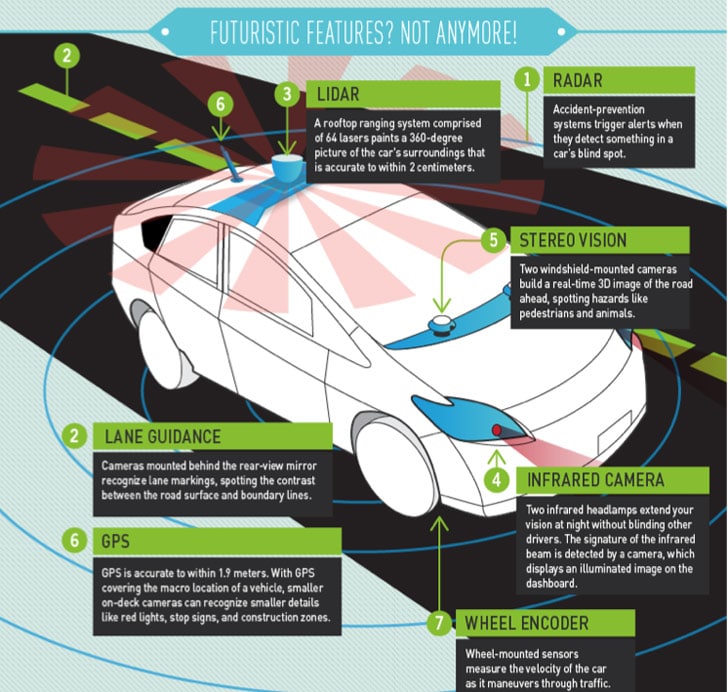
Just a note to our readers that you can listen to a great conversation on hacking automobiles on Airtalk, a National Public Radio call-in talk show that airs on WPCC, Pasadena, California. Interestingly: the other expert guest on the show was none other than Chris Valasek of IOActive, one of the most recognized researchers on security vulnerabilities in modern automobiles. [Read more Security Ledger coverage of Chris Valasek’s research here.] Chris and I spoke with host Larry Mantle about the current state of affairs with regard to car hacking: what is possible (theoretically), what is practical and what are car makers doing about it. Check out our conversation via KPCC’s web site: The next frontier for computer hackers: Your car | AirTalk | 89.3 KPCC.
operating system
Microsoft Issues Critical, Emergency Patch: MS14-068
Microsoft on Tuesday released a critical security patch outside of its normal, monthly software update cycle to fix what it described as a serious, privately reported vulnerability in Microsoft Windows Kerberos Key Distribution Center (KDC). If left unpatched, the security hole could allow an attacker to impersonate any user on a domain, including domain administrators. They could use that access to install programs; view, change or delete data; or create new accounts on any domain-joined system, Microsoft said. The security hole affects a wide range of Windows versions and is rated Critical for all supported editions of Windows Server 2003, Windows Server 2008, Windows Server 2008 R2, Windows Server 2012, and Windows Server 2012 R2, Microsoft said. Kerberos is an encryption technology that is the default authentication method for Windows systems, starting with Windows 2000. The Kerberos Key Distribution Center is a standard network service for issuing temporary session keys to users and computers […]
Whack-A-Bash: New Vulnerabilities add to Patch Confusion
The good news about the rapid, industry response to the revelations about exploitable security holes in GNU Bash (Bourne Again Shell) (aka “Shellshock”) is that Linux users had a fix in hand almost as soon as they became aware of the problem those patches addressed. The bad news about the quick fixes for the two issues, CVE-2014-6271 and CVE-2014-7169, from the likes of Red Hat, Ubuntu, Debian and others is that – in being early- they fail to fix the problems we don’t yet know about. And that’s what we’re seeing in the wake of last week’s storm of patches: a steady drip-drip of disclosures that suggest that Bash may contain other problems worthy of new fixes. Within hours of the disclosure of the first holes, there were problems discovered by Red Hat Product Security researcher Todd Sabin, who found additional “off by one” errors in Bash that were assigned CVE-2014-7186 and CVE-2014-7187 and […]
Samsung Expanding Mobile Management To Court Enterprise
Editor’s Note: this story was updated to note that Centrify is now known as Delinea. PFR Sept. 18, 2022 Apple stole the show this week, unveiling its new, larger iPhones and a smart watch that everyone is just calling iWatch, whether that’s the product’s name or not. But the rush of new products from Cupertino doesn’t change the fact that, behind the scenes, the battle for the hearts and minds of business users (aka “enterprises”) rages on between Apple, Google, Microsoft and Blackberry. iPhone 6 or no, the outcome of that battle is anything but clear. Case in point: Samsung will roll out new features this week for its KNOX-powered Android phones and tablets that are designed to appeal to security and privacy conscious business users. The new KNOX solution offerings, which will become public on Thursday, promise enterprises and government organizations the tools to simplify the implementation of BYOD (or Bring Your Own Device) programs. In […]
Dan Geer’s Other Keynote: Embedded Devices Need A Time To Die
With the Black Hat Conference well under way and DEFCON starting later this week, the security world’s attention will turn to Las Vegas, where some of the cyber security industry’s top researchers and thinkers will be holding court. One of the most anticipated talks is the Black Hat Briefings opening keynote. This year, the honor goes to none other than Dr. Dan Geer, the CISO of In-Q-Tel, the investment arm of the U.S. intelligence sector. Geer’s talk on Wednesday, August 6, 2014 is entitled “Cybersecurity as Realpolitik.” In anticipation of Dr. Geer’s Black Hat, we’re releasing another recent talk he gave: this one a keynote speech at our May, 2014 Security of Things Forum in Cambridge, MA. In this talk, Dan focused on the security of embedded devices and the fast-emerging Internet of Things. (A full transcript of the talk is available here.) “The embedded systems space, already bigger than what is normally thought of as […]