With news of the breach of big-box retailer Target Inc. still in the headlines, the U.S. Computer Emergency Readiness Team (CERT) issued a warning about the danger posed by malicious software targeting Point of Sale (POS) systems. CERT issued an advisory (TA14-002A) on Thursday asking POS owners to take steps to secure the devices, and telling consumers to beware. The warning comes after a string of reports that suggest that malware attacking point of sale systems is on the rise. In December, researchers from Arbor Networks said they had detected an “active PoS compromise campaign” to steal credit and debit card data that used the Dexter and Project Hook malware. Dexter is a Windows-based program that was first discovered in December, 2012 by Seculert, an Israeli security firm. It is still not known whether malware played a part in the huge theft of credit card data from Target Inc. That […]
keylogger
NSA Toolbox Included Hacks For Juniper, Cisco, Dell
The German magazine Der Spiegel made headlines this week with its story detailing the US National Security Agency’s (NSAs) offensive hacking capabilities. The story is based on classified NSA documents absconded with by former contractor Edward Snowden and lays bare a Webster’s Dictionary full of classified hacking tools and programs. Among the highlights of the story: + The NSA developed and deployed a wide range of hacking tools that could compromise hardware from leading IT and networking equipment makers including Cisco Systems, Juniper Networks and the Chinese vendor Huawei and Dell Inc. + The NSA tools were designed to provide persistent access that allowed the NSA to monitor activity on the compromised endpoint, avoid detection by third party security software and survive software and firmware updates. One such tool, DEITYBOUNCE, provided persistent access to Dell’s PowerEdge servers by “exploiting the system BIOS” and using “System Management Mode to […]
Report: Cards Stolen From Target Used – at Target
The web site that first broke the news that data on millions of credit cards was lifted from box retailer Target now reports that those cards are being used to make fraudulent purchases at brick and mortar stores- including at Target itself. Writing on the website Krebsonsecurity.com, Brian Krebs said that so-called “dumps” of stolen card data are flooding underground “carder” web sites where cyber criminals fence stolen card information. Citing an unnamed source at a New England bank, Krebs said that the bank had, with his help, purchased about 20 cards for its customers that were offered for sale on rescator(dot)la, the carder web site, and confirmed that all the stolen cards had been used at Target. Furthermore, the source confirmed to Krebs that some of the stolen cards had already been used to make fraudulent purchases – including at Target and other big box retailers. Only one […]
Target Confirms Massive Breach – 40 million Credit Cards Affected
Black Friday just got a bit more black. Target Corp., one of the U.S.’s leading retail outfits, confirmed in a statement Thursday morning that reports of a massive breach of the company’s payment infrastructure, resulting in the exposure of data on an estimated 40 million credit and debit card accounts. The statement, released on Target’s website, follows media reports on Wednesday citing reports from leading credit card issuers. In it, the company confirmed “it is aware of unauthorized access to payment card data that may have impacted certain guests making credit and debit card purchases in its U.S. stores.” According to statements by Target, the credit card data was stolen between Nov. 27 and Dec. 15, 2013 and includes customer name, credit or debit card number, and the card’s expiration date and the CVV, or three-digit security code. Shoppers at the company’s U.S. stores were affected, but the breach did not affect Target’s Canadian […]
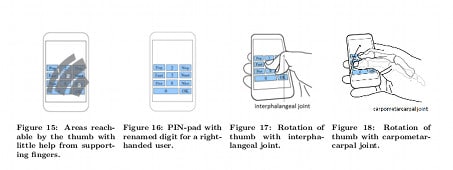
Hack Uses Phone’s Camera and Mic To Best Anti-Keylogger
Smart phones these days are bristling with sensors. Forget about the camera and microphone – there are accelerometers, Global Positioning System components, not to mention Bluetooth and NFC transmitters. All those remote sensors enable all kinds of cool features – from finding the nearest Starbucks to mobile payments. But they also pose a risk to the privacy of the phone’s owner – as malicious actors (and the occasional national government) look for ways to turn cameras and other sensors into powerful, cheap and convenient spying tools. Now researchers at The University of Cambridge have demonstrated one possible, new attack type: harnessing the built-in video camera and microphone on Android devices to spy on an owner’s movements and guess his or her password. The technique could be a way for cyber criminals to defeat anti-keylogging technology like secure “soft” keyboards used to enter banking PINs and other sensitive information. The work […]