In-brief: An article on the web site Venturebeat.com makes the case for a Chief Internet of Things Officer to manage adoption of new technologies. But are companies ready for a CIoT?
Big Data
Are Data Lakes A Key To Securing IoT Environments? | Tripwire Blog
Mitch Thomas over at the security firm Tripwire has a good post on “architecting the security of things” that’s worth checking out. As an incumbent security vendor, Tripwire faces the same challenges and problems as other vendors who came of age securing traditional endpoints and enterprise IT environments. Among them: adapting to a nearly limitless population of new endpoints – many of them small, resource constrained embedded systems. As we’ve noted before: many of these systems aren’t capable of the kinds of interrogations (vulnerability- and malware scans just two examples) that many security tools take for granted.
With Multi-Vector Attacks, Quality Threat Intelligence Matters
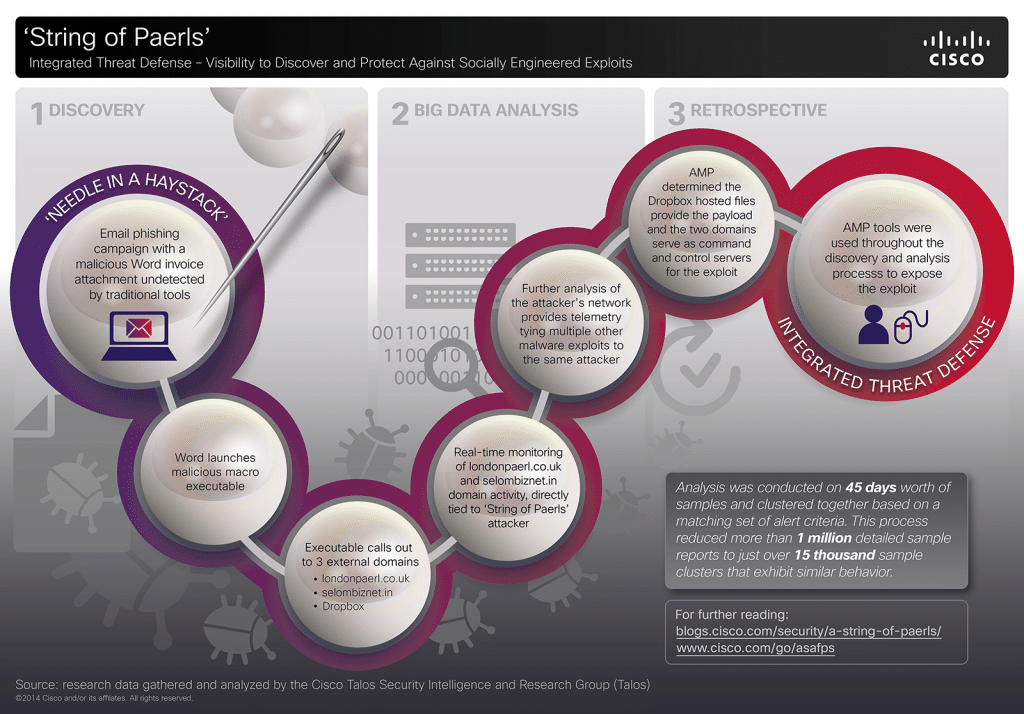
In the last year, the world’s attention has been riveted by a series of high-profile hacks of major corporations in retail, finance and the entertainment industry, among others. Each of these incidents is unique, involving different threat actors and motives. However, each of these attacks is also a sterling example of what we, at Cisco, term “multi-vector attack” that employs a range of technologies, deployed in numerous stages, to penetrate the defenses of the target organization. Here at Cisco, we have studied these attacks in-depth and have identified some commonalities among these multi-vector attack, and useful approaches to combat them. This blog post will discuss some of our findings. About Multi-Vector Attacks Any cyber attack, large or small is born from a weak link in the security chain. These weak links take many forms: poorly configured Web servers, gullible employees or vulnerable-but-common applications like Microsoft Office, Adobe Reader and Java are common examples. Multi-vector attacks […]
Big Data, Security Drive Dell In Post-PC Future
If you consider how the Internet of Things is transforming the technology industry, one of the most interesting and thought-provoking areas to pay attention to is what we might consider technology “majors” – firms like HP and IBM and Cisco that made their mark (and their hundreds of billions) serving the needs of an earlier generation of technology consumers. How these established technology firms are pivoting to address the myriad challenges posed by the “Internet of Things” tells us a lot about how the IoT market is likely to shake out for consumers and – more pressingly- the enterprise.
Convergence of M2M and IoT signals Major Cultural Shift
Required reading for Monday: TechCrunch has a nice little explainer article by @ArtyomAstafurov (of DeviceHive) that talks about the evolution of machine-to-machine (M2M) technologies into the Internet of Things and how the two technology trends are now indistinguishable- and are poised to cause large-scale disruption. To quote Astafurov: “IoT separates itself from M2M not only in the simplicity and quantity of devices involved, but also by how the devices communicate with each other…Whereas M2M tends to rely on point-to-point exchanges between individual devices, IoT communications involve dispersed devices sharing data through a central server, resulting in exponentially more data based on the relationships and patterns that emerge.” And the IoT will drive massive investment in products and technologies that can capture, aggregate and analyze consumer data. This will be akin to the kind of investment corporations put into ERP (enterprise resource planning) tools a decade ago, he says. Though the focus of IoT right […]