In-brief: Tune in to our conversation with Dell CISO Alan Daines on Friday, May 29th at 1:00 PM ET. Click the image above to register!
Web
Mobilizing SQL Injection Attacks: Same Pig, New Lipstick?
In-brief: New research from Akamai suggests that attackers are using new methods to carry out and cover up for malicious attacks, among them: harnessing harmless mobile carrier networks to carry out attacks such as SQL injection.
A Good Housekeeping Seal for the Connected Home?
In-brief: Experts on the security of the Internet of Things warned that lax security and privacy protections are rampant in connected home products, but consumers have no way of knowing whether the products they buy are easy targets for hackers.
Verizon: Internet of Things Hacks Pose Little Risk – For Now
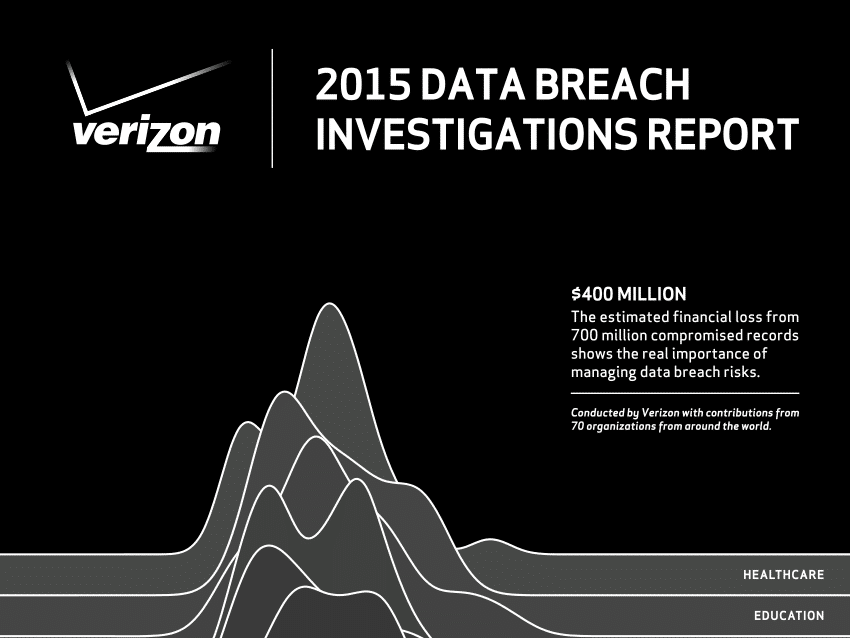
In-brief: Verizon said in its latest Data Breach Investigations Report that threats from Internet of Things technologies were more theory than practice in 2014, but that 2015 could see IoT devices play a role in breaches.
Update: CAs Still Accepting E-mail as Proof of Domain Ownership
In-brief: Carnegie Mellon’s CERT issued a warning that many certificate authorities continue to issue domain certificates with no more proof than the right e-mail address. Updated to include comment from GlobalSign. Paul 3/27/2015