In-brief: the Panama-based law firm at the center of a massive data leak said that more than 11 million documents were taken from his firm by “hackers” and defended its reputation and practices.
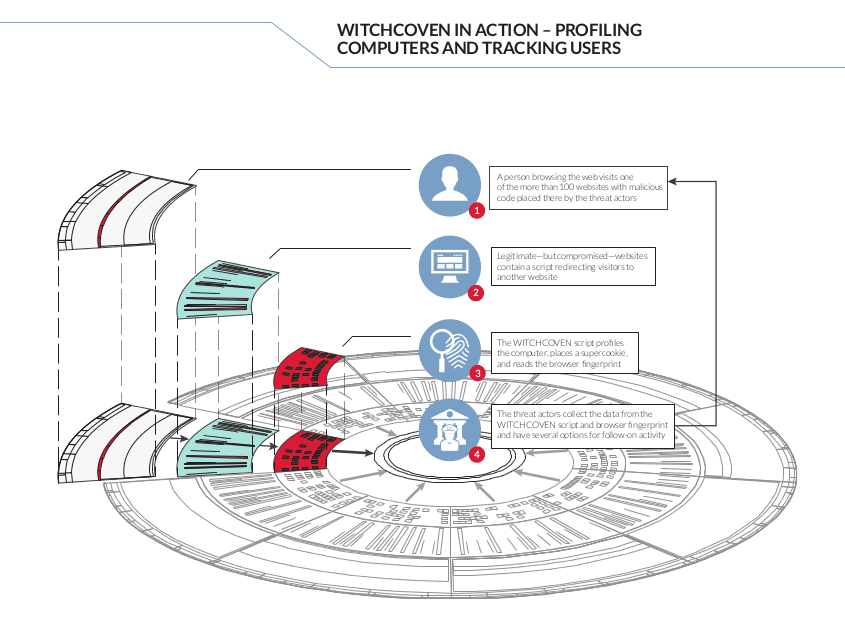
Super Cookies, Web Analytics Behind Malicious Profiling
In-brief: FireEye is warning about a sophisticated campaign of online surveillance that combines web “super cookies” and common analytics software to target individuals with links to international diplomacy, the Russian government and the energy sector.
Iran Games Google’s 2FA in Attacks on EFF, Others
In-brief: Hackers believed to be linked to the government of Iran are using sophisticated attacks on Google’s two-factor authentication technology to break into the e-mail accounts of individuals within the country and in the Iranian diaspora, according to Citizen Lab.
Everything Tastes Better with Bluetooth: Understanding IoT Risk
In-brief: Marc Blackmer of Cisco says that, with so much promise, it can be hard to anticipate how individual or company-wide decisions to embrace the IoT might bear on cyber risk.
Was Malware Behind A Billion Dollar Heist?
In-brief: The New York Times reports on a massive online heist involving more than 100 banks worldwide and losses of between $300 million and $1 billion, according to the security firm Kaspersky Lab.