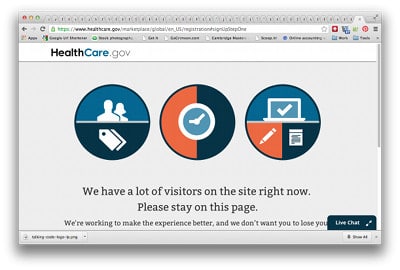
In a blog post on Veracode’s blog today, I write about the problems encountered at government-run online health exchanges that were intended to connect millions to private insurance plans under the Affordable Care Act. The exchanges opened to the public on Tuesday, and they got off to a rocky start, with reports of web sites paralyzed as millions of uninsured Americans logged on to sign up for subsidized health insurance. In some cases, the problems appear to have been caused by “external factors.” New York State’s online health exchange was felled by the weight of more than 10 million requests of dubious origin, The New York Post reported. But other exchanges, including Healthcare.gov the federal government’s main health insurance storefront, which is used by residents or more than half of the states, were victims of their own success: overwhelmed when the doors swung open and millions of eager customers poured […]
Experts Crowd Source Bounty To Defeat iPhone 5S TouchID
A group of security enthusiasts, including some leading figures in the IT security industry, have pledged their hard-earned cash toward a bounty for the first hacker who can fool Apple’s new iPhone 5s Touch ID fingerprint scanner using a fingerprint lifted without the owner’s consent. A web site, istouchidhackedyet.com, has been set up to coordinate the campaign, with more than $14,000 in pledges committed (via Twitter posts) from a Who’s Who of the IT security community. The project was the brainchild of Robert David Graham of Errata Security (@ErrataRob) and Nick De Petrillo (@nickdepetrillo) of Crucial Security, who launched the contest and set up the web site to collect donations. Security luminaries from across the globe chipped in funds to build a bounty, including Travis Goodspeed ($50) and Nick Percoco (@c7five) of the security firm Trustwave ($250). The largest single donation – $10,000 – came by way of Arturas Rosenbacher (@arturas) […]
Security Of “Things” Increasingly The Stuff Of Headlines
It looks as if the mainstream media is waking to the security implications of the “Internet of Things,” in the wake of recent demonstrations at the Black Hat and DEFCON conferences that highlight vulnerabilities in everything from home automation systems to automobiles to toilets. Stories in The New York Times and other major news outlets in the last week have highlighted concerns about “the cyber crime of things” as Christopher Mims, writing in The Atlantic, called it. Insecure, Internet connected devices ranging from surveillance cameras to home heating and cooling systems could leave consumers vulnerable to remote attacks and spying. The stories come after hacks to non-traditional computing platforms stole most of the headlines from this year’s Black Hat and DEFCON shows in Las Vegas. A compromise of a Toyota Prius hybrid by researchers Charlie Miller of Twitter and Chris Valasek of IOActive was featured prominently in stories by Forbes and […]
Update: DARPA Cyber Chief Peiter “Mudge” Zatko Heads To Google
Editor’s Note: Updated with comment from Google on Zatko’s role. – PFR Noted hacker and innovator Peiter “Mudge” Zatko, a project manager for cyber security research at DARPA for the past three years- will be setting up shop in the Googleplex, according to a post on his Twitter feed. Zatko, who earned fame as a founding member of the early 1990s Boston-area hacker confab The L0pht and later as a division scientist at government contractor BBN Technologies, announced his departure from DARPA following a three-year stint as a Program Manager in DARPA’s Information Innovation Office on Friday. “Given what we all pulled off within the USG, let’s see if it can be done even better from outside. Goodbye DARPA, hello Google!” he Tweeted. Google did not immediately respond to a request for comment on Zatko’s hiring and Zatko declined to expound on his title and responsibilities within the search giant. However, he has acknowledged that […]
Many Watering Holes, Targets In Hacks That Netted Facebook, Twitter and Apple
The attacks that compromised computer systems at Facebook, Twitter, Apple Corp. and Microsoft were part of a wide-ranging operation that relied on many “watering hole” web sites that attracted employees from prominent firms across the U.S., The Security Ledger has learned. The assailants responsible for the cyber attacks used at least two mobile application development sites as watering holes in addition to the one web site that has been disclosed: iPhoneDevSDK.com. Still other watering hole web sites used in the attack weren’t specific to mobile application developers – or even to software development. Still, they served almost identical attacks to employees of a wide range of target firms, across industries, including prominent auto manufacturers, U.S. government agencies and even a leading candy maker, according to sources with knowledge of the operation. More than a month after the attacks came to light, many details remain under tight wraps. Contacted by The Security […]