In-brief: In this video from the Security of Things Forum in September, Scott Tenaglia of Invincea demonstrates vulnerabilities in Belkin’s WeMo family of connected home products.
smart home
Home wireless networks are set for a makeover
In-brief: In our latest Security Ledger podcast, we talk with Luma founder and CEO Paul Judge, a serial entrepreneur (Ciphertrust, Purewire, Pindrop) whose latest venture seeks to bring enterprise-quality wireless to the home market, improving both security and management along the way.
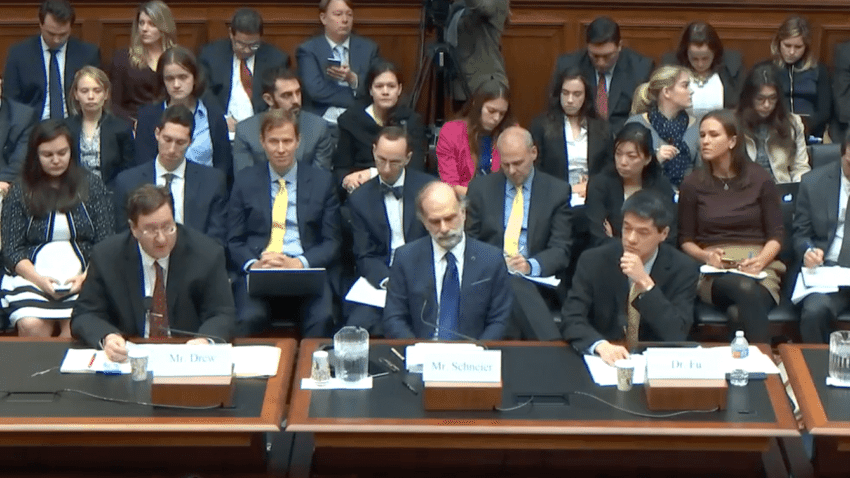
On Capitol Hill: Calls For A Federal Role in Securing World of Dangerous Things
Some of the nation’s top experts on cyber security and the Internet of Things urged Congress to take a more forceful approach to securing a burgeoning population of Internet connected devices before security and quality issues undermine consumer confidence. Members of the House Committee on Energy and Commerce were told in separate testimony that security problems such as the recent denial of service attacks linked to the Mirai botnet will become more common and could threaten the integrity of the Internet and of the nation’s broader economy if left unaddressed. The Committee heard from Dr. Kevin Fu of the University of Michigan, Bruce Schneier of IBM and a fellow at Harvard’s Kennedy School of Government and Dale Drew, the Chief Security Officer of Level3 Communications. All three, to varying degrees, advised a bigger government role in setting standards for devices connected to the Internet. And all three warned that a failure to […]
Survey Sounds More Alarms on Internet of Things in the Enterprise
In-brief: A survey of customer networks by the firm zScaler found that cameras, printers, video recorders and other devices are common – and often easy to snoop on and attack.
Can Low-Power Devices Be Secured? | Semiconductor Engineering
In-brief: Internet of Things will break the traditional perimeter-based model for security, and article at Semiconductor Engineering declares. But are device makers ready to do what’s necessary to build a new generation of secure endpoints that can scale globally?