In-brief: We speak with Sean Dillon of the firm RiskSense, who helped reverse engineer DoublePulsar and EternalBlue, the Windows exploit tools used to help spread the WannaCry ransomware. We also chat with John Dickson of The Denim Group about the impact of President Trump’s Cyber Executive Order.
Last week was one for the record books. For the first time in almost a decade, the world bowed down to the ravages of a virulent Windows-based worm, this one absent a name, but bearing a gift in the form of ransomware dubbed “WannaCry.”
Starting early Friday, the virulent Windows-based worm infected and locked down data on more than one hundred thousand systems, shutting down more than 16 hospitals in the UK and hobbling telecommunications firms across the globe.
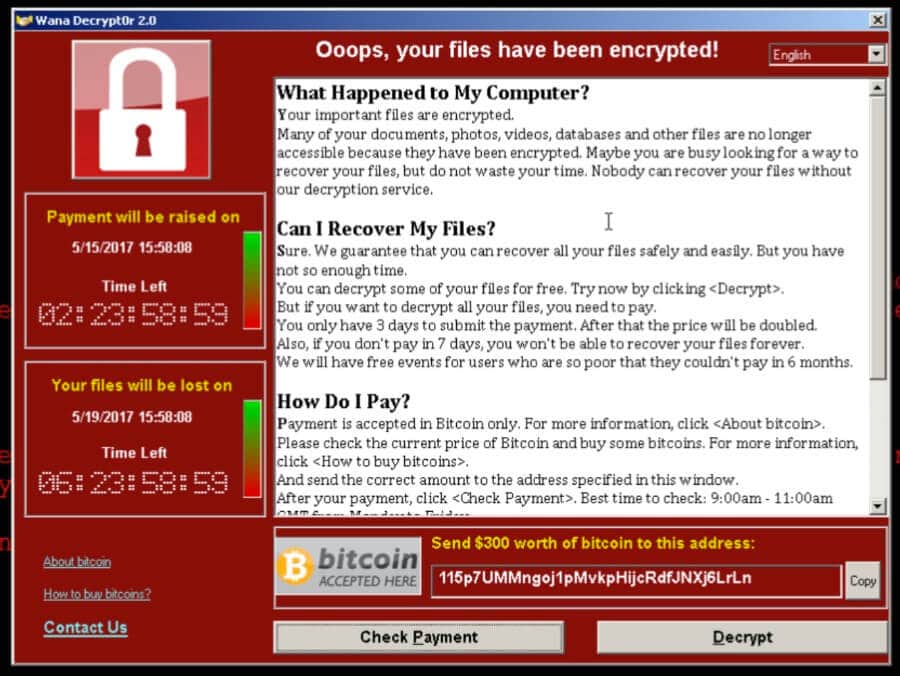
Under the hood of the ransomware outbreak were exploits for a core Windows component, SMB – or Server Message Block. Those exploits are believed to have been derived from an offensive hacking toolkit used by U.S. intelligence services and then stolen and leaked by a group known as Shadow Brokers.
But wait…that’s not all. Also this week, President Donald Trump made good on a campaign promise this week, signing a long-awaited cyber security order for “strengthening the cyber security of federal networks and critical infrastructure.”
The Executive Order had been promised within the first days of Trump taking office in January. However, it was postponed to allow more time for federal agencies to weigh in and contribute to the final draft.
The result? Decidedly mixed. The EO makes good on some of candidate Trump’s campaign promises, including calls for a top-down review of government cyber security and demands for agency heads to be held accountable for breaches on their watch.
But cyber security experts sounded notes of caution: noting that the EO makes few substantive recommendations compared to what preceded it. The EO also puts the onus on the Federal Government, with little discussion of the role that private sector firms can and should play in helping improve the security of government systems or critical infrastructure. The Information Technology Innovation Foundation , a non-partisan Washington DC called it “mostly a plan for the government to make a plan.”
To help sort out these issues, we invited a couple of experts into The Security Ledger studio. Sean Dillon is a senior security analyst at RiskSense, he’s been following the advance of the WannaCry ransomware attacks and has researched DoublePulsar and EternalBlue, the Windows exploits that are the primary payloads used in the NSA hacking framework. Sean says that exploits like these don’t come along very often and they help account for WannaCry’s rapid spread.
And we talked with John Dickson, a Principal at the Denim group regarding President Trump’s Cyber Executive order. John said that, while there’s much to admire in the Trump Administration’s Cyber Executive Order, many questions remain unanswered. Among the most important: how the government will overcome its cumbersome, expensive and inefficient process for procuring software and services.
Check our full conversation in our latest Security Ledger podcast below or at Soundcloud. You can also listen to it on iTunes. As always, if you like our intro music, give some love to the group JoeLess Shoe, who recorded “Baxton,” the song we use in just about every podcast.
