The dangerous security hole in OpenSSL known as “Heartbleed” has (mostly) faded from the headlines, but that doesn’t mean it isn’t still dangerous. As this blog has noted, the Heartbleed vulnerability was patched quickly on major platforms like Apache and nginx and by high profile service providers like Google and Facebook. But it still has a long tail of web applications that aren’t high risk (i.e. directly reachable via the Internet) and embedded devices that use OpenSSL or its various components.
As the folks over at Acunetix note in a blog post today, hundreds of other services, application software and operating systems make use of OpenSSL for purposes that might be entirely unrelated to delivering pages over HTTPS. This includes all the email servers (using SMTP, POP and IMAP protocols), FTP servers, chat servers (XMPP protocol), virtual private networks (SSL VPNs), and network appliances that use OpenSSL or its components. The number of systems vulnerable to Heartbleed, then, is almost certainly much larger than originally estimated.
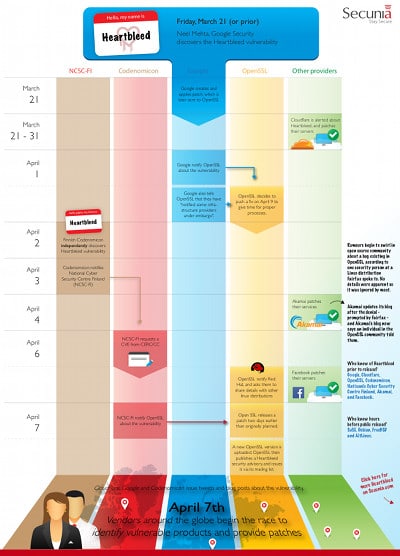
To help us understand where we are in the Heartbleed “incident response” timeline, Secunia has put together a nice little infographic that brings us up to date. It includes the initial discovery of the hole between March 21 and April 7 and arranges events according to the perspective of the organizations responsible for bringing it to light: NCSC-FI, Codenomicon, Google, Open SSL and Other Providers. The company has written about why Heartbleed had such an outsize impact. Secunia is also hosting a webcast tomorrow to discuss the disclosure of Heartbleed and how the uncoordinated disclosure of the vulnerability complicated organizations’ efforts to respond to it.

Pingback: Report: Community Health Hack Linked To Heartbleed OpenSSL Hole | The Security Ledger
Pingback: ShellShock's Long Tail in the Enterprise | The Security Ledger | The Security Ledger