In brief: A report studying compromised networks from the firm Vectra finds a big jump in “lateral movement,” as hackers delve deeper into hacked organizations.
Tag: Black Hat
Dusting For Malware’s Bloody Prints
Malicious software is nothing new. Computer viruses and worms have been around for decades, as have most other families of malware like remote access tools (RATs) and key loggers. But all our experience with malware hasn’t made the job of knowing when our organization has been hit by it any easier. In fact, recent news stories about breaches at Home Depot, Target, Staples and other organizations makes it clear that even sophisticated and wealthy corporations can easily overlook both the initial compromise and endemic malware infections – and at great cost. That may be why phrases like “dwell time” or “time to discovery” seem to pop up again and again in discussions of breach response. There’s no longer any shame in getting “popped.” The shame is in not knowing that it happened. Greg Hoglund says he has a fix for that latter problem. His new company, Outlier Security, isn’t “next generation […]
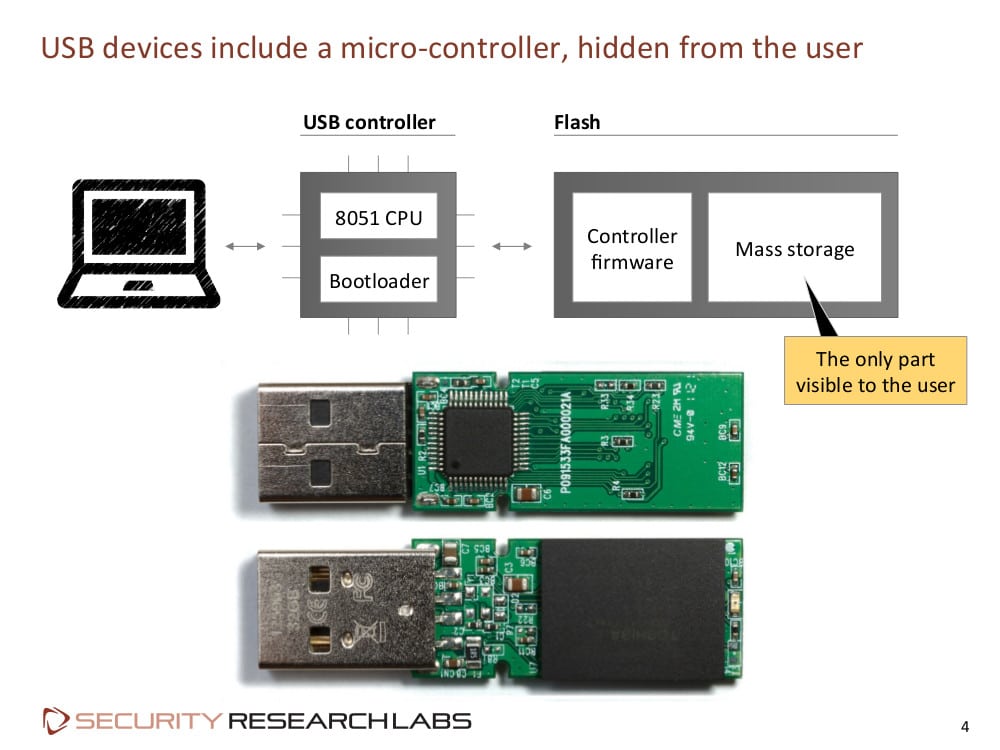
Unpatchable USB Malware Now Open Source | WIRED
Andy Greenberg over at Wired has an interesting piece of news coming out of last week’s Derbycon hacker conference in Louisville, Kentucky. According to Greenberg and Wired, researchers Adam Caudill and Brandon Wilson showed off their own version of Karsten Nohl and Jakob Lell’s BadUSB malware, and that they’d released the code on Github. Their presentation raises the stakes for USB manufacturers to fix the BadUSB problem or leave hundreds of millions of users vulnerable, Greenberg writes. At a presentation at the Black Hat Briefings in August, Nohl and Lell, both of Security Research Labs (SRLabs), showed how the controller chips inside common USB devices can be reprogrammed, allowing USB peripherals to impersonate other kinds of devices. Among other things, Nohl demonstrated how a BadUSB infected device could emulate a USB keyboard, issuing commands to a connected machine using the permissions of the logged-in user. Alternatively, an infected USB could spoof a […]
Exploding Gas Tanks: Risk, Liability and Internet of Things
We like to construct Hollywood friendly plots around a lot of the seminal moments in our collective history. For Civil Rights, we like to picture the integration of Little Rock High School, Rosa Parks’ courageous protest on a Montgomery bus or the March on Washington. For environmentalism, we talk about Rachel Carson’s Silent Spring or, maybe, the burning Cuyahoga River in Cleveland. (This vintage news footage of the 1969 fire calls it the fire that “sparked the environmental movement” without any apparent irony.) For automobile safety, we imagine Ralph Nader and the image of a 1972 crash test that shows the gas tank of the Ford Pinto exploding in a rear impact collision, engulfing both cars in flames. But those memories are often way oversimplified. Little Rock and the Montgomery bus boycott were just two battles in a fight for civil rights that went back to the end of the Civil War. Likewise, the Cuyahoga […]
McAfee sideshow eclipses Defcon’s real security breakthroughs | Security – InfoWorld
The onetime technology wunderkind, who left a job working for Lockheed to turn his curiosity about computer viruses into a thriving, global corporation showed up at two Las Vegas hacker cons last week: B-Sides Las Vegas and DEFCON. He offered some off-the-cuff rebukes to firms like Google. He also rambled long and hard about the dark forces that pursue him: the U.S. government, the government of Belize, Central American drug cartels and script kiddies desperate for his (virtual) scalp. Everywhere he goes, people take his picture. Who are they working for? The phones and computers he buys are bugged. His movements are being tracked. Those in attendance were admonished to beware of government snooping — especially via mobile applications. “Without privacy there is no freedom,” McAfee intoned. Listening to McAfee rant, it’s easy to forget there were plenty of folks walking the halls of Defcon, Black Hat, and B-Sides […]