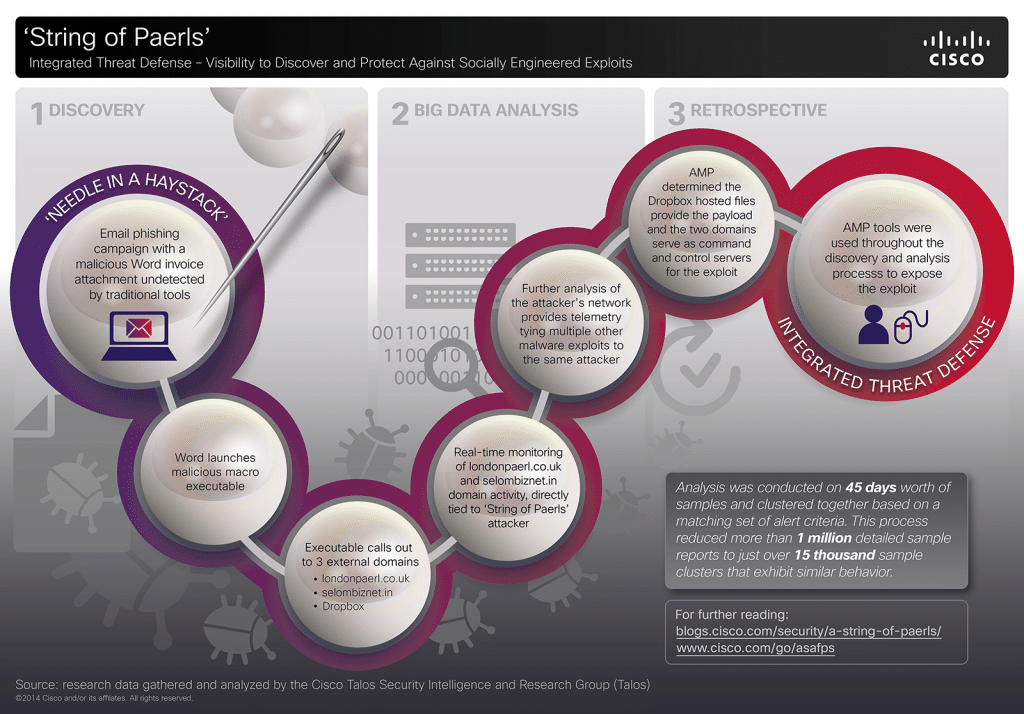
In the last year, the world’s attention has been riveted by a series of high-profile hacks of major corporations in retail, finance and the entertainment industry, among others. Each of these incidents is unique, involving different threat actors and motives. However, each of these attacks is also a sterling example of what we, at Cisco, term “multi-vector attack” that employs a range of technologies, deployed in numerous stages, to penetrate the defenses of the target organization. Here at Cisco, we have studied these attacks in-depth and have identified some commonalities among these multi-vector attack, and useful approaches to combat them. This blog post will discuss some of our findings. About Multi-Vector Attacks Any cyber attack, large or small is born from a weak link in the security chain. These weak links take many forms: poorly configured Web servers, gullible employees or vulnerable-but-common applications like Microsoft Office, Adobe Reader and Java are common examples. Multi-vector attacks […]
social engineering
Report: Cyber Ring Stole Data To Game Stock Market | Reuters
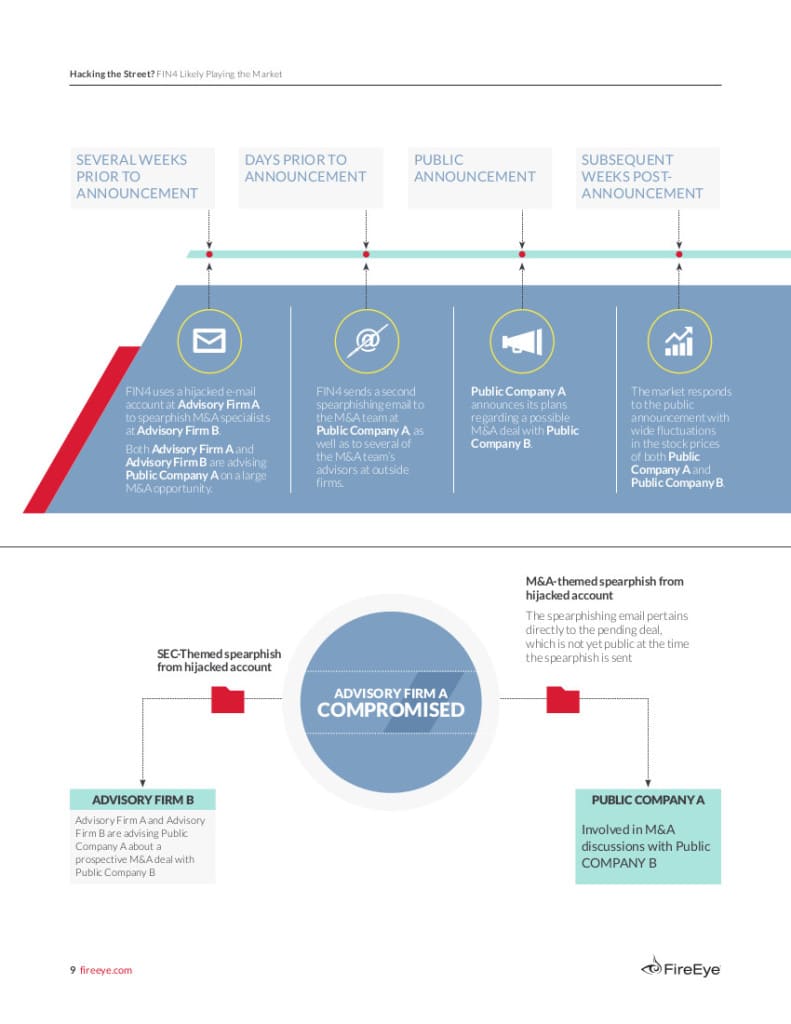
Reuters has the story this morning about a new report out from the folks at FireEye about a cyber espionage ring that targets financial services firms. The campaign, dubbed FIN4 by FireEye, stole corporate secrets for the purpose of gaming the stock market. FireEye believes that the extensive cyber operation compromised sensitive data about dozens of publicly held companies. According to FireEye the victims include financial services firms and those in related sectors, including investment bankers, attorneys and investor relations firms. Rather than attempting to break into networks overtly, the attackers targeted employees within each organization. Phishing e-mail messages led victims to bogus web sites controlled by the hackers, who harvested login credentials to e-mail and social media accounts. Those accounts were then used to expand the hackers reach within the target organization: sending phishing email messages to other employees. The criminals behind FIN4 sought data that could be useful to stock traders, including Securities and […]
White House Cyber Chief: JP Morgan Underscores Critical Infrastructure Risk
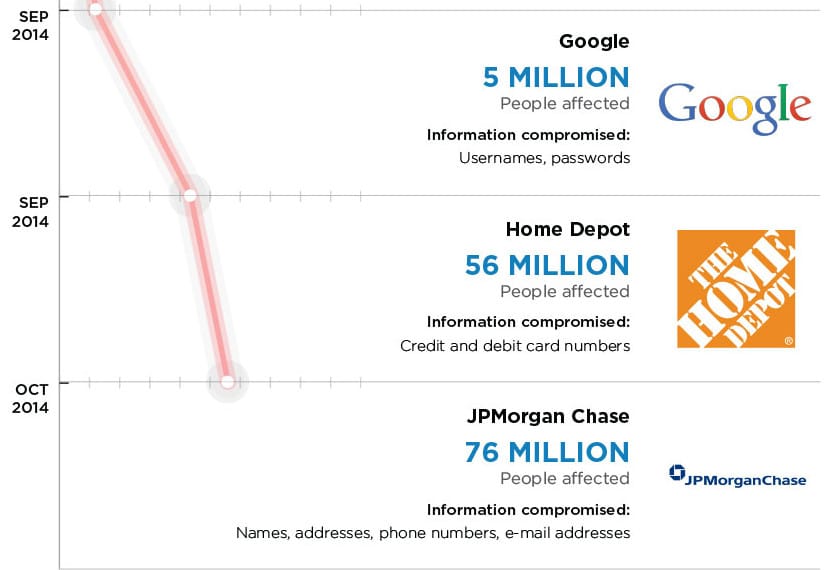
The White House’s cyber security czar, Michael Daniel, said the Obama Administration is deeply concerned about the reported hack of systems belonging to banking giant JP Morgan Chase & Co. but sees the incident as part of a larger trend of attacks against U.S. critical infrastructure. Asked about the targeted attack against JP Morgan and other banks and financial institutions, Daniel said that the White House was concerned, but not surprised by the incident. “We have watched for several years the trend of malicious actors in cyber try to figure out how to target critical infrastructure,” he said. “Financial services is critical infrastructure.” The White House was concerned that a major U.S. bank would fall victim to hackers, but sees it in the context of a “broad trend,” rather than an isolated incident, he said. Speaking with Michael Farrell, the Cybersecurity Editor at Christian Science Monitor, Daniel hit on many of the now-common talking […]
Europol Warns of Internet of Things Risk
In a newly released report, Europol’s European Cybercrime Center (EC3) warns that the growth of the Internet of Things (IoT) threatens to strengthen the hand of organized cyber criminal groups and make life much more difficult for police and governments that wish to pursue them. EC3’s latest Internet Organized Crime Threat Assessment (iOCTA) says the “Internet of Everything” will greatly complicate the work of law enforcement creating “new opportunities for everything from cyber criminals to state actors to child abusers. The growing numbers of connected devices will greatly expand the “attack surface” available for cyber criminal activity, the EC3 warns. Cyber criminals may co-opt connected devices for use in common criminal activity (like denial of service attacks and spam campaigns). However, advancements like connected (“smart”) vehicles and infrastructure create openings for large scale and disruptive attacks. The report, which was published late last months, is a high level position paper and pulls data mostly […]
Chief Security Officer: The Toughest Job In IT?
Register now for our CISO Hangout with Jon Trull of Qualys, the former Chief Security Officer for the State of Colorado. Chief Information Security Officers (CISOs) are in the news a lot these days. The breaches at prominent corporations like Target, Home Depot and (this week) JP Morgan have solidified the consensus that the CISO is a necessary complement to the CIO. They’ve also shone a spotlight on what many consider to be the toughest job in corporate America. After all, successful cyber attacks and data breaches are the quickest path to a ruined corporate reputation. And a strong and capable CISO is increasingly seen as the best defense against such an unfortunate occurrence. (Target’s misfortune was the direct result, some argued, on its lack of a CISO.) With all that in the air, the time couldn’t be better to sit down with some of the top CISOs in industry and the public […]