The top news this week is about Wall Street giant JP Morgan Chase, which disclosed on Thursday that a previously disclosed breach was much larger than initially believed, affecting more than 75 million account holders. And once again, reports suggest that a compromised employee account may be at the root of the incident. Bloomberg, which first broke the news of the cyber attack on JPMorgan Chase in August, said on Friday that hackers exploited an employee’s access to a development server as part of an attack on a JPMorgan Chase & Co. server that led to one of the largest cyber-attacks ever and the theft of data on 76 million households and 7 million small businesses. According to the Bloomberg report, which cited “people familiar with the bank’s review,” the breach started in June when an employee’s user name and password for what’s described as “a web-development server” were compromised. From that […]
Fraud
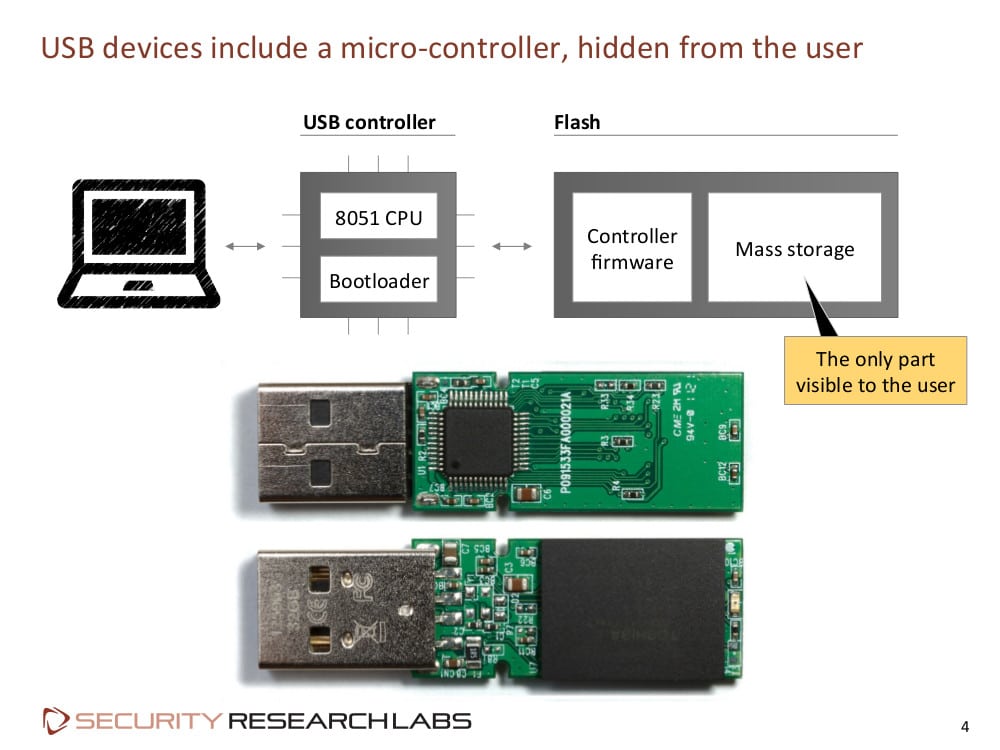
Unpatchable USB Malware Now Open Source | WIRED
Andy Greenberg over at Wired has an interesting piece of news coming out of last week’s Derbycon hacker conference in Louisville, Kentucky. According to Greenberg and Wired, researchers Adam Caudill and Brandon Wilson showed off their own version of Karsten Nohl and Jakob Lell’s BadUSB malware, and that they’d released the code on Github. Their presentation raises the stakes for USB manufacturers to fix the BadUSB problem or leave hundreds of millions of users vulnerable, Greenberg writes. At a presentation at the Black Hat Briefings in August, Nohl and Lell, both of Security Research Labs (SRLabs), showed how the controller chips inside common USB devices can be reprogrammed, allowing USB peripherals to impersonate other kinds of devices. Among other things, Nohl demonstrated how a BadUSB infected device could emulate a USB keyboard, issuing commands to a connected machine using the permissions of the logged-in user. Alternatively, an infected USB could spoof a […]
Infographic: Possible Attacks on The Internet of Things
The folks over at Trend Micro have put together a nice infographic that reminds us that all those smart devices connected to the Internet communicate through some well worn channels, namely: standard communications protocols like Wi-Fi, Ethernet and Bluetooth that connect devices to each other and the global Internet, as well as HTTP that are used to transmit data to and from cloud based resources like management interfaces. Of course those standard protocols also leave IoT devices vulnerable to a wide range of commodity attacks: from brute force password cracking on web based management consoles to Man in the Middle attacks that can sniff out authentication credentials and hijack sessions. Trend’s infographic does a good job of depicting the various layers in the IoT stack and some of the likely attack vectors for each layer. It also gives advice on how to protect yourself (use encryption, patch software vulnerabilities, disable unused ports). Nothing ground breaking […]
You’re Invited: A Conversation on Password Security and Targeted Attacks
A note to Security Ledger readers that I’ll be facilitating a really interesting conversation this afternoon on password (in)security and how weak user authentication can undermine even the best laid security plans. The SANS Webinar, Security for the People: End User Authentication Security on the Internet” kicks off at 3:00 PM Eastern today (12:00 PM Pacific). You can register to join us using this link. My guest is DUO Security researcher Mark Stanislav, a frequent Security Ledger contributor and one of the smartest guys out there when it comes to passwords, authentication and securing the Internet of Things. There’s plenty to talk about: weak authentication schemes are the root cause of any number of prominent breaches – from the recent attacks the Apple iCloud accounts of A-list celebrities, to the breach at retailer Target (reportedly the result of a phishing attack on an HVAC contractor that Target used.) Mark and I […]
Report: Home Depot Fallout Reveals History of Lax Security, Hiring
Its a truism in cyber security that behind every great hack often lies a string of bad decisions and missed opportunities. Its also true that when you dig into the details of damaging cyber incidents, the root causes are personal and psychological as often as they are technical in nature. Organizations -even sophisticated and wealthy organizations – end up making bad decisions for all the wrong reason: failing to properly assess their risk, or pursuing short term savings when long term investment is needed. Home Depot learned via law enforcement that a breach of transaction data exposed as many as 52 million credit card transactions, the largest retail credit card breach to date. But as more comes out about the breach at home improvement giant Home Depot, it starts to look a lot more like the root causes there may have started in the HR department rather than the data center. The […]