Research from the firm Akamai finds cyber criminals are marrying vulnerable home routers to sophisticated “fast flux” command and control tools to create long-lived, cyber criminal infrastructure.
published research
Report: 1.9b Records Lost in First Half of 2017, topping 2016
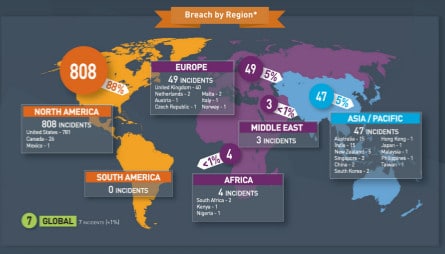
A survey of public data breaches has found a large increase in the number of records that have been stolen, lost or compromised in the first six months of 2017. The firm Gemalto said that the number of records caught up in breaches jumped 164% from the second half of 2016 and the first half 2017 to almost 2 billion lost records. That is more than the total number of records lost in all of 2016. Gemalto said its latest data from the company’s Breach Level Index, a global database of public data breaches, indicates 918 data breaches led to 1.9 billion data records being compromised worldwide in the first half of 2017. Most of the leaked records came from just 22 large data breaches, each involving more than one million compromised records, the company said. How many records? Nobody knows. Even more worrying: of the 918 data breaches, the […]
Inside the Equifax Hack, Facebook’s Problem with Authoritarianism & ASPertise harnesses Asperger’s Syndrome
In-brief: In this week’s podcast, Security Ledger Editor in Chief Paul Roberts talks with noted security researcher Robert “RSnake” Hansen about the data breach at Equifax and why the company’s response to it was so lacking. Also: Chris Sumner of the Online Privacy Foundation talks about why Facebook is a killer app for information operations and we talk to the president of ASPertise: a consulting firm by and of professionals with Aspergers and Autism spectrum disorders.
A Right to Repair the Internet of Things? Spear Phishing Detection and Nonstop Attacks on DVRs
In-brief: In the latest Security Ledger podcast we talk about pending right to repair laws and their impact on the Internet of Things. Also: Facebook’s Internet Defense Prize went to a better method for spear phishing detection. We talk to a member of the winning team. And, Johannes Ullrich of The Internet Storm Center joins us to talk about a study he did to measure the frequency of attacks on a common IoT device: digital video recorders.
The Spectrum of Mobile Risk: Protecting Your Corporate Data
In-brief: organizations need to better understand mobile risks if they want to protect critical data, writes Aaron Cockerill of the firm Lookout.