Ars Technica has an interesting write-up on an apparently successful compromise of Google’s two-factor authentication technology. Though in this case, the culprit wasn’t any system Google deployed or managed, but a gullible customer support representative working for the victim’s cell phone carrier. According to this post over at Facebook-for-hipsters site Ello.co, Grant Blakeman woke up on a recent Saturday morning to find that his Google account had been hijacked – despite the fact that he used Google’s two-factor authentication to protect access to the account. How? Blakeman enlisted the help of none-other than Mat Honan, whose own struggles with account hijacking became the subject of a much-cited Wired feature article. As with Honan, Blakeman’s valuable three-character Instagram account, @gb, appears to have been the lure for hackers. (Honan’s @mat Twitter account was what lured his attackers.) Read “Researchers sidestep Paypal Two-Factor Authentication.” After a conversation with Honan, Blakeman contacted his cell provider and […]
fraud
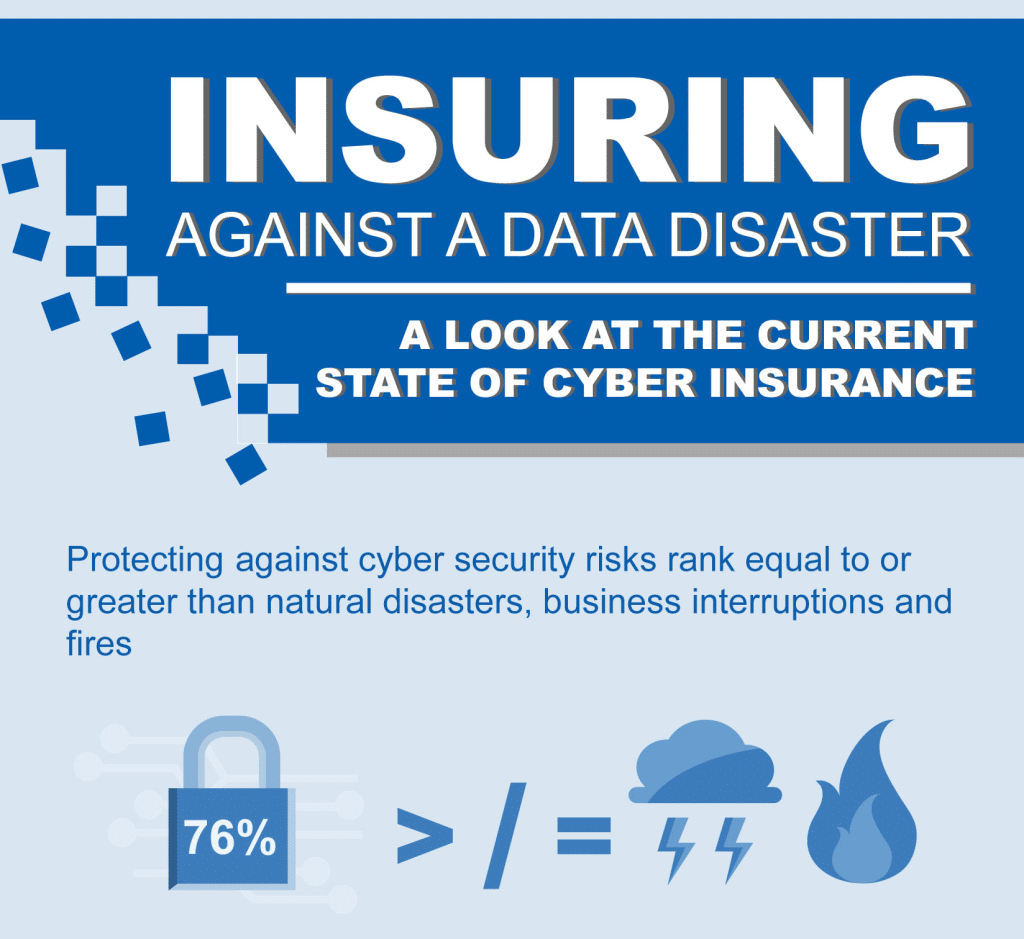
Cyber insurance: Only fools rush in | ITworld
Cyber incidents these days tend to follow a familiar pattern: law enforcement is contacted and will begin criminal investigations. Cyber forensic investigators are hired to piece together what happened and security consultants will analyze and remove the malware from any affected systems. Finally: customers who were affected are notified and – typically -offered free credit monitoring services. All of these services come at a cost, of course, as does the business disruption that results. Current cyber insurance policies are structured to recover some or most of those costs. Now companies – from the Fortune 10 on down – are looking to hedge their online risks with various kinds of business insurance. That demand, in turn, is fueling a rapid expansion of the cyber insurance industry that was little more than a niche offering five years ago. But insurance industry experts and corporate security professionals offer words of advice for companies that think they […]
Is IoT Innovation Outpacing Our Ability To Keep It Safe?
GigaOm has an interesting, high-level piece that looks at the issue of law, liability and the Internet of Things. The article takes off from a discussion at the Download event in New York City earlier this month, wondering whether adoption of Internet of Things technologies like wearables is starting to run far ahead of society’s ability to manage them. Specifically: is the pace of technology innovation outstripping the ability of our legal system to reign in excess and protect public safety and civil liberties? On the list of ‘what-if’s’ are some familiar questions: How to assign liability. (“If one of Google’s automated cars crashes, is it the fault of the driver or Google?”) Read more Security Ledger coverage of Internet of Things here. What responsibility to users have to take advantage of safety features in connected products? (Does a parent’s failure to password-protect a baby monitor change the manufacturer’s liability when and […]
Obama Uses Executive Order To Push Chip and Pin
Add data security to the long list of issues on which U.S. President Barack Obama has resorted to unilateral action in order to push the government forward on a crucial matter. On Friday, President Obama signed an Executive Order directing the government to require the use of so-called “chip and PIN” technology for any newly issued or existing government debit and credit cards. The Order was intended to make the federal government “lead by example in securing transactions and sensitive data,” the White House said in a statement. The new BuySecure Initiative will provide consumers with more tools to secure their financial future by assisting victims of identity theft, improving the Government’s payment security as a customer and a provider, and accelerating the transition to stronger security technologies and the development of next-generation payment security tools. The Order launches a new initiative dubbed “BuySecure” intended to “drive the market towards more secure payment systems” […]
McKinsey: Consumers Want Connected Cars – And Fear Them, Too
The consulting firm McKinsey & Co. has released an interesting report on the future of connected vehicles. But it has some sobering data for car makers: concerns about privacy and the possibility that connected cars could be hacked are major concerns for consumers that could dampen enthusiasm for smart vehicles. The report, “What’s Driving the Connected Car?” finds that connectivity features will be a major driver of car sales in the coming years, with car buyers increasingly accustomed to vehicles that sport sophisticated interactive and networking features. That said: security concerns may hamper the “rapid and broad adoption” of connected vehicle technology. For its report, McKinsey interviewed 2,000 new car buyers in four countries: Brazil, China, Germany and the U.S. The survey found that a quarter of respondents considered connectivity a more important feature than engine power or even fuel efficiency. The firm estimates that connectivity features will become increasingly important selling features […]