Researchers have found an unsecured Microsoft-hosted cloud database that holds personal information from 80 million U.S. households, exposing sensitive data and putting people at risk for identity theft, ransomware and other cybercrimes.
Security researchers and known “hactivists” Ran Locar and Noam Rotem from VPN Mentor discovered the 24-gigabyte database, which includes information such as the number of people living in each household with those individuals’ full names, marital status, income bracket and more, they said in a blog post. The data breach affects about 65 percent of U.S. households and researchers have no idea who owns it, they said.
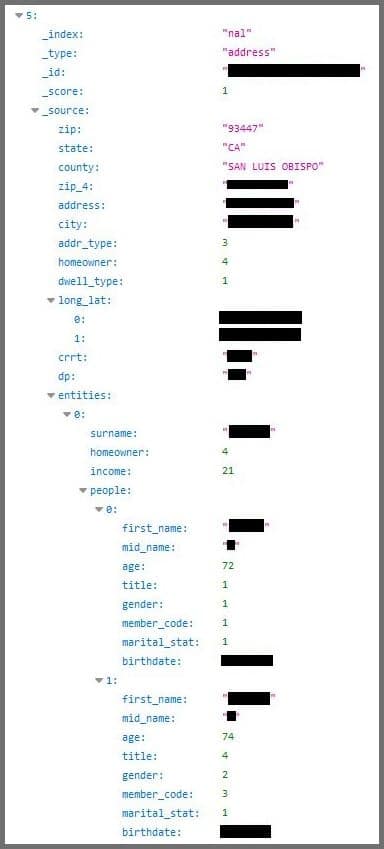
The information held by the database, which is hosted on a Microsoft cloud server, appears census-like, listing data by household rather than by individual person. The types of information includes the following: full names of persons in the household, including first, last and middle initial; their ages and dates of birth; full addresses, including street addresses, cities, counties, states, and ZIP codes; and exact longitude and latitude of the household.
Other information that appears coded in the database but can be ascertained are the gender, marital status, income and homeowner status of those living in a household, as well as dwelling type of the household, researchers said.
Calling the data breach a “goldmine for identity thieves and other hackers,” Locar and Rotem said they believe it’s the first time a breach of this size has included people’s names, addresses and income. They said the personal nature of the data can be used by cybercriminals in various ways, including by targeting people who appear vulnerable with phishing scams and other types of criminal e-mail campaigns.
Good guys prevail–this time
Indeed, “it is very unsettling to see so much sensitive data exposed to anyone with a computer and an Internet connection,” said Mounir Hahad, head of Juniper Threat Labs at Juniper Networks. “There are several services that continuously scan the Internet these days, so it takes very little time for anything unprotected on the Internet to be discovered. On a good day, the exposure is detected by a white-hat researcher that alerts the owner, but on other days, threat actors do since they have access to the same capabilities as the good guys.”
However, John Gunn, chief marketing officer of digital security firm OneSpan, was unfazed by the type of data exposed in the risk. He said the breach merely shows the “poor security practices” of the owner and does not put anyone at risk, since the data by its nature would “have very limited value on the dark web.”
“This is not a goldmine for identity thieves, or even of significant note,” he said. “It does not contains any payment-card information, no social security numbers, no passwords, not even any email addresses. This is the type of information that countless marketers have been tracking and using for decades and is readily available.”
No matter, it was the “good guys” who discovered the data breach this time. VPN Mentor researchers said they found the database as part of a huge Web-mapping project in which they are currently engaged. In this project, they use port scanning to examine known IP blocks, which reveals open holes in Web systems. Once those holes are exposed, researchers examine them for weaknesses and data leaks.
Typically researchers said they alert the owner when they come across an unprotected database like this, they said. The trouble is, this time, they can’t, since it’s still unclear who the unsecured database belongs to.
“It’s hosted on a cloud server, which means the IP address associated with it is not necessarily connected to its owner,” they explained in their post. Moreover, the sheer breadth of data makes its “almost impossible” to narrow down the owner–except for a possible clue that most of the people listed in the database were over the age of 40, researchers said.
Because of their inability to identify the owner, the VPN Mentor team is seeking public help in finding the owner, asking anyone with a possible lead to send an email to info@vpnmentor.com.
In the meantime, Microsoft–alerted to the situation by the VPN Mentor post–took the server hosting the database offline. Not long after, the entire database was removed from the public cloud, researchers confirmed late Tuesday. Still, the identity of its owner remains a mystery.
Cloud security remains complex
VPN Mentor researchers didn’t speculate how a database of this size could be left so exposed, though they acknowledged data breaches themselves are fairly common. However, other security experts had strong opinions, with several agreeing that the exposure likely was due to a persistent lack of understanding about how to secure cloud-based architecture.
Willy Leichter, vice president of marketing for application security vendor Virsec, said that the cloud inherently makes it easier for security blunders like this to happen.
“Any IT person with a credit card can turn on a server or database in the cloud with dozens of different services,” he said. “Unfortunately, for many cloud services, security is not turned on by default, and a casual user can easily expose large amounts of data.”
Another expert agreed, noting that the data breach exposes the two extremes of moving data to the cloud, which he called its “beauty” and “ugliness.”
“The beauty of the cloud is that you can be more agile, more responsive to the business, accessing the applications and services you need ‘on demand,’ said Matt Keil, director of product marketing for Cequence Security. “No longer do you need to go through channels–working with IT and purchasing–to get a server and a license.”
This, however, is part of the “ugliness” of the cloud, he said, because “configuring a cloud service takes time and an understanding of what you are doing.” Due to this increased complexity of security, Keil echoed Leichter’s sentiment that “it’s easy to make a mistake.”
“I liken it to configuring security on your new mobile device, with many steps to walk through to make sure you have a working configuration,” Keil said. “And you need to walk through each of those steps for every cloud service in use.”

