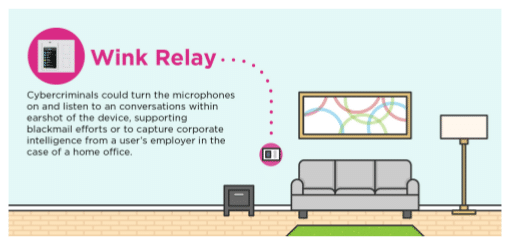
In-brief: A study of common connected home gateways finds lax security that could expose consumers to snooping or even malicious attacks, according to the application security firm Veracode.
Veracode
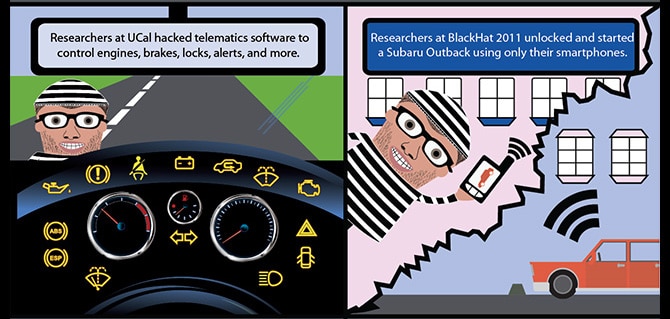
Cyber Lemons: Lawsuit alleges Hackable Cars Pose Risks to Consumers
In-brief: A lawsuit filed in California charges U.S. automakers with endangering their customers by failing to protect ‘connected vehicle’ features from cyber attack.
Strategies for Securing Agile Development: An Online Conversation
There’s no question that agile development methods, which emphasize collaboration and shorter, iterative development cycles, are ascendant. Many factors contribute to agile’s growing popularity, from constrained budgets to increased user demands for features and accountability. Though traditionally associated with small and nimble software and services startups, agile methodology has been embraced by organizations across industry verticals – many (like John Deere) whose name doesn’t scream “app store” or “Silicon Valley Startup.” But if agile is here to stay, a nagging question is how to pivot to agile’s fast-paced and iterative release schedules without skimping on important areas like code security. After all, the conventional wisdom is that security slows things down: imposing time- and labor intensive code audits and testing on the otherwise results-driven development cycle. Fortunately, agile and secure development aren’t mutually exclusive. Tomorrow (Thursday), the Security Ledger and Veracode will collaborate on a Hangout and discussion of how to build, automate and deliver secure software using the agile […]
Cyber Insurance Is Sexy
So bland is the insurance business perceived to be, that it’s the stuff of Hollywood comedy. In the 2004 film Along Came Polly, Ben Stiller played a skittish, risk averse insurance adjuster with actuarial data on bathroom hygiene at his fingertips (no pun). Woody Allen famously depicts his hapless criminal Virgil Starkwell locked in solitary confinement with an eager insurance salesman in the 1969 mocumentary Take the Money and Run. Cruel and unusual punishment, indeed. Boring though they may be, insurance markets are incredibly important in helping society manage risks of all sorts. Insurance markets also have a funny way of shaping behavior – both personal and commercial – in ways that serve the public interest. Take the response to Hurricane Sandy as just one example. Law makers in Washington D.C. may never agree on whether that storm was a product of a warming climate. In fact, they may debate the […]
Is It Time For Customs To Inspect Software? | Veracode Blog
If you want to import beef, eggs or chicken into the U.S., you need to get your cargo past inspectors from the U.S. Department of Agriculture. Not so hardware and software imported into the U.S. and sold to domestic corporations. But a spate of stories about products shipping with malicious software raises the question: is it time for random audits to expose compromised supply chains? Concerns about ‘certified, pre-pwned’ hardware and software are nothing new. In fact, they’ve permeated the board rooms of technology and defense firms, as well as the halls of power in Washington, D.C. for years. The U.S. Congress conducted a high profile investigation of Chinese networking equipment maker ZTE in 2012 with the sole purpose of exploring links between the company and The People’s Liberation Army, and (unfounded) allegations that products sold by the companies were pre-loaded with spyware. Of course, now we know that such […]