One of the most vexing problems that faces IT organizations these days is how to measure their relative risk of being hacked or otherwise attacked. This sounds like pretty dry stuff, but it’s not. Failing to adequately account for your risks and exposure can mean the difference between swatting away an annoying intrusion attempt, and watching as foreign competitors or nation-states siphon off your critical intellectual property, bleeding your company of its competitiveness. But raising the alarm about this is always a tricky matter. Soft pedal it, and nobody takes you seriously. Scream from the rafters and …well…you’re screaming from the rafters. My friend and former colleague Josh Corman, however, found a good metaphor for the whole affair: the ZOMBIE APOCALYPSE. It’s all a bit of fun – though Mr. Corman is dead serious about the zombie stuff. Still, the idea is simple: attacks on your network and those of […]
Veracode
Google Will Use Cash To Clean Up Open Source
The widespread use of vulnerable or buggy third party code is serious problem facing public and private sector organizations, alike. Just this week, for example, The Wall Street Journal reported that an independent audit of Healthcare.gov, the star-crossed Federal Government website that is the primary health exchange in more than 30 states, is choking on poorly integrated or extraneous code that “served no purpose they could identify.” But what happens when the third-party code in question is open source code? Things get more complex. For one thing: open source is the salt and pepper of the software world: a common ingredient in applications of all sorts. And, as security researchers have noted: many of the so-called “smart devices” that are populating the physical world run variants of Linux, the open source operating system. But because those source code repositories are managed cooperatively and collectively by volunteers, security often takes a […]
Health Exchanges Need A Fail Whale
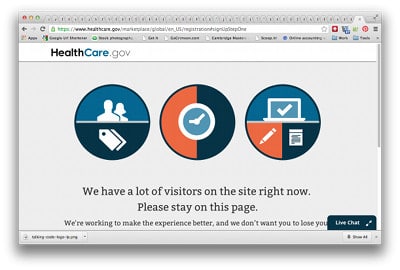
In a blog post on Veracode’s blog today, I write about the problems encountered at government-run online health exchanges that were intended to connect millions to private insurance plans under the Affordable Care Act. The exchanges opened to the public on Tuesday, and they got off to a rocky start, with reports of web sites paralyzed as millions of uninsured Americans logged on to sign up for subsidized health insurance. In some cases, the problems appear to have been caused by “external factors.” New York State’s online health exchange was felled by the weight of more than 10 million requests of dubious origin, The New York Post reported. But other exchanges, including Healthcare.gov the federal government’s main health insurance storefront, which is used by residents or more than half of the states, were victims of their own success: overwhelmed when the doors swung open and millions of eager customers poured […]
Software Safety Should Be Treated Just Like Food Safety. Discuss.
It’s easy to agree with statements like “the food we buy in supermarkets should be safe to eat.” After all, who wants go to bat for shoddy growers pushing contaminated lettuce, or distributors sending out botulinum-laced fish and meats? But what about software safety? Suffice it to say that if people ate software applications instead of, say, cinnamon rolls, they’d be dropping like flies. That’s because the code that powers those applications is often riddled with potentially dangerous insecurities. Unlike the food industry, however, there have been only fitful efforts by government and industry to address what everyone recognizes is a widespread problem. I’ve written elsewhere about the relative lack of a “safety culture” in the software industry compared with industries like civil aviation or even food. (Remember: most of the food recalls and alerts that are issued today are voluntary.) But there’s also a decades-long track record of the government taking […]
Protecting Smart Cars And The Supply Chain From Hackers
One theme that frequently comes up in my conversations with experienced security veterans when we talk about security and “the Internet of Things” is the absence of what might be termed a “security culture.” That’s a hard term to define, but it basically describes a kind of organizational culture that anticipates and guards against online attacks. Certainly companies that have been selling software in any great number for any amount of time have had to develop their own security cultures – think about Microsoft’s transformation following Bill Gates Trustworthy Computing memo, or Adobe’s more recent about-face on product and software security. But that culture is lacking at many of the companies that have traditionally thought of themselves as ‘manufacturers’ – makers of “stuff,” but which now find themselves in the software business. Think General Electric (GE) or – even better – auto makers. A couple of months back, I had […]