In-brief: Nine of every ten data breaches that occurred in the first eight months of 2015 were “easily avoidable,” according to a study released by the Online Trust Association (OTA) on Tuesday.
Auto OEM Harman Buys Security firm TowerSec
In-brief: HARMAN, the automobile supplier, said it will buy Tower Security, a maker of security technology for connected vehicles.
Podcast: Interview with Car Hacker Chris Valasek of IOActive
In-brief: Security Ledger Editor in Chief Paul Roberts speaks with Chris Valasek, the Director of Vehicle Research at IOActive about the work he and Charlie Miller did to develop wireless based attacks that control the braking, steering and acceleration of late model Chrysler vehicles.
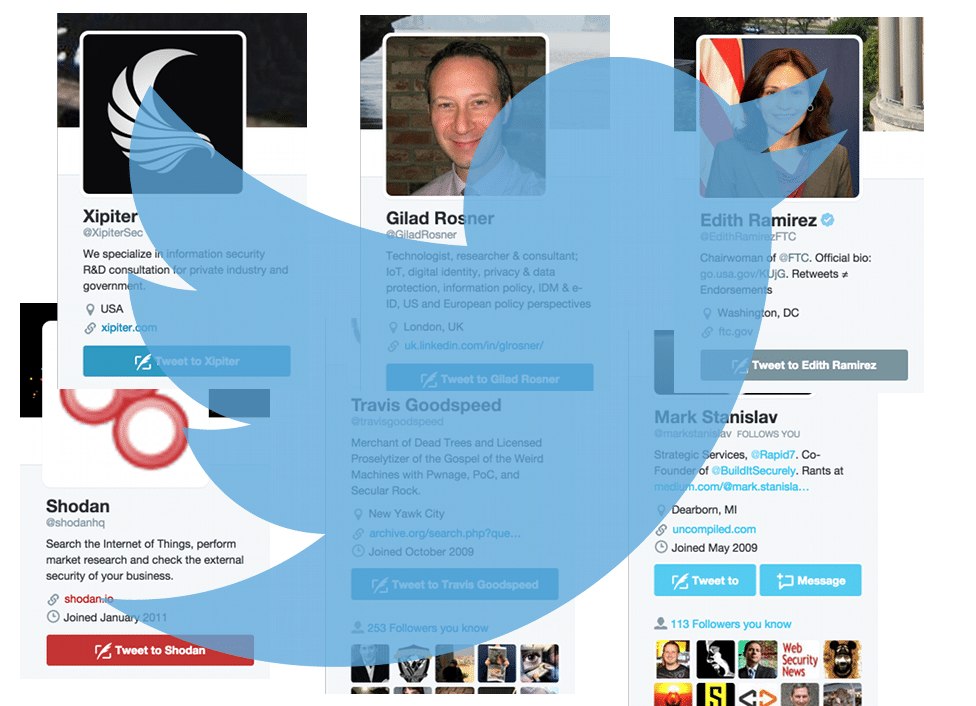
Twitter Accounts to follow for IoT and Security
Twitter is a great place to keep tabs on what leading security researchers, academics, policy makers and luminaries are up to. That’s no different for security and Internet of Things, where scores – even hundreds – of world-class researchers and thought leaders share their latest work, exchange ideas, opine and post pictures of their cats. Here are a few of the most rewarding security and Internet of Things accounts that we follow here at The Security Ledger. [soliloquy id=”56140″]
Customer Support A Weak Link In Two Factor | Ars Technica
Ars Technica has an interesting write-up on an apparently successful compromise of Google’s two-factor authentication technology. Though in this case, the culprit wasn’t any system Google deployed or managed, but a gullible customer support representative working for the victim’s cell phone carrier. According to this post over at Facebook-for-hipsters site Ello.co, Grant Blakeman woke up on a recent Saturday morning to find that his Google account had been hijacked – despite the fact that he used Google’s two-factor authentication to protect access to the account. How? Blakeman enlisted the help of none-other than Mat Honan, whose own struggles with account hijacking became the subject of a much-cited Wired feature article. As with Honan, Blakeman’s valuable three-character Instagram account, @gb, appears to have been the lure for hackers. (Honan’s @mat Twitter account was what lured his attackers.) Read “Researchers sidestep Paypal Two-Factor Authentication.” After a conversation with Honan, Blakeman contacted his cell provider and […]