Recently, the Akamai Threat Research Team unveiled a unique distributed brute force attack campaign targeting nearly five hundred WordPress applications. What’s interesting about this campaign? It clearly demonstrates how Web attackers are becoming more sophisticated, attempting to evade security controls – specifically Web Application Firewalls (WAFs) and rate control protections. A Short Primer to Brute-Force Attacks Brute force Web attackers attempt to gain privileged access to a Web application by sending a very large set of login attempts, within a short period of time. Using volumetric single source of attack is easily mitigated by blacklisting. Today’s brute force attacks are typically characterized by volumetric attacks coming from distributed IPs. In this way, if the attacker’s source IP is detected, they can still continue with the attack campaign by switching a source IP. As part of this cat-and-mouse evolution, WAFs are enhanced with several rate control measures that detect and block […]
Infograph
With Multi-Vector Attacks, Quality Threat Intelligence Matters
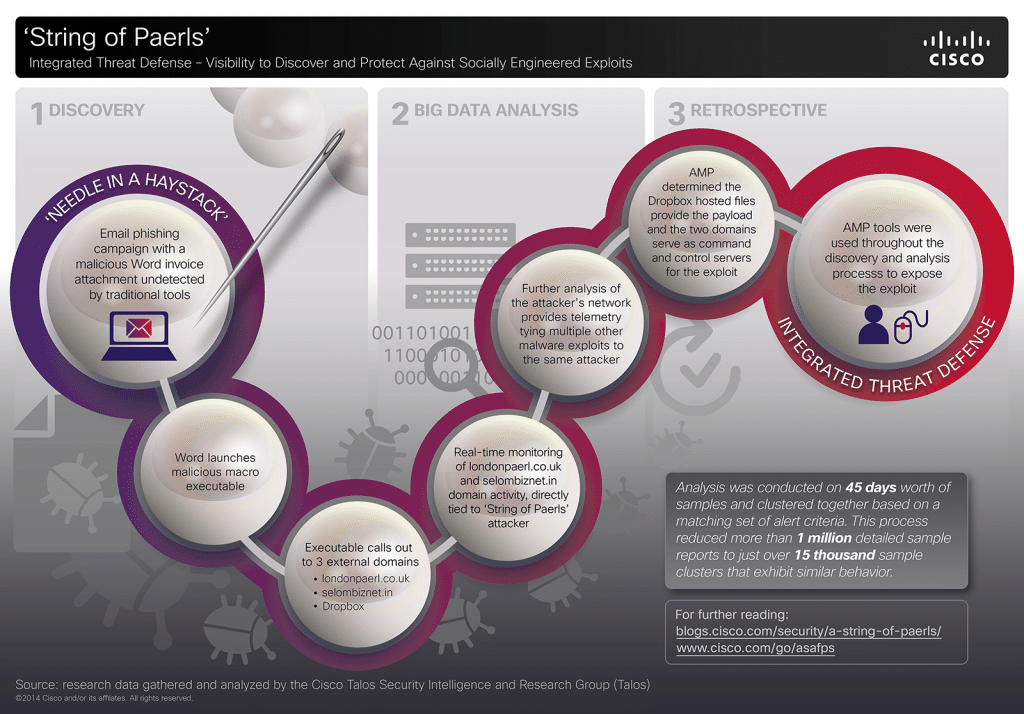
In the last year, the world’s attention has been riveted by a series of high-profile hacks of major corporations in retail, finance and the entertainment industry, among others. Each of these incidents is unique, involving different threat actors and motives. However, each of these attacks is also a sterling example of what we, at Cisco, term “multi-vector attack” that employs a range of technologies, deployed in numerous stages, to penetrate the defenses of the target organization. Here at Cisco, we have studied these attacks in-depth and have identified some commonalities among these multi-vector attack, and useful approaches to combat them. This blog post will discuss some of our findings. About Multi-Vector Attacks Any cyber attack, large or small is born from a weak link in the security chain. These weak links take many forms: poorly configured Web servers, gullible employees or vulnerable-but-common applications like Microsoft Office, Adobe Reader and Java are common examples. Multi-vector attacks […]
Intel’s New IoT Platform Emphasizes Security
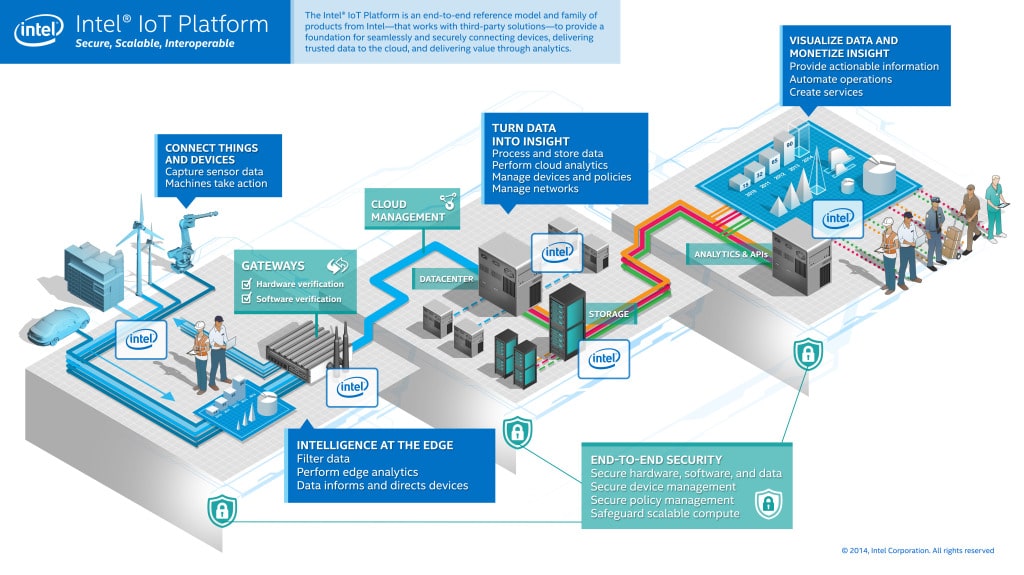
Intel unveiled a new Internet of Things platform this week dubbed (surprisingly enough) the “Intel IoT Platform.” The goal is to provide a unified platform for connecting diverse and distributed connected things. Given Intel’s big investment in security with the purchase of McAfee, its no surprise that security is a big part of the “value add” for the IoT platform. Intel says that its IoT platform promotes interoperability of network, operational technology and information technologies. The IoT Platform envisions Intel Quark™ to Intel Xeon, and Intel-based devices, gateways, and datacenter solutions with hardware-based root of trust. With hardware enabled identity and secure boot features, Intel believes that you can eliminate a wide range of malicious attacks and compromises. Intel’s IoT Gateway devices are based on its 2009 acquisition of WindRiver. They also wrap security intelligence from Intel’s acquisition of McAfee. Specifically, Intel has embedded anomaly and intrusion detection and prevention capabilities in […]
Infographic: After A Year of Breaches, Are Retailers More Secure?
After a year in which some of the U.S.’s top retailers found themselves on the wrong side of sophisticated, cyber criminal hacking groups, you may be tempted to search for a silver lining. Maybe the up side of all the attacks on retail networks and point of sale systems is an improved security posture overall? After all: if your neighbors to the left and right have their house broken into, you may well beef up your locks and alarms, even if your house hasn’t been targeted. Or, at least, that’s how the thinking goes. But Boston-based BitSight took a look at how the retail sector is faring security-wise as 2014 draws to a close. BitSight is an interesting company. They market a kind of reputation monitoring service: assessing security posture for companies by observing how they look from the outside. Think of it as a kind of Experian or TransUnion for security. […]
Convergence of M2M and IoT signals Major Cultural Shift
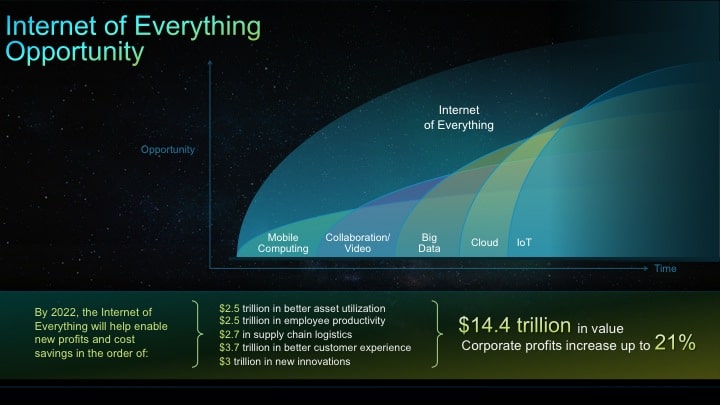
Required reading for Monday: TechCrunch has a nice little explainer article by @ArtyomAstafurov (of DeviceHive) that talks about the evolution of machine-to-machine (M2M) technologies into the Internet of Things and how the two technology trends are now indistinguishable- and are poised to cause large-scale disruption. To quote Astafurov: “IoT separates itself from M2M not only in the simplicity and quantity of devices involved, but also by how the devices communicate with each other…Whereas M2M tends to rely on point-to-point exchanges between individual devices, IoT communications involve dispersed devices sharing data through a central server, resulting in exponentially more data based on the relationships and patterns that emerge.” And the IoT will drive massive investment in products and technologies that can capture, aggregate and analyze consumer data. This will be akin to the kind of investment corporations put into ERP (enterprise resource planning) tools a decade ago, he says. Though the focus of IoT right […]