Podcast: Play in new window | Download (Duration: 33:43 — 30.9MB) | Embed
In this episode of The Security Ledger Podcast (#259) Paul speaks with Ross McKerchar, the CISO of Sophos, about the the company’s recent, headline grabbing report on a six year, state sponsored hacking campaign it dubbed Pacific Rim. Ross talks about the company’s dawning awareness of the extent and sophistication of the operation and its use of a targeted software implant to monitor the workings of the state-sponsored group and stay a step ahead of the hackers efforts to breach Sophos and its customers.
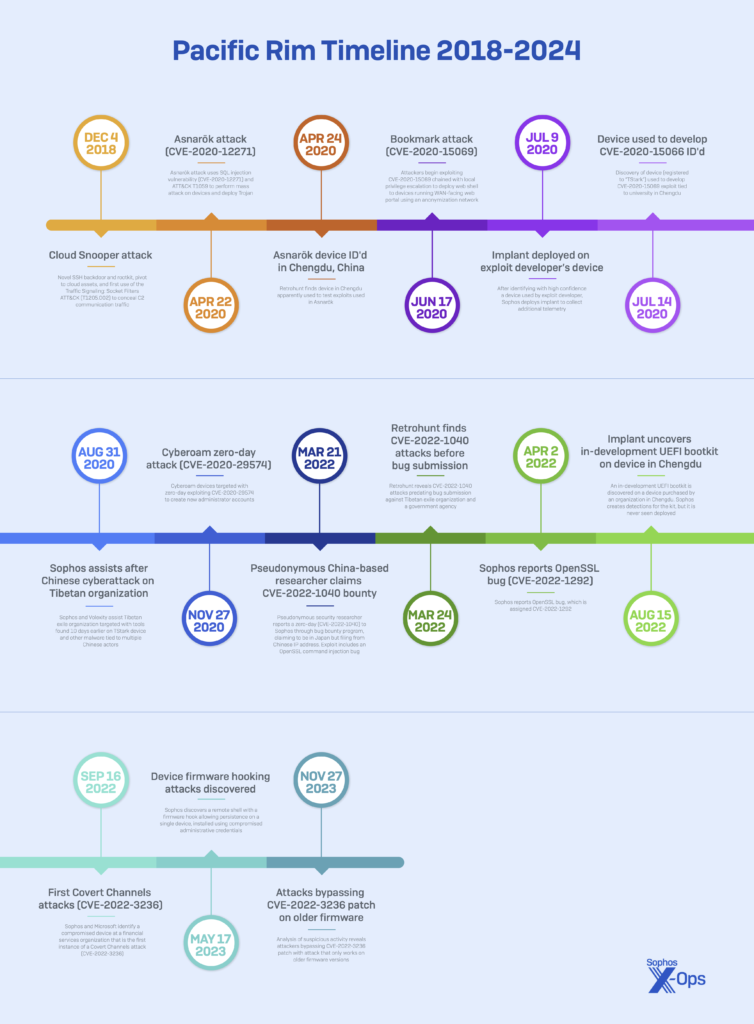
After so many decades writing about hair raising cyber attacks, it is easy to get jaded -and hard to be impressed. And then something like the Pacific Rim report comes along. Released last month by the UK-based cybersecurity firm Sophos, Pacific Rim is an eye-raising account of a years-long battle with persistent and sophisticated hackers based in China who were determined to compromise Sophos and use their access to target the company’s customers.

A six year stealth campaign
The Sophos Pacific Rim report paints a detailed picture of a relentless nation-state level cyber assault that was years in the making. The attack, emanating from a well-resourced group of PRC-based actors, wasn’t a conventional one-off breach but rather a protracted, six-year campaign involving a wide range of entities and software assets across regions, beginning in India with the compromise of a wall-mounted display at Cyberoam, a company Sophos had acquired. From there, the attackers used “live off the land” techniques to infiltrate other systems, exploiting vulnerabilities to gain unauthorized access to sensitive areas, all the while showcasing advanced techniques that far exceeded the kind of low-skill script kiddie or hacker tactics, and elevated concerns about the breadth of their capabilities.
ORBs and AWS: China’s sophisticated hacking techniques
In this podcast, I sat down with Ross McKerchar to dig into the Pacific Rim incident. Ross and I talk about his company’s quick realization that what appeared to be a run-of-the-mill intrusion onto Cyberoam’s network was much more: one branch of a global campaign by Chinese-backed hacking groups to gain access to a wide range of sensitive targets, from tech firms to critical infrastructure providers to government agencies and embassies.
Ross and I discuss the evolution of attack methodologies by China-based threat groups, as well as the many characteristics that made the Pacific Rim stand out, such as the attackers’ utilization of cutting edge cloud-based management tools like AWS SSM to elevate their intrusion capabilities and “ORBs” (operational relay boxes) -a kind of purpose built botnet of compromised devices that hacking groups use as a foundation for further attacks.
The report exposes intriguing insights into China’s cyber capabilities, with attackers using sophisticated methods – including the deployment of exploits for “zero day” software vulnerabilities to further economic and geopolitical goals: from corporate espionage and intellectual property theft to surveillance of perceived rivals and cyber-physical disruptions of critical infrastructure.
The wisdom of defending forward
Ross and I also talk about Sophos’ move to “defend forward” and deploy a “targeted implant” – software on compromised IT assets that allowed Sophos to monitor the comings and goings of the Chinese hackers. Among other things, Sophos’ use of the targeted implant allowed the company to intercept an exploit for a 0day vulnerability that the Chinese hackers were preparing to use and patch the underlying software flaw before the large-scale deployment, highlighting their success in navigating this sophisticated cyber battlefield.
We also discuss the growing challenges of ensuring endpoint security in the face of growing “end of life” and legacy systems, an intricate web of local and cloud-based attack surfaces, and the constant rise in exploitation capabilities. Ross shares his insights into the broader strategic implications of Pacific Rim: underscoring the necessity for resilience and advanced detection frameworks in today’s cyber landscape.
He advocates for enhanced cybersecurity protocols, urging companies to not only strengthen defenses but also incorporate forward-thinking detection and response measures to stay ahead of threats.
Use the podcast player above to listen to an audio of our talk, or check us out on your favorite podcast app. Or check out the video version of our conversation below!
Video Podcast & Transcript
Video Podcast
You can watch a video of my interview with Ross below. Also: check out more Security Ledger podcast interviews on our YouTube channel!
Transcript
[00:00:00]
Paul Roberts (Security Ledger): Hey, welcome back everyone to another episode of the Security Ledger Podcast I’m Paul Roberts, and I am the host and editor in chief here at the security ledger. And we are thrilled to have with us Ross McKerchar, who is at CISO, Chief. Information Security Officer at Sophos to talk about a really pretty astounding report.
Paul Roberts (Security Ledger): Sophos put out late last month in October on a sustained APT attack, nation state attack on their organization and others as well, dubbed Pacific Rim and Ross, welcome.
Ross McKerchar, CISO Sophos: Yeah, great to be here. Thanks, Paul.
Paul Roberts (Security Ledger): It’s great to have you. I think it’s the first time and honored to have you on. Before we get going just for our listeners who aren’t familiar with you, just give us a little bit of your [00:01:00] origin story and just talk about the work you’re doing at Sophos.
Ross McKerchar, CISO Sophos: yeah, sure. Not a terribly exciting origin story. I’ve been at Sophos Almost straight out of university for 17 years now. Yeah started on the kind of Linux security side of things and i’ve just been lucky enough to grow with the You know grow with the company basically and you know build up build up a team as the company grew.
Ross McKerchar, CISO Sophos: My role now You know typical kind of CISO role, I guess responsible for kind of all aspects, you know all the way through from certifications and compliance through product security corporate security just the the full works here very similar to a CISO role, I guess another tech company.
Ross McKerchar, CISO Sophos: Although obviously doing it for a security company has its own kind of Unique set of challenges. And it does tend to draw you into the product side, I guess more than more than many other CISO roles, although corporates obviously important as well.
Paul Roberts (Security Ledger): Okay, so let’s talk about Pacific Rim report. Released on Halloween.
Ross McKerchar, CISO Sophos: Yep.
Paul Roberts (Security Ledger): I don’t know. It was pretty scary.
Ross McKerchar, CISO Sophos: It was generally a [00:02:00] coincidence. We were expecting the odd kind of bad headline from it. But by and large, it was fine.
Paul Roberts (Security Ledger): Pretty scary report. So for listeners who haven’t read it yet, and obviously we’ll link to it in the blog post that accompanies podcast. Could you give us just a rundown of this campaign and, what happened when Sophos became aware of this campaign and how it played out.
Ross McKerchar, CISO Sophos: Yeah, sure. So it is unusual compared to, normal reports of disclosures around specific campaigns. Cause we’re not just talking about one single event or incident. This is actually six years of back and forth with a kind of loose knit group of PRC, China based actors. It’s the main arc of the story, it kicks off with a more kind of, what I guess, a traditional attack, if you will, against a against a subsidiary of ours out in India through a company we acquired called Cyberoam. [00:03:00] That kicked off as a relatively run of the mill Incident we detected a scan a network scan of our Sophos environment originating from the the Cyberoam environment.
Ross McKerchar, CISO Sophos: We kept the companies relatively separate at the time of that attack. So we started tracing it back and found a compromise. It was one of those devices – it wasn’t a Raspberry Pi, I think it was an Intel knock, but it powers an overhead, like an overhead display in the office.
Ross McKerchar, CISO Sophos: So just a, just a little low powered device. Get into that, start doing forensics and it’s, quite uninteresting at this stage. Obviously it’s an internal, potentially internal breach, quite an important for us to investigate, but it looked relatively unsophisticated kind of basic Linux tradecraft, living off the land, standard Linux tooling.
Ross McKerchar, CISO Sophos: And then we start tracing the attack back. We’ll obviously clean it up, but that’s not enough. We need to understand How they got in, et cetera, et cetera. And there were a few points where as we trace this attack backs, we figure out where, what was the device that they logged in from, that they accessed the this little [00:04:00] NOC from, and it just gets this kind of series of escalating kind of situations where ” Oh, that’s quite clever!” “Oh, we haven’t seen that before.” “Oh, that’s interesting.”
Paul Roberts (Security Ledger): These don’t look like script kiddies,
Ross McKerchar, CISO Sophos: Yeah. Yeah. So we realized it wasn’t script kiddies, quite quickly in that incident. We saw, for instance we were using, this was an on premise environment, but we also had some of them some of these devices in that environment managed by AWS SSM, which is quite a new technology at the time they’d actually use that in a really interesting way to pivot into cloud assets.
Ross McKerchar, CISO Sophos: And that’s like a big uptick and capability from someone who, you, we thought that time was more standard common Linux tooling, open source malware. So that was interesting. And then finally we traced back what we now call Cloud Snooper. We disclosed at the time as Cloud Snooper, really interesting root kit, very stealthy.
Ross McKerchar, CISO Sophos: We took us, we actually had a couple of consultancies helping us through this and they, both of them did forensics on this system and couldn’t find it. It was only cause we’ve got some people on my team who who are very good at this as well. We actually found it internally, but yeah, very well [00:05:00] hidden.
Ross McKerchar, CISO Sophos: So that was just the first the first incident.
Paul Roberts (Security Ledger): So now you’ve got advanced cloud based techniques and a custom root kit. So now you’re thinking, okay.
Ross McKerchar, CISO Sophos: Yeah. Yeah. So now we’re thinking, okay. We thought, okay, this is gonna be, this is gonna be hard work. So we, it was actually one of the major catalysts for us integrating that company entirely. We essentially just burned it all down to the ground and built it back up again. Cause we knew it was a pretty nasty situation, but we didn’t realize at the time was that was just the start. What we now know was that was a reconnaissance gathering exercise. They had wider ambitions that the target wasn’t really us. The target was our customers. And I think about 18 months after that maybe a couple of years, actually during the middle of COVID.
Ross McKerchar, CISO Sophos: Where we saw this kind of higher scale activity kickoff, the Covid link’s important because they were attacking, not us, but our customer devices in the field. And because of Covid, a lot of our customers had configured their firewalls to be much more [00:06:00] remotely accessible than they were previously.
Ross McKerchar, CISO Sophos: ’cause obviously everyone had gone had, had gone to work from home. So things like administrative portals that maybe wouldn’t necessarily be so commonly. configured to be on the internet were , internet and WAN facing. So that was a kind of what I’d say is an at scale attack. It was targeting, tens of thousands of our customers. And we were a bit on the back foot at that point in terms of, we found out about it because of a customer report which I don’t like to do, obviously much better to find out about things before your customers find out about things.
Ross McKerchar, CISO Sophos: And what we now know, they were trying to build what we call orbs. So operational relay boxes. It’s not a Sophos term. That’s, that’s used quite a lot. A subset of a type of botnet, basically. But, used by, more advanced attackers to obfuscate the true origin of the attacks.
Paul Roberts (Security Ledger): You bring up orbs and this is a really interesting kind of Concept that I think has emerged in the past few years. So these are often kind of low value could be consumer devices or kind of low value but internet [00:07:00] connected devices that nation state actors will assemble and then utilize as a platform for second and third stage attacks
Ross McKerchar, CISO Sophos: That’s right. Yeah. I’m, I think the term actually originated in the intelligence community. You’re like the five, I think the five eyes use this kind of terminology a bit but I think it’s becoming more industry standard as well, Google Mandiant did a good article on, on, on them as well.
Ross McKerchar, CISO Sophos: Yeah. They’re basically botnets, but I think more specifically they’re botnets used for a very distinct purpose. We’re not talking about, DDoS wars script kiddies here. And whilst you had, they can be built out of maybe lower value devices. I think they, I think that the actors actually quite like enterprise devices as well for these, because if if you’ve got, if you’ve if you’re on a, an edge device in an enterprise in the same country as your end target, that’s just a brilliant place to be.
Ross McKerchar, CISO Sophos: You’ve got high bandwidth, you’re always on, you’re coming from a trusted IP space. You know obfuscates your true origin. So I think PRC (People’s Republic of China) based actors, [00:08:00] the various typhoons particularly are well known to use these these types of techniques and I think it’s important for Maybe mid market organizations particularly to think about these kind of threats historically ransomware has been the big driver of, of kind of risk for those organizations and maybe not considering the more nation state actors as being interested in them but if you are, at this point you become collateral damage in a wider operation where your infrastructure can be abused to attack another organization, not a great situation but then there’s actually other reasons why, the mid market might be a target for some of these for particularly PRC based actors, they’re known to be pre positioning themselves to target critical infrastructure as well.
Ross McKerchar, CISO Sophos: And. A lot of a lot of the mid market, they might not, some of them do, but they might not all have a very high value intellectual property, but they could be, like a, hospital healthcare, maybe not a lot of IP in that environment, but [00:09:00] it’s absolutely, very important critical infrastructure.
Ross McKerchar, CISO Sophos: So that’s another reason why, you know, as well as building offs at the mid market really needs to, or the whole market, not just the mid market, the whole market really needs to think about their hygiene when it comes to running these these devices on their on, on, on their perimeter and obviously not just Sophos devices, one of the key learnings and as we’ve collaborated with others on this report, and just, looking at news events is that this targeting of these perimeter devices is really prolific.
Ross McKerchar, CISO Sophos: If you look at the CISA’s latest report on the KEV list. They’ve listed out I think list out the top 15, the top six of those top 15 are all perimeter device attacks. And interestingly, they also call out a lot of use of zero days as well, much more than there were last year. So yeah, the threat is high at the moment.
Ross McKerchar, CISO Sophos: It’s a really challenging area for the industry. And that’s one reason why we’re so keen to, to do this report. Just get that Get that understanding out there.
Paul Roberts (Security Ledger): In [00:10:00] your research. I’m guessing that wasn’t the only appliance they were targeting, that you were part of a broader campaign of just whole category of these types of edge devices.
Ross McKerchar, CISO Sophos: we’re pretty confident of that. One, one, because we are, we’ve collaborated other vendors and I think as we’ll get to this part of the story in a bit, but we we got pretty good at identifying some of the kind of behind the scenes groups that we’re actually doing some of the exploit development, and we actually, with some other vendors, We shared some of that Intel quite a few years ago now, and they were seeing activity from those, from that, from those same cluster, cluster of IP addresses.
Ross McKerchar, CISO Sophos: Secondly, we with law enforcement help, we managed to gain access to one of the C2 servers. And actually we took that over. We gain access to the domains through a court order. We then point that domain at a server under our control. Not one of the attackers servers, and then we can see all the HTTP requests coming in, all the C2 and the user agent strings that were associated [00:11:00] were not our user agent strings.
Ross McKerchar, CISO Sophos: And obviously user agent strings, you can’t be a hundred percent confident in, but you can, they’re indicative of there are clearly other vendor devices in, in those. So yes, this is definitely, an industry wide concern for sure.
Paul Roberts (Security Ledger): So one of the really interesting aspects of the Pacific Rim report was the inferences you were able to make about the structure of China’s Offensive cyber operation, how you get that you were able to trace back the origins for some of these compromises to universities and private sector firms within China, who it would seem are working hand in glove with.
Paul Roberts (Security Ledger): The, l. A. or at least the Chinese Communist Party as part of these larger campaigns. I don’t think anybody’s going to be like, oh, my God, I can’t believe that. Yeah, we’ve all assumed that’s going on, especially, in wake of China, [00:12:00] requiring 1st, look at 0days and vulnerability discoveries, but talk to us a little bit about that and how that kind of played out in terms of the attack.
Ross McKerchar, CISO Sophos: Yeah, that was certainly, we found ourselves with this kind of really fascinating and unique insight into this. So we didn’t see it all, we don’t claim to understand the whole ecosystem and, others, the Atlantic Council, for instance, have done some really good research on this and what we see, what we observed, it was more like we could just go deep into a specific kind of part of that ecosystem.
Ross McKerchar, CISO Sophos: So the way that unfolded was in some of these first kind of widespread attacks that we that we responded to against our customers, we started to see in our device telemetry, these individual systems that had the same indicators of compromise as the rest of the rest of the fleet, but far earlier.
Ross McKerchar, CISO Sophos: Like months before, and we were initially thinking, Oh, maybe they were testing it. Maybe, maybe this was just like an [00:13:00] unfortunate kind of early victim, but we as we dived into that more and started to marry up Some of that data with our other back office systems, the kind of like the registration systems that you need to get, these are all virtual, primarily virtual devices.
Ross McKerchar, CISO Sophos: So you can go on a website, you can download a a copy of our XG software and run it as a VM. The attackers did later actually get the hands on physical kit, but we’ll get back to that, get back to that later. So we So we started to actually change our minds about what we were seeing, and it started to look more like this wasn’t a, an actual attack.
Ross McKerchar, CISO Sophos: It was more of a test of an, a test of an attack. So we start pulling on this thread. Again that’s interesting. We were doing that at the same time as responding to the first wave of attacks. And then there’s only a couple of weeks after responding to the first wave, whilst we were trying to get our hands on, figure this out, Second wave of attacks hit us.
Ross McKerchar, CISO Sophos: This was really interesting because it was a very different type of attack Like it’s really like they’d learned their lesson in the first wave [00:14:00] of attacks but we were more prepared. We rolled out some improved telemetry across our environment. This is like internal system telemetry, it’s things like hashes of unexpected files, processes on disk things like that, and we so we were slightly better prepared and that second attack gave us again, a little bit more insight into these into these actors and then we, and it was actually the, it was between the second and the third attack that we made the big leap where we were like, okay, these are definitely attacker devices.
Ross McKerchar, CISO Sophos: We are very confident in that it’s not just vulnerability research. It was exploit development and the difference being the, it wasn’t about finding the initial ways in, because obviously there’s lots of kind of legitimate vulnerability development that goes on across the world. It was about chaining the way in with deploying kind of stealthy malware onto the devices.
Ross McKerchar, CISO Sophos: So we were confident that this is, it’s very likely kind of malicious kind of illegitimate activity. [00:15:00] We were confident it was originated in the Chengdu region of China. So I guess the unusual step we took, which has got, had a lot of commentary across the industry was we had this telemetry that gave us a kind of like broad view. It’s think of it like a basic EDR, but we really needed to get closer. To these devices to really understand what’s going on. That’s when we deployed the what we call the targeted implant. it was a stealthy way. No problem. I still, a stealthy way of of us like really monitoring. The the attackers and the devices, we can get near, near term, near real time, what they’re typing, typing in the key on the keyboard, running, putting commands on the system.
Ross McKerchar, CISO Sophos: That alone is unusual in a firewall because you don’t typically log into a firewall shell and actually type commands on the shell. Obviously, you’re configuring it through, a web interface or code. So that really proved it’s worth quite quickly, actually, because we actually managed to get our hands on a On an exploit or [00:16:00] vulnerability they had and they were turning into an exploit to we, and then patch it before they used it.
Ross McKerchar, CISO Sophos: So that was the first real indicator, the first real kind of measure of success that we had, we we have to do funny things like we had to patch it like accidentally, like stealthily, because we were worried they were monitoring our hot fixes. So we’re playing this real kind of this kind of game of like thinking, like treating it like a game theory problem, trying to like second guess, what they knew what they were looking at.
Ross McKerchar, CISO Sophos: But we realized at this point we had this really valuable capability. And we were just able to milk that over a period of about two, two, three two, three years to to try and stay ahead of these of these adversaries. So they so they weren’t able to use that third vulnerability at scale. We managed to patch that. And after that, I think they it basically looks like they gave up on trying to do mass exploitation and build up these orbs, but by that point we’d instrumented our firewall a bit better and we’re much more paying really close attention to this stuff.
Ross McKerchar, CISO Sophos: And that allowed us to [00:17:00] unlock this kind of ecosystem of. Much more targeted activity. So like high value targets so that the activity we observed really pivoted from those mass widespread attacks into Just a real threat intelligence goldmine of really interesting victimology, very kind of obvious ranging from like obvious espionage targets through to critical infrastructure targets We could marry up a lot of the activity that we saw with kind of ccp Objectives like political objectives and even the travel, even the travel itineraries and Travel plans as well.
Ross McKerchar, CISO Sophos: So we saw You know embassy, being targeted It shortly before that embassy was due to host a CCP dignitary. So it was, yeah, really interesting activity as well as really interesting malware, that’s when we managed to uncover some very interesting except some other root kits and all the way up to a quite sophisticated root kit as well as even a boot kit, which is, you fee very low level malware.
Ross McKerchar, CISO Sophos: Yeah, it was an interesting few [00:18:00] years. That’s for sure.
Paul Roberts (Security Ledger): The targeted implant aspect of it is 1 that, as you said, it has gotten a lot of attention. Sometimes it’s got a little bit of a little shadow over it. But in this case, as you said highly useful in the context of a sophisticated nation state campaign of trying to, stay one step ahead of a, very widespread and sophisticated operation.
Paul Roberts (Security Ledger): Is this something that more organizations should be looking at rather than trying to, button every button and, check every lock in their, incredibly. Diverse it ecosystem of saying, what can we do to learn more about what they’re up to, and prepare.
Ross McKerchar, CISO Sophos: Yeah, I think that’s a good, that’s a really good question that kind of hits at the heart of why we were so keen to talk about this, knowing it was device that we already had code execution on.
Ross McKerchar, CISO Sophos: So it wasn’t like there was anything clever to get code running on it. Of it as defending forward like monitoring kind of threat intelligence collection. To defend our customers. And there’s [00:19:00] clear value, obvious successes doing that.
Ross McKerchar, CISO Sophos: But it’s a re it’s a really good question because I think there is a lot of value in applying what I just call generally, detection and response principles to edge, edge devices. And I think it’s an, “and: not an “or.” So I think we, we need to continue to harden these devices. A lot of them, I’m speaking, across the industry here, not specifically on software.
Ross McKerchar, CISO Sophos: So we obviously invested very heavily in, in trying to shore up our devices as a result of some of this activity. But as an industry, a lot of these devices have quite legacy architectures. They weren’t really built to sustain. To withstand such a intense adversarial ecosystem where you’re talking about, what I understand is you have very large numbers of people doing really deep exploit research.
Ross McKerchar, CISO Sophos: Like we talked about legislation when we get back to that, but like PSC legislation has really co opted the entire country, I think it’s the second [00:20:00] largest country in the world by population right now, into like be able to harvest that, that entire country to identify exploits against these devices.
Ross McKerchar, CISO Sophos: So we have to recognize that whilst we have a lot of work to do to harden them and make them much harder to, exploit, we need a plan for failure. This is a lesson that we learned in the endpoint world, probably 10 years ago now, maybe even 15 years ago, where we made that shift from antivirus to endpoint detection and response. we realized that you have to have a plan for if your AV doesn’t catch something. And that kind of gave birth to the endpoint detection response,, movement. And now we’re at the point where, if you have good EDR deployed, and you are crucially monitoring it well, which is obviously where things like MDR come in because a lot of organizations aren’t capable of monitoring, monitoring EDR themselves.
Ross McKerchar, CISO Sophos: It’s hard, right? But if you have that and you’re looking at it and it’s well deployed and it’s, a leader, a leading solution like ours, then it’s [00:21:00] actually quite hard to persist in a corporate network. And actually that’s why, that’s one good reason I think why we’re seeing threat actors go to, go to these devices because we haven’t learned that lesson.
Ross McKerchar, CISO Sophos: So yes to answer you bluntly, whilst we shouldn’t, you, it shouldn’t be too big a distraction from hardening these devices. It very much is an, and we should definitely be thinking about how we can detect and respond in these environments as well to to counter this threat.
Paul Roberts (Security Ledger): the next question is the hardest one for a software publisher, which is, as you said, a lot of these campaigns are contingent on 0days or, known exploitable vulnerabilities in. Commercial software, right? Whether that’s VPN software or what have you. Um, what does that mean for a company like Sophos in terms of your approach to, as you said, hardening devices and software that you’re deploying to your customers.
Paul Roberts (Security Ledger): [00:22:00] And given that, We know you’re never going to be able to be perfect, right? Like you, you’re writing, hundreds of thousands of millions of lines of code, like there’s going to be X number of vulnerabilities in it. This is unavoidable. But now we know they’re really targeting this.
Paul Roberts (Security Ledger): They’re spending significant resources to find and exploit these vulnerabilities. How does that change things from a software publisher’s point of view?
Ross McKerchar, CISO Sophos: Yeah. Yeah. Another reason we wanted to release this report is that we think it’s a more constructive conversation to have if we recognize that secure software development is really hard. I, that sounds old, that might sound obvious, but I
Paul Roberts (Security Ledger): And expensive.
Ross McKerchar, CISO Sophos: Yeah. And expensive. Yeah. Yeah.
Ross McKerchar, CISO Sophos: That might sound obvious, but I think a lot of the security industry has relied on pretending everything’s perfect. No, pretending that we can, build perfectly secure software, not having a plan, not having a plan for failure. That’s changing.
Ross McKerchar, CISO Sophos: So there [00:23:00] are initiatives like the Scissor Secure by Design Initiative. Which we’ve really leaned into, we sat, we signed up alongside, many other vendors that’s got a lot of momentum. We’ve actually published like quite detailed blog article quite early on around how we’re trying to Not just adhere to the core principles, which we by and large met already, but taking it to the next step.
Ross McKerchar, CISO Sophos: Things like , unfishable FIDO2 based authentication, for example in, in our products, as well as, moving to more modern memory safe, more memory safe languages, as an example, we’ve rewritten our, A VPN provisioning portal is a very exposed component because obviously if you want someone to be able to Get on a vpn and they don’t and they’ve got a new device and you don’t want them to visit the office Then they obviously need to be able to get into the portal to download the client.
Ross McKerchar, CISO Sophos: So a lot of customers have that We prefer they went into the office to, to get that, but that’s just not always realistic. So a lot of customers. Have that as an internet facing component, that [00:24:00] means it’s much more attack. We’ve very, we’ve recently rewritten that in go using, very very,
Paul Roberts (Security Ledger): Memory safe language.
Ross McKerchar, CISO Sophos: Yeah.
Ross McKerchar, CISO Sophos: And also using our most modern S-S-D-L-C process, which has evolved with the time. And I think a lot of vendors in this place. It’s not it’s not like we are necessarily churning out code, really subpar below code. For like today’s environment now, but our SSL SSDLC process is 10 years ago.
Ross McKerchar, CISO Sophos: When, we’re maybe not up to scratch for the threat environment now. And this is particularly true in firewalls because they tend to have much longer life cycles. And then actually in our case, it was even more challenging than that.
Ross McKerchar, CISO Sophos: Because some of this code comes from mergers and acquisitions. So it was written, it was written by a team that didn’t follow my SSDLC process because they weren’t my team at that point, if you follow me. So yeah there’s a lot of work to do. We’ve we’ve, we’ve invested heavily, we’re really [00:25:00] focused.
Ross McKerchar, CISO Sophos: It’s like any other security problem. If you’re too myopically focused on one part, you’re probably going to fail. You need to, then the CSF is popular for a reason. You need to think about prevention, protection initiatives, risk identification, governing all that, but also have a plan for failure detection and response other ways that we really like that we find really effective are for instance, bug bounty programs, we have Our rewards for the firewall, I think, are up to 50k right now.
Ross McKerchar, CISO Sophos: I think we think that’s industry leading because the reality is finding everything internally is tough and there’s a big community out there that if you harness them in the right way can really can really help. We’re a fan of that. It also acts as a forcing function for your vulnerability disclosure processes.
Ross McKerchar, CISO Sophos: So doing things like releasing CVEs, being very transparent to help your customers also respond, we think is very important.
Paul Roberts (Security Ledger): Can I throw out another issue that’s close to my heart, which is end of life devices, right? End of life software and end of life hardware. [00:26:00] We know for a fact that the, Volt Typhoon and other actors are particularly interested in finding and exploiting end of life devices.
Paul Roberts (Security Ledger): Manufacturers, they don’t compel customers to stop using it once they’ve stopped supporting it, but it does seem like there’s a public health risk for these devices that we need a way to address. And I don’t know what the, I don’t know who it falls to be the cop on the beat for that.
Paul Roberts (Security Ledger): But I, I’m interested in your thought or Sophos thought on what do we do about all this end of life
Ross McKerchar, CISO Sophos: I’m really glad that you brought that up actually, cause that’s, that that’s the third phase of the of the attacks that we saw. So at. As we got better and better at burning the the operations and also showing up our firewall platform as well, we just increasingly had this kind of end of life, which we call this digital detritus problem where only the customers that are still our customers upgrading the devices are getting all these fixes.
Ross McKerchar, CISO Sophos: So you still end up with this kind of [00:27:00] vulnerable, old pop, old population that, as you say, it’s not just about the risk to that organization. They might have a very, a very kind of high risk tolerance. They might not care, frankly, but there’s a there’s a greater risk to our kind of overall digitally ecosystem.
Ross McKerchar, CISO Sophos: The one thing that we’ve, that we know is that we can Act unilaterally on this, if we got really aggressive and push customers too hard, who, have their budget constraints, who have, their resource constraints they’re simply going to go to another vendor, that’s, so that’s not going to be good for our business, but it’s also not going to be good for the good for the ecosystem.
Ross McKerchar, CISO Sophos: So we’d love to see more. Kind of collaboration and standards on this, even things like just standardizing on terminology, end of life versus end of sale, what they should be like, what steps are acceptable to take across your end of life population what industry [00:28:00] convention, industry conventions around this area, we think would be really helpful to
Paul Roberts (Security Ledger): There’s a public health epidemiologic angle to this, right? Which is if we have vaccines, but we charge $300 for them, then okay, sure. Affluent people will get vaccinated, but most people won’t and diseases will still spread. And that’s what you’re talking about, which is listen, if I’m a small business five or 10 person business, it’s on my budget to, keep upgrading this device, but it seems to be doing what I bought it to do.
Paul Roberts (Security Ledger): So I’m just going to leave it. From their standpoint, that’s fine. But from the broader public health standpoint, it’s really a problem, or the broadband routers or the smart TVs or whatever, right? As long as that smart TV is still showing me Netflix, I really don’t care if it’s running the latest, software and is patched.
Paul Roberts (Security Ledger): And I actually don’t really care if China’s on it, but we as a society and we as an economy, we definitely care because that becomes a platform for bigger, uglier attacks.
Ross McKerchar, CISO Sophos: Yeah, [00:29:00] absolutely. The start, I think the start is just having a common standard on how long devices are supported for, when they get end of life, it’s impossible. People might say why don’t you just backport patches, for forever. Hardware evolves, right?
Ross McKerchar, CISO Sophos: We can’t run our latest software on a on hardware that was built 10 years ago. So there’s a backstop there. Risk also goes up, we’ve obviously we’re, the industry’s Very recently learned about the risks of a large widespread update going out across a lot of systems quickly.
Paul Roberts (Security Ledger): Vendor will not be named, but yes. Yes.
Ross McKerchar, CISO Sophos: If vendors have to, we have to test these updates. And, hardware changes over time, software changes over time. So you get this you get this kind of combinatorial problem where you have to test on huge numbers of different versions of hardware and software, and it just gets extremely complex.
Ross McKerchar, CISO Sophos: There’s more problems, the more likelihood that you’re going to screw that up. So you so there’s a lot of good reasons why vendors can’t. Can’t, can’t can’t support forever. Or [00:30:00] TPMs, old devices don’t have TPMs and TPMs are keen for, critical for for kind of modern defenses.
Ross McKerchar, CISO Sophos: So yeah, it’s, I don’t have the solution, but I certainly know it’s an area that needs needs a lot of attention for, for our kind of collective digital resilience.
Paul Roberts (Security Ledger): There needs to be some structure, right? Because right now, it really comes down to the individual vendor, the individual customer. It is totally, it’s a wild west, as we would say here in the US but I think we’re, We’re seeing the result of that which is very fertile ground for bad actors
Paul Roberts (Security Ledger): OK, final question: one of the big conclusions out there was that you know as you said earlier that nation state actors China, are interested in high value targets, but they are also involved in campaigns against what we would not consider to be high value targets, usually as a precursor to these later stage campaigns. What do we need to do to adjust our defenses and approach to account for that?
Ross McKerchar, CISO Sophos: I’ll start by saying we, we shouldn’t just assume that it’s [00:31:00] a what the economists call it, a negative externality, like a, it’s not just someone else’s problem. Although in the case of orbs, that’s likely the case that the attackers on your devices, they’ll also do.
Ross McKerchar, CISO Sophos: Everything they can to rotate to gain extract other values. So they’ll steal your credentials from that, from that device. And then they’ll, and then they’ll likely use that for, credential stuffing campaigns in the in, in the future. And as I already said as well, if, even if you’re not a an espionage target, you might very well be a critical infrastructure. And I think a lot of companies don’t think of themselves as critical infrastructure, but they are. You know, you’re logistics….
Ross McKerchar, CISO Sophos: Right?
Ross McKerchar, CISO Sophos: you might be a small delivery company, but depending on what you’re delivering, you’re very likely critical infrastructure. A lot of examples, a lot of examples of that. And of course, just from your own business perspective, availability, lack of availability is going to hit you financially as well.
Ross McKerchar, CISO Sophos: So I think we need to, we definitely need to move past this idea [00:32:00] that ” I’m not a target.” ” there’s not, there’s nothing of value that I’ve, that I’ve got” that kind of apathy, which is particularly common maybe in the more, in, in the smaller end of the market en enterprise enterprises.
Ross McKerchar, CISO Sophos: More tuned on, tuned into this, obviously intellectual property theft is, that can be very damaging. I think there’s a part to play for a wider policy part to play like outside this, the kind of cyber realm where we’ve essentially let. IP theft go unpunished for a very long, for a very long time.
Ross McKerchar, CISO Sophos: I think there’s, targeted economic sanctions, things like that, if there’s a demonstrable kind of economic headwinds from, if products getting sold back into an American market, for example, which are clearly the result of IP theft, this is not a, This is not a, this is not simply a technical problem.
Ross McKerchar, CISO Sophos: It is a it’s increasingly a geopolitical problem that that we need to solve as a society. I think if we just focus on the technical [00:33:00] problems it’s an unfair fight in many ways. You’ve got a lot of very sophisticated people doing a lot of research. You can’t expect even the best – even the Fortune 50 to do that on their own. There’s definitely, there’s a government part to play here as well. There’s a legislation, wider part.
Paul Roberts (Security Ledger): Ross McKerchar, CISO at Sophos. Thank you so much for joining us on Security Ledger Podcast and I’d love to have you on again.
Ross McKerchar, CISO Sophos: Thank you.
Narrator: If you liked what you heard, subscribe to The Security Ledger podcast or check us out on your favorite podcast app. including Spotify, Apple Podcasts and Amazon Music.






