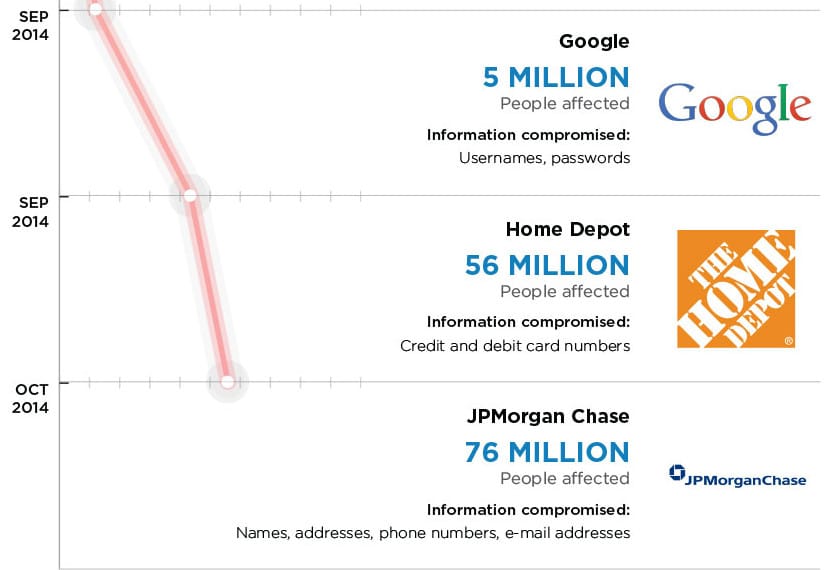
The White House’s cyber security czar, Michael Daniel, said the Obama Administration is deeply concerned about the reported hack of systems belonging to banking giant JP Morgan Chase & Co. but sees the incident as part of a larger trend of attacks against U.S. critical infrastructure. Asked about the targeted attack against JP Morgan and other banks and financial institutions, Daniel said that the White House was concerned, but not surprised by the incident. “We have watched for several years the trend of malicious actors in cyber try to figure out how to target critical infrastructure,” he said. “Financial services is critical infrastructure.” The White House was concerned that a major U.S. bank would fall victim to hackers, but sees it in the context of a “broad trend,” rather than an isolated incident, he said. Speaking with Michael Farrell, the Cybersecurity Editor at Christian Science Monitor, Daniel hit on many of the now-common talking […]
Infograph
McKinsey: Consumers Want Connected Cars – And Fear Them, Too
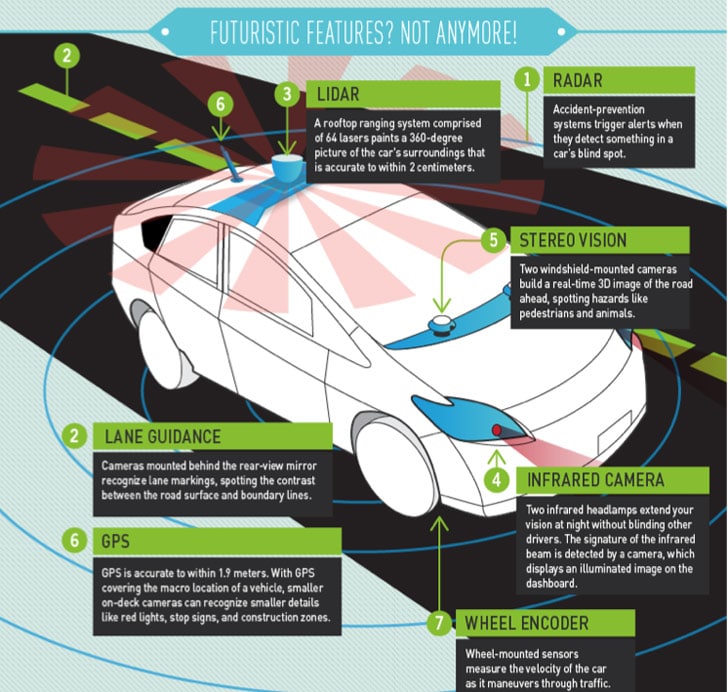
The consulting firm McKinsey & Co. has released an interesting report on the future of connected vehicles. But it has some sobering data for car makers: concerns about privacy and the possibility that connected cars could be hacked are major concerns for consumers that could dampen enthusiasm for smart vehicles. The report, “What’s Driving the Connected Car?” finds that connectivity features will be a major driver of car sales in the coming years, with car buyers increasingly accustomed to vehicles that sport sophisticated interactive and networking features. That said: security concerns may hamper the “rapid and broad adoption” of connected vehicle technology. For its report, McKinsey interviewed 2,000 new car buyers in four countries: Brazil, China, Germany and the U.S. The survey found that a quarter of respondents considered connectivity a more important feature than engine power or even fuel efficiency. The firm estimates that connectivity features will become increasingly important selling features […]
FDA Issues Guidance on Security of Medical Devices
The U.S. Food and Drug Administration (FDA) issued final guidance on Wednesday that are designed to strengthen the safety of medical devices. The FDA called on medical device manufacturers to consider cyber security risks as part of the design and development of devices. The document, “Content of Premarket Submissions for Management of Cybersecurity in Medical Devices,” asks device makers to submit documentation to the FDA about any “risks identified and controls in place to mitigate those risks” in medical devices. The guidance also recommends that manufacturers submit documentation of plans for patching and updating the operating systems and medical software that devices run. The document, which will be released on Thursday, does not contain specific requirements. Rather, it describes the kinds of things that medical device manufacturers should consider when preparing pre-market submissions for medical devices in areas such as information confidentiality, integrity, and availability, the FDA said. The release of the document follows the […]
Infographic: Possible Attacks on The Internet of Things
The folks over at Trend Micro have put together a nice infographic that reminds us that all those smart devices connected to the Internet communicate through some well worn channels, namely: standard communications protocols like Wi-Fi, Ethernet and Bluetooth that connect devices to each other and the global Internet, as well as HTTP that are used to transmit data to and from cloud based resources like management interfaces. Of course those standard protocols also leave IoT devices vulnerable to a wide range of commodity attacks: from brute force password cracking on web based management consoles to Man in the Middle attacks that can sniff out authentication credentials and hijack sessions. Trend’s infographic does a good job of depicting the various layers in the IoT stack and some of the likely attack vectors for each layer. It also gives advice on how to protect yourself (use encryption, patch software vulnerabilities, disable unused ports). Nothing ground breaking […]