Attempted cyber attacks on critical infrastructure in the U.S., including energy and critical manufacturing jumped sharply in the first half of 2013, according to a just-released report from the Department of Homeland Security’s Industrial Control System Cyber Emergency Response Team (ICS-CERT).
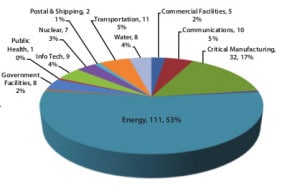
ICS-CERT said that cyber incidents across all critical infrastructure in the U.S. are on pace to double in 2013. The agency has responded to 200 such incidents so far in fiscal year 2013 (October of 2012 to May of 2013), compared to 198 incidents for all of fiscal year 2012. A majority of those incidents – 53% – were against organizations in the energy sector, ICS-CERT reported.
The report is just the latest from DHS about threats to the energy sector. The agency warned energy firms after seeing a sharp jump in attacks during 2012, when attacks on energy firms accounted for around 40% of the malicious activity directed at critical infrastructure.
According to DHS, the cyber incidents reported represented a “wide variety of threats ranging from Advanced Persistent Threats (APT), to sophisticated and common malware found in the ICS environment.” Other attacks were less sophisticated. DHS noted incidents in the water and commercial sectors linked to weakly protected Internet-facing systems that used weak or default credentials.
The critical manufacturing sector was the next most common target, accounting for 17% of the cyber incidents reported to ICS-CERT. DHS said the majority of those incidents involved attacker techniques such as watering hole attacks, SQL injection, and spear-phishing attacks.
The information was included in the ICS-Monitor report covering April, May and June of this year. DHS said that, in five instances, it deployed on site teams to help the affected organization assess the breadth of the incident. That compares with six on site deployments in all of 2012. Three of the on site visits were in the energy sector and two were in the critical manufacturing sector, DHS said. All concerned breaches linked to “sophisticated threat actors who had successfully compromised and gained access to business networks.” The ICS-CERT incident response team went on site to determine if ICS networks were also compromised, but often found that there was not enough usable logging and cyber forensic data to make a determination.
The report is just the latest to raise issues about the security of critical infrastructure in the U.S. In April, the security firm Rapid 7 disclosed widespread security flaws and insecure configuration of ubiquitous networking components known as serial port (or “terminal”) servers that exposed a wide range of companies and critical assets – including point of sale terminals, ATMs and industrial control systems – to remote cyber attacks. In January, security researchers Billy Rios and Terry McCorkle published a report showing that industrial and medical systems manufactured by the same firms contain many of the same critical software security problems.
The report is further proof that the energy sector is perceived as a target by external actors said Lila Kee, the Chief Product and Marketing Officer at the firm GlobalSign and a member of the North American Energy Standards Board.
“Although attacks on major gas and electric systems are nothing new to those in the industry, these facts serve as evidence that low-level criminals, all the way up to state-sponsored groups see the value in compromising our nation’s critical infrastructure,” she said.